Key negotiation method and system
A technology of key agreement and session key, which is applied in the field of information security, can solve problems such as the inability to predetermine the shared key of the result, hidden dangers of the key agreement method, and hidden dangers of the security system, so as to prevent anti-replay attacks and improve Safety, the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
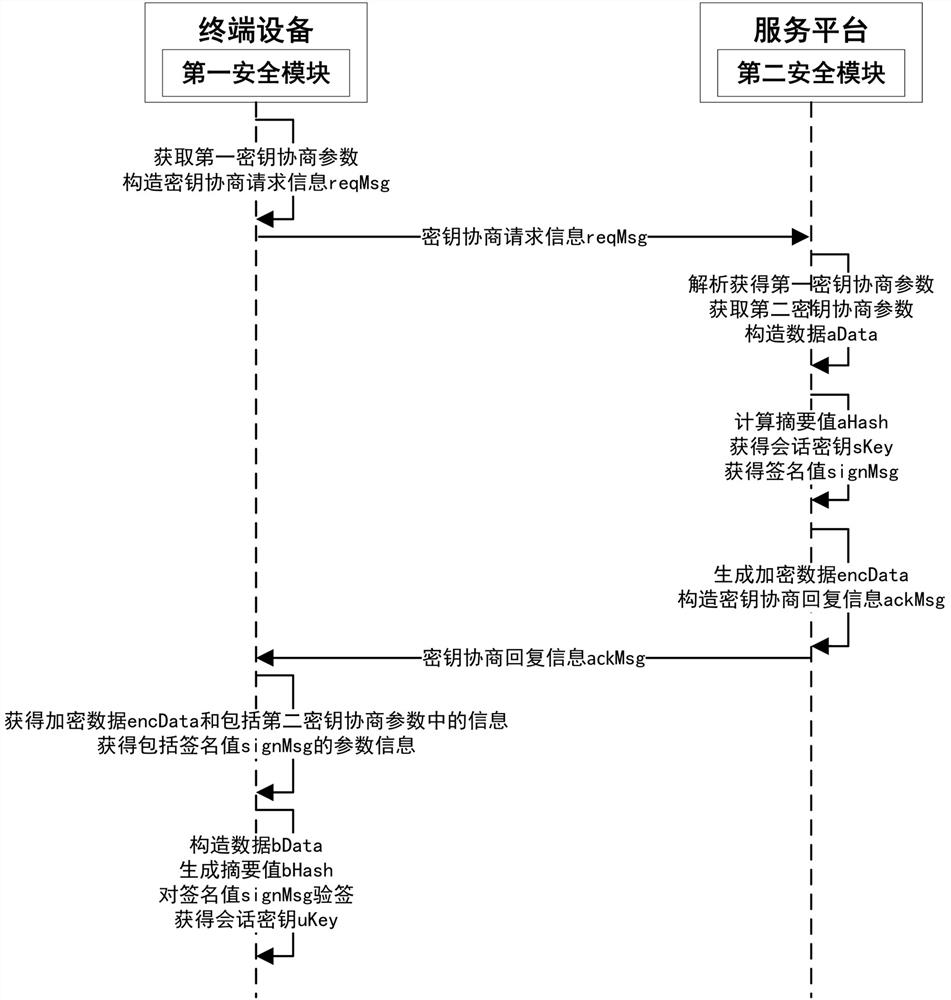
[0053] like figure 1 As shown, this embodiment proposes a key agreement method, including:
[0054] S1. The terminal device obtains a first key negotiation parameter, and constructs the first key negotiation parameter into key negotiation request information reqMsg and sends it to the service platform;
[0055] S2. The service platform acquires the second key negotiation parameter, and constructs the second key negotiation parameter and the first key negotiation parameter into data aData, where the first key negotiation parameter is the pair of the service platform The key agreement request information reqMsg is obtained after parsing;
[0056] S3, the service platform performs digest calculation on the data aData to generate a digest value aHash, and after obtaining the session key sKey according to the digest value aHash, signs the digest value aHash to obtain a signature value signMsg;
[0057] S4. The service platform encrypts the parameter information including the sign...
