Attribute-based access control method with anonymous access capability
An access control and access capability technology, applied in the information field, can solve problems such as privacy leakage, achieve the effect of protecting privacy and improving decision-making efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
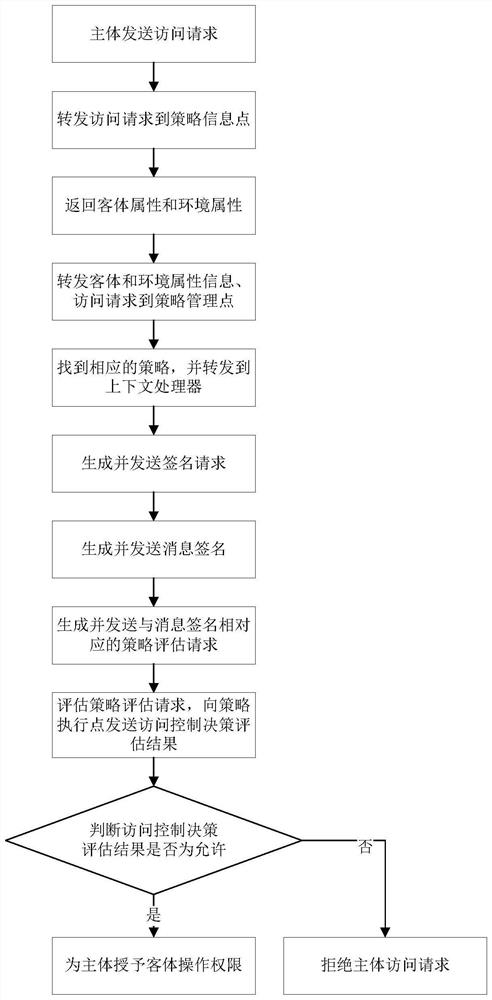
[0028] In order to better describe the implementation process of the present invention, the access control flow is divided into three parts. Among them, the first part is system initialization, which provides guarantee for the security of information released in the system during the subject’s anonymous access process; the second part is subject registration, which issues corresponding subject attribute certificates for subjects participating in the subject’s anonymous access process; the third part is this The subject anonymous access described in the method of the invention, usually, the method of the invention is carried out on the basis of the above two parts.
[0029] The specific steps of the first part of system initialization are as follows.
[0030] The key distribution center runs the signature HABS based on the homomorphic attribute to generate the public key and private key pair of the attribute authority, and distributes the private key to the attribute authority....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com