Program white list generation method and device and program updating method and device
A program update and whitelist technology, applied in the field of network security, can solve problems such as lax update program control, update package security verification or verification, etc., to achieve the effect of software security update, ensure security, and avoid spreading
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
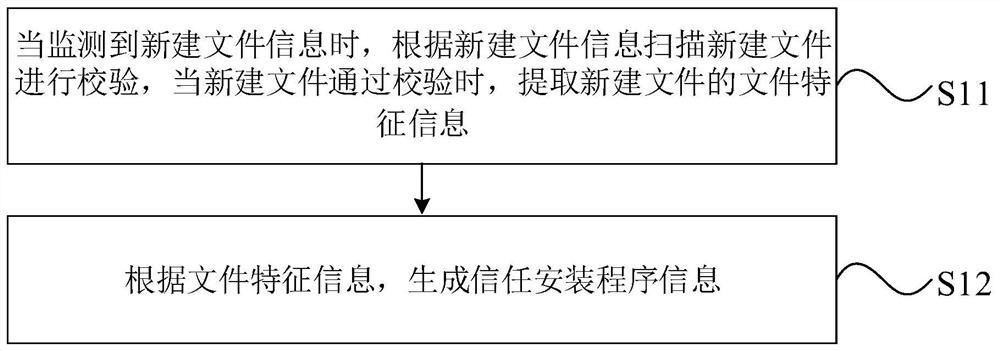
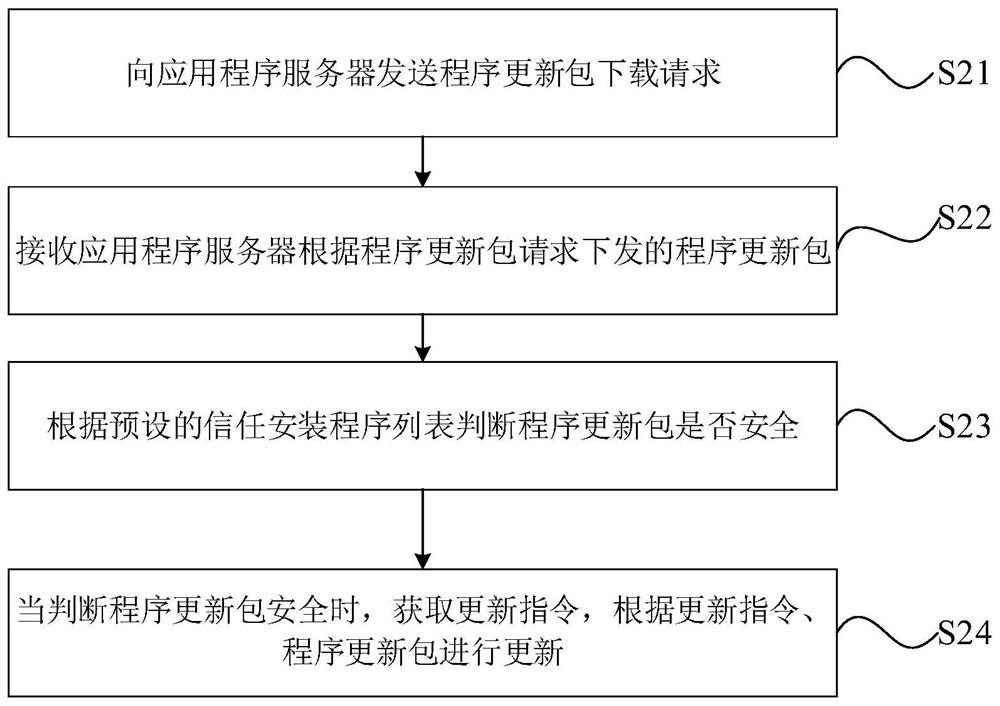
[0052] As an optional implementation manner of the present invention, the program updating method further includes:
[0053] Generate an updated program according to the update instruction and the program update package, and determine the hash value of the updated program; store the updated program in a preset white list library according to the hash value.
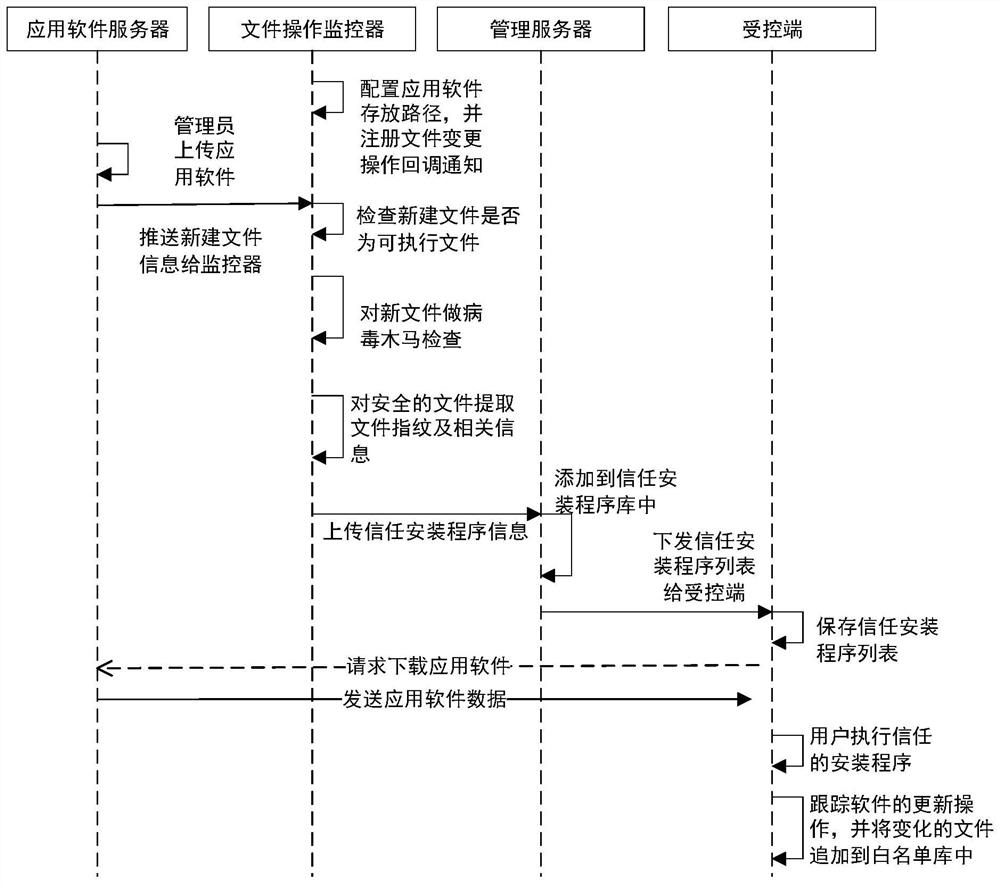
[0054] Such as image 3 As shown, the following describes in detail the implementation process of the method for generating the program whitelist and the method for updating the program in the above-mentioned embodiment in combination with a schematic diagram of a system. That is to say, the above-mentioned method can be applied to such image 3in the system shown. Specifically, the system includes: an application server, a file operation monitoring component, a management server, and a controlled host. The application server includes a file operation monitoring component.
[0055] The file monitoring component is used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com