Embodiment 2
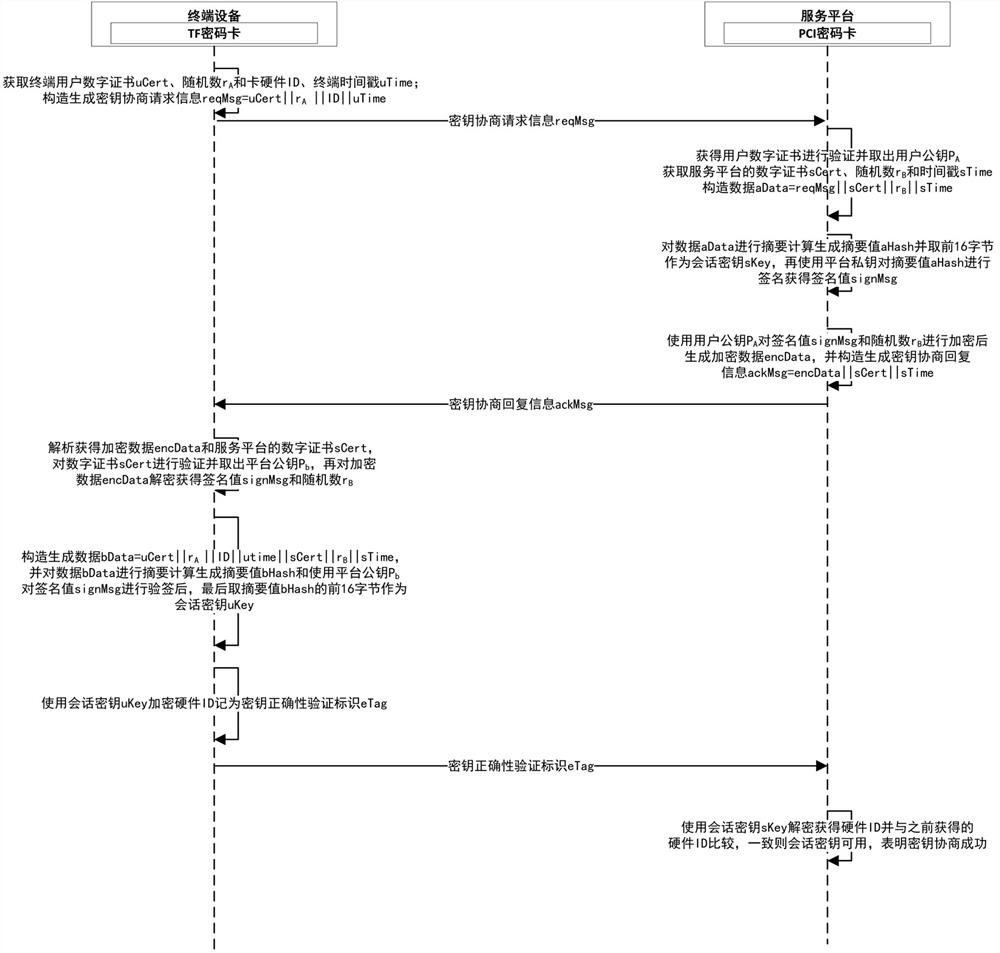
[0083] like figure 2 As shown, this embodiment provides a key negotiation system, including a terminal device and a service platform for performing key negotiation, and when the key negotiation is specifically implemented, the first security module set in the terminal device is a TF password card, The second security module set in the service platform is a PCI password card; the complete process of key negotiation between the terminal device and the service platform is as follows:
[0084] When generating the key agreement request information reqMsg, the specific work of the terminal device is as follows:
[0085] A1: Call the TF password card interface to read the end user digital certificate uCert;
[0086] A2: Call the random number generator in the TF password card to generate a random number r A ∈ [1, n-1];
[0087] A3: Call the TF password card to read the security chip hardware ID;
[0088] A4: Splicing uCert||r A ||ID||uTime (terminal timestamp), recorded as the...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap