Network security policy optimization method
A technology of network security and optimization method, applied in the field of network information security, can solve problems such as business importance screening, achieve the effect of reasonable priority and ensure reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] The following uses two firewalls to illustrate, and the scenario of multiple firewalls can be extended.
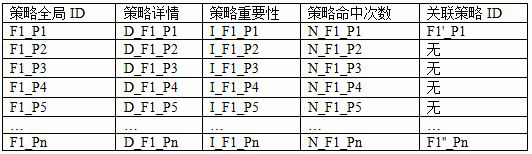
[0056]Assume that the network area under the jurisdiction of firewall F1 is 1.1.0.0 / 16, and the list of network security policies on it is as follows:
[0057]
[0058] The network area under the jurisdiction of firewall F2 is 1.2.0.0 / 16, and the list of network security policies on it is as follows:
[0059]
[0060] The smaller the policy priority, the higher the priority.
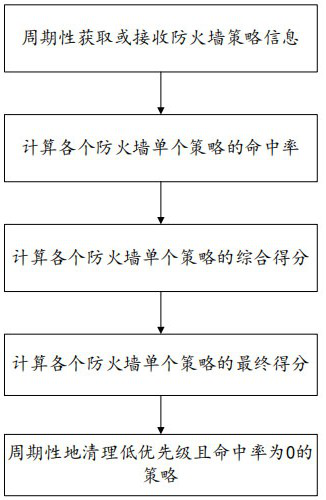
[0061] The following steps are performed periodically, and the specific period can be adjusted according to the actual application scenario.
[0062] Step 1. The network security policy optimization system obtains the network security policy information on it by calling the api interface of the firewall or pushes it to the network security policy optimization system by sending syslog from the firewall, and obtains the following list after preprocessing:
[0063]
[0064]
[0065]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com