Electric power communication network vulnerability evaluation method and system based on complex system theory
A power communication network and complex system technology, applied in the field of distribution network optimization operation, can solve problems such as difficult to obtain communication business operation mode, achieve the effect of improving reliability and stability, and preventing failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
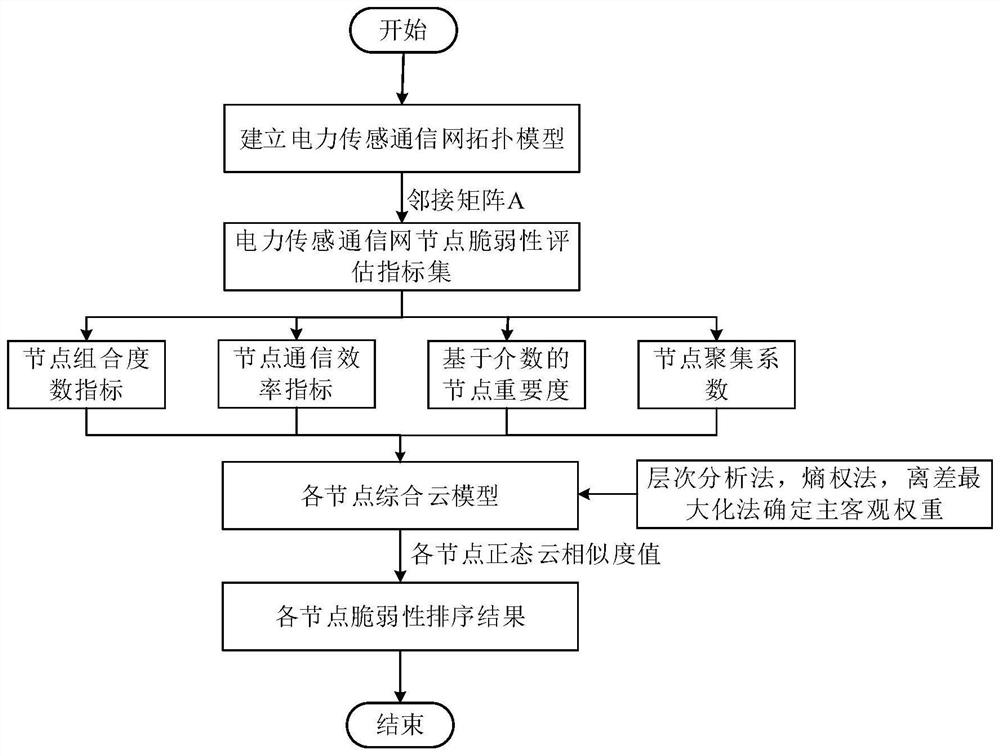
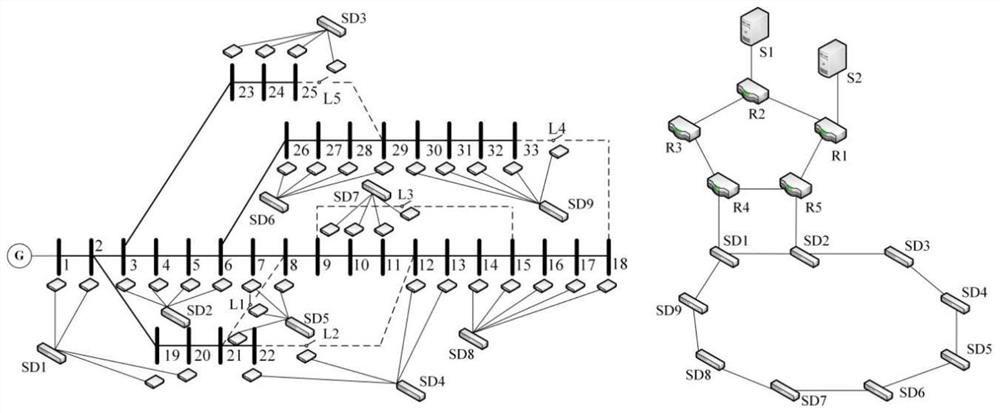
[0106] Such as figure 2 As shown, the power sensor communication network model is the object. The model is based on IEEE-33 nodes, and the communication systems of each plant station and dispatch center are equivalent to the same node. The communication lines between sites are the edges of the communication network, and the differences between the communication lines are ignored, and the communication lines are considered to be bidirectional, that is, all edges are considered undirected. Merge multiple lines of communication in the same direction to eliminate multiple edges and self-loops. The control, monitoring and protection of the power sensor communication network are all implemented by the IED unit, and communicate with the server and the master station control center through industrial Ethernet and SDH, and send all the data to the master station server. Carry out according to each step of above-mentioned method successively.
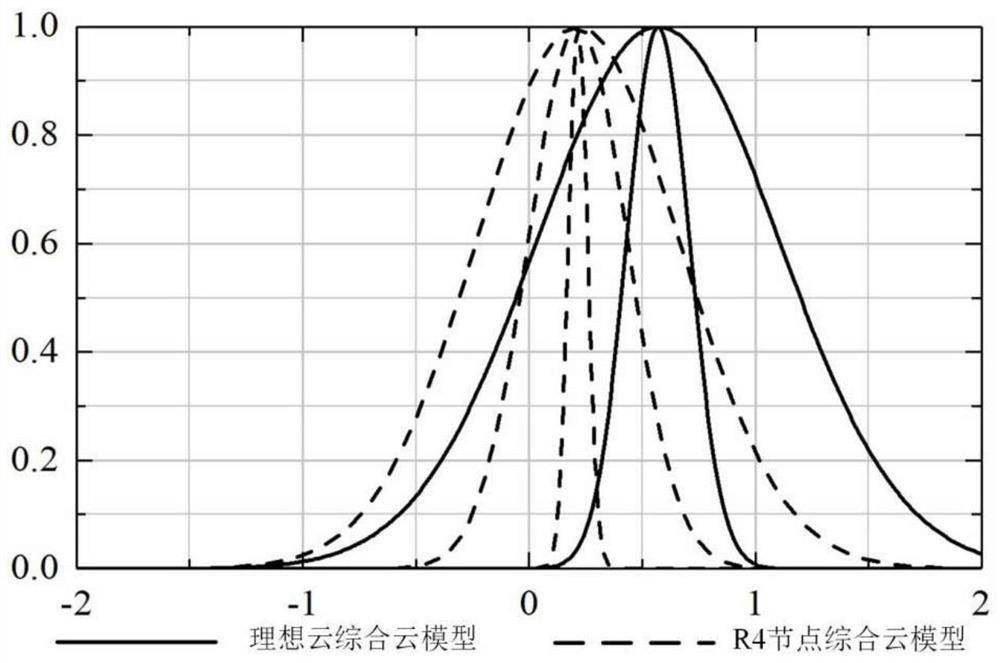
[0107] Table 1 shows the index scores o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com