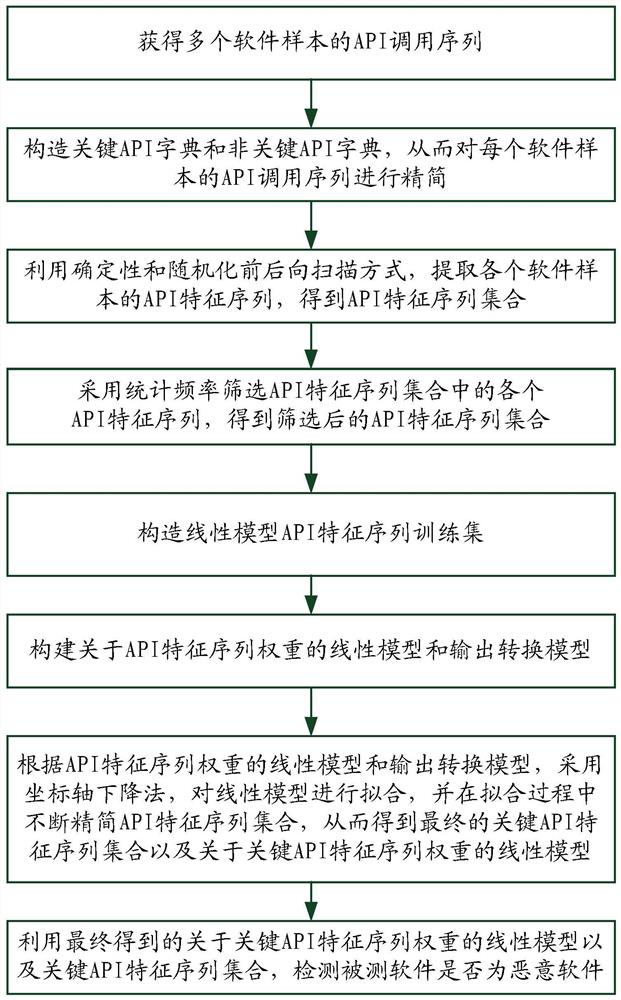
Malicious software detection method based on feature sequence mining and simplification
A feature sequence, malware technology, applied in special data processing applications, complex mathematical operations, instruments, etc., can solve problems such as reducing the accuracy of malware detection and classification, deformation or junk code insertion, and inability to effectively identify malware.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0277] The experimental samples come from the data set used in a security algorithm competition, including 7 typical types of malware samples and normal software samples. Among them, the 7 types of malware samples are: ransomware software (98 samples), mining software (107 samples), DDOS Trojan software (185 samples), worm software (95 samples), infectious virus software (221 samples) , backdoor and Trojan software (164). The normal software samples used in the experiment are software files (2000) extracted from software packages such as operating system Linux, windows and virtual machine software VMware.
[0278] (1) Step 1 is implemented, and the API call sequence of each software sample is obtained by using sandbox technology. Table 1 shows the statistical data of the API call sequence obtained for each software sample.
[0279] Table 1
[0280] Average length of API call sequence Ransomware 136765 mining software 2785781 DDOS Trojan software...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com