An implementation method of opcua protocol supporting mimic system
A technology of mimicking systems and implementation methods, applied in the field of network communication, can solve the problems of complex network functions, difficult for attackers to observe and predict, and complex computing functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
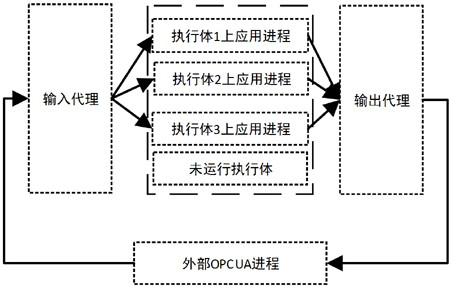
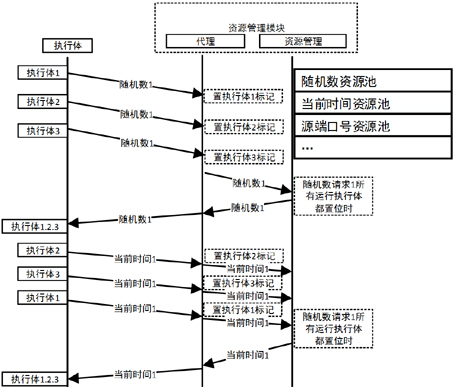
[0029] An implementation method of an OPCUA protocol supporting mimic system of the present invention mainly includes a unified resource management module, an OPCUA state synchronization module and an OPCUA output agent module. The OPCUA protocol is applied in the form of an OPCUA process in the mimic system.
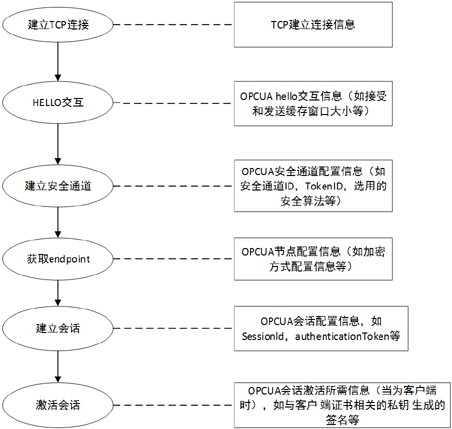
[0030] Such as figure 2 As shown, the OPCUA process includes six states: establishing a TCP connection, HELLO interaction, establishing a secure channel, obtaining an endpoint, establishing a session, and activating a session. Each state corresponds to different configuration information. Among them, the configuration information corresponding to the establishment of the TCP connection state mainly includes the information of the TCP three-way handshake, such as the sliding window size, random number, etc.; the configuration information corresponding to the HELLO interaction state mainly includes the value of the interactive sending and receiving data cache size; the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com