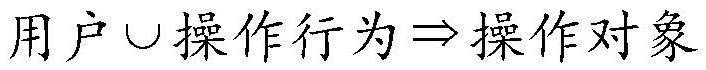Database security detection method and system based on user behavior rules
A technology of security detection and database, which is applied in the field of database security detection, can solve problems such as the influence of network facilities, and achieve the effect of easy filtering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] see figure 1 , the present embodiment provides a method for detecting database security based on user behavior rules, the method comprising the following steps:
[0038] Step 101: Obtain the normal SQL statement submitted by the user to the database.
[0039] Step 102: Split the normal SQL statement into user operation behavior vectors. In this embodiment, the user operation behavior vector includes but not limited to three elements: user name, operation behavior and operation object. It should be noted that in a database application, a SQL statement may contain many different operations, for example, "DELETE FROM table1 WHERE NOTEXISTS(SELECT*FROM table2 WHERE table1.d1=table2.d1)" contains both DELETE and SELECT. Operation types, where DELETE corresponds to the operation table table1, and SELECT corresponds to the operation table table2. Therefore, the SQL statement can be split into 1: , 2: .
[0040] Step 103: Use the set of user operation behavior vectors as a d...
Embodiment 2
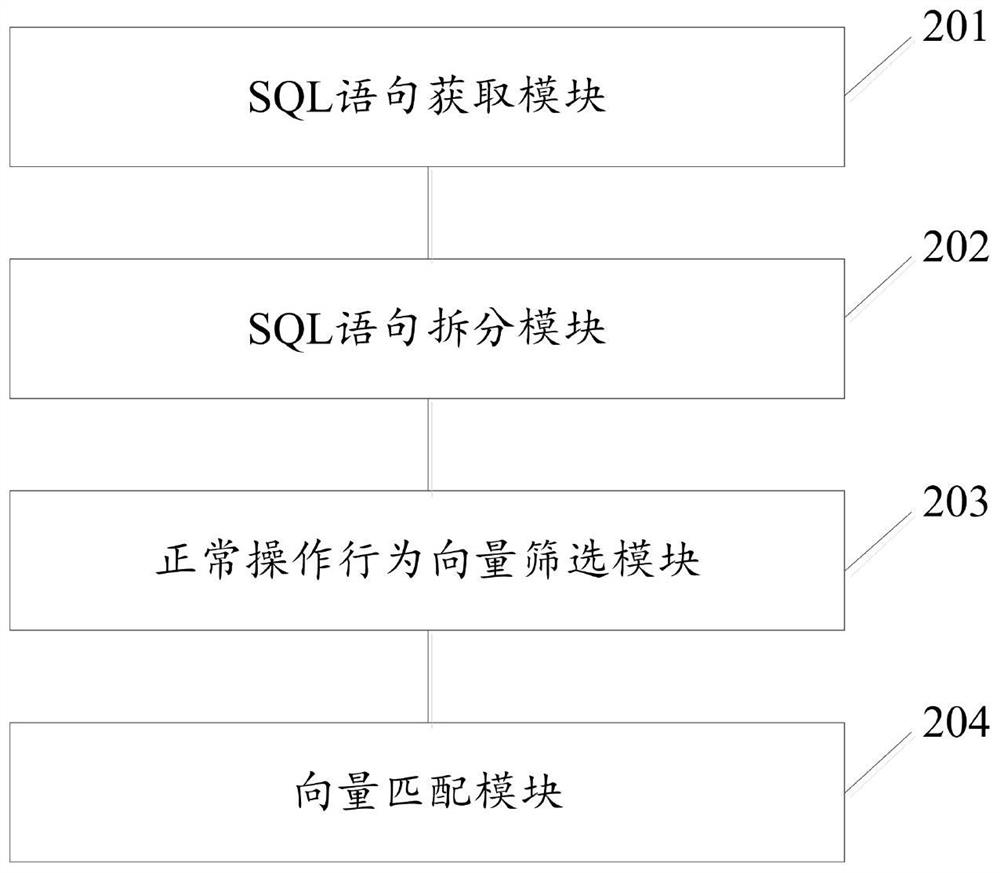
[0075] see figure 2 , the present embodiment provides a database security detection system based on user behavior rules, the system includes:
[0076] The SQL statement acquisition module 201 is used to acquire the normal SQL statement submitted by the user to the database and acquire the SQL statement to be detected;
[0077] The SQL statement splitting module 202 is used for splitting the normal SQL statement into user operation behavior vectors and for splitting the SQL statement to be detected into user operation behavior vectors to be detected, and the user operation behavior vector includes user name, operation behavior and operation object;
[0078] The normal operation behavior vector screening module 203 is used to use the set of user operation behavior vectors as a data set, use the maximum confidence as a correlation metric, and use the Apriori algorithm to screen the user operation behavior vectors in the data set that are greater than the correlation threshold, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com