A method of establishing risk assessment level
A risk assessment and risk assessment model technology, applied in the field of risk monitoring, can solve the problem of not doing enterprise risk information risk classification, and achieve the effect of facilitating the exploration of customer value, improving accuracy, and reducing interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
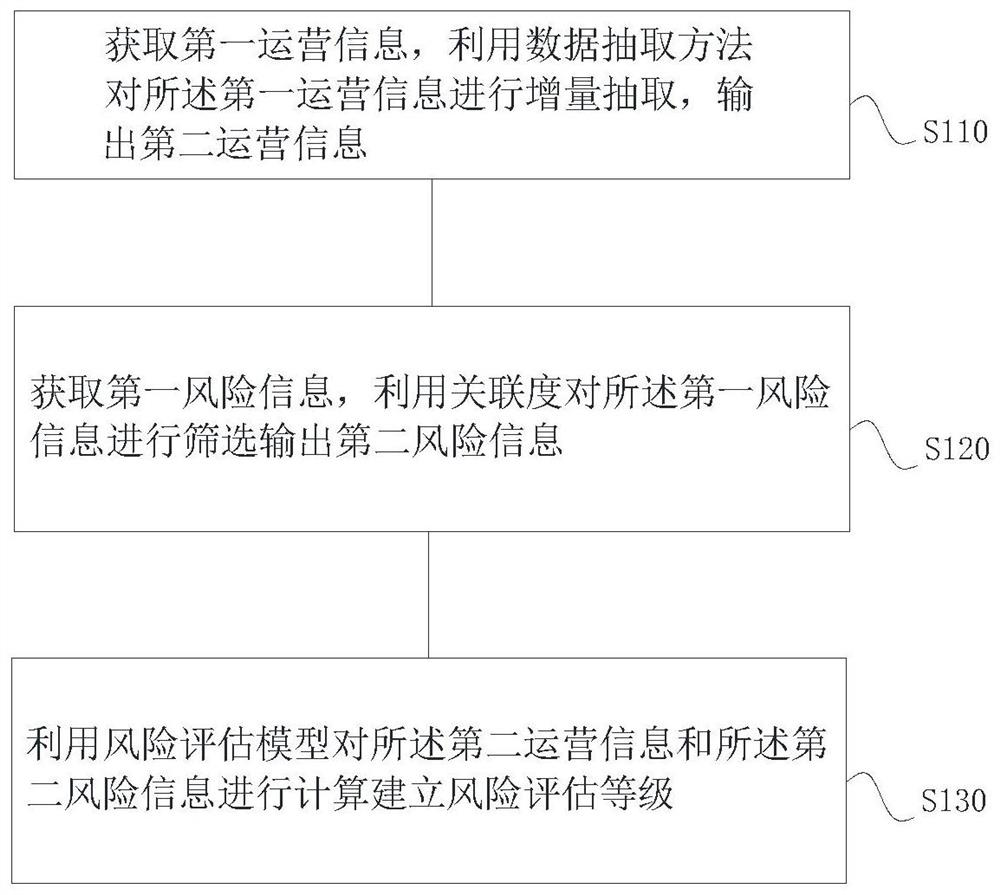
[0053] Such as figure 1 As shown, a method for establishing a risk assessment level includes the following steps:
[0054] S110. Acquire first operation information, incrementally extract the first operation information by using a data extraction method, and output second operation information;
[0055] S120. Acquire first risk information, filter the first risk information by using the degree of relevance, and output second risk information;
[0056] S130. Use a risk assessment model to calculate the second operation information and the second risk information to establish a risk assessment level.
[0057]According to Embodiment 1, it can be seen that the resource allocation mechanism list is sent to the ERP system (enterprise resource planning system), and the first operation information is obtained. The first operation information includes supplier contract execution, price stability, and stability of the top five suppliers. ; Customer accounts receivable turnover, revenu...
Embodiment 2
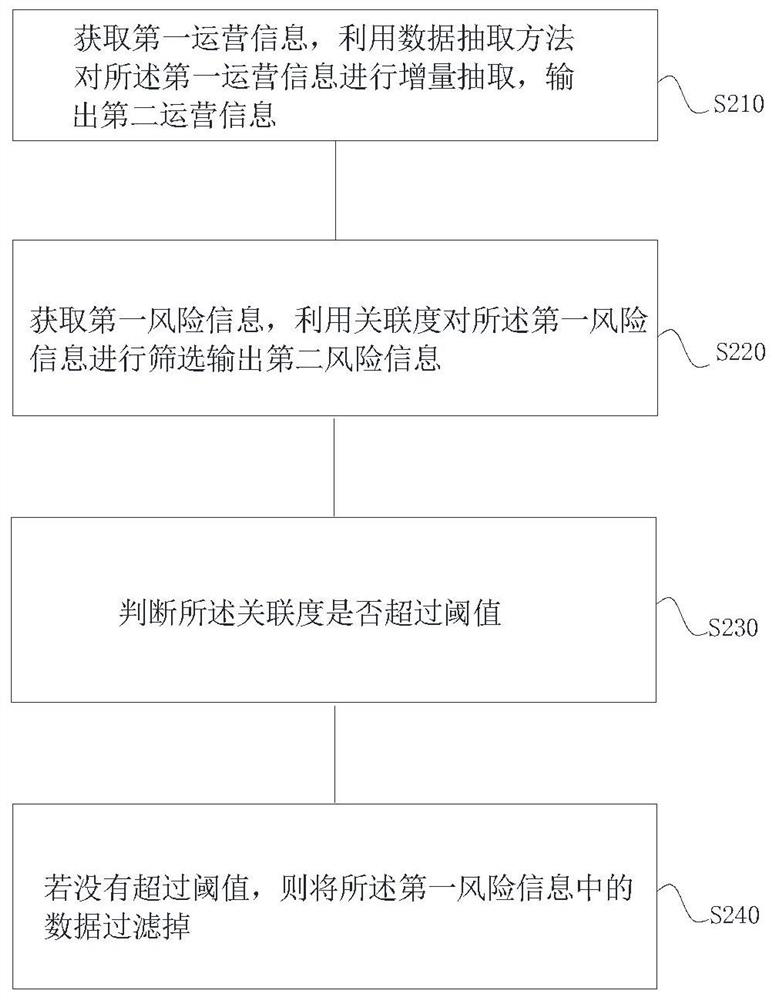
[0059] Such as figure 2 As shown, a method for establishing a risk assessment level, including:
[0060] S210. Acquire first operation information, incrementally extract the first operation information by using a data extraction method, and output second operation information;
[0061] S220. Acquire first risk information, filter the first risk information by using the degree of relevance, and output second risk information;
[0062] S230. Determine whether the degree of association exceeds a threshold;
[0063] S240. If the threshold is not exceeded, filter out the data in the first risk information.
[0064] According to Embodiment 2, it can be seen that the first risk information obtained from the third-party platform and the list of resource allocation mechanisms, that is, the list of enterprises, are used to determine the degree of correlation, and the first risk information with a low degree of correlation is filtered out. The associated news is filtered out, and oth...
Embodiment 3
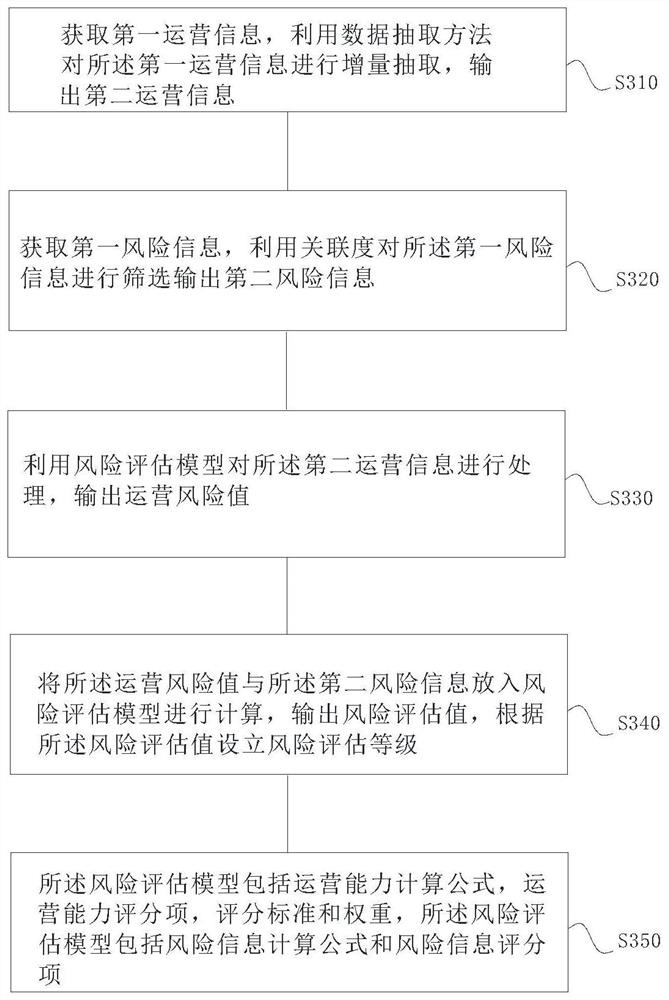
[0066] Such as image 3 As shown, a method for establishing a risk assessment level, including:
[0067] S310. Acquire first operation information, incrementally extract the first operation information by using a data extraction method, and output second operation information;
[0068] S320. Acquire first risk information, filter the first risk information by using the degree of relevance, and output second risk information;
[0069] S330. Use a risk assessment model to process the second operation information, and output an operation risk value;
[0070] S340. Put the operation risk value and the second risk information into a risk assessment model for calculation, output a risk assessment value, and establish a risk assessment level according to the risk assessment value;
[0071] S350. The risk assessment model includes an operation capability calculation formula, an operation capability scoring item, a scoring standard and a weight, and the risk assessment model includes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com