A graph-based interactive feature extraction method for encrypted Internet traffic
A feature extraction and Internet technology, applied in the direction of neural architecture, biological neural network models, instruments, etc., can solve the problems of small distinction, large quantity, high computational complexity, etc., and achieve the effect of low false alarm rate and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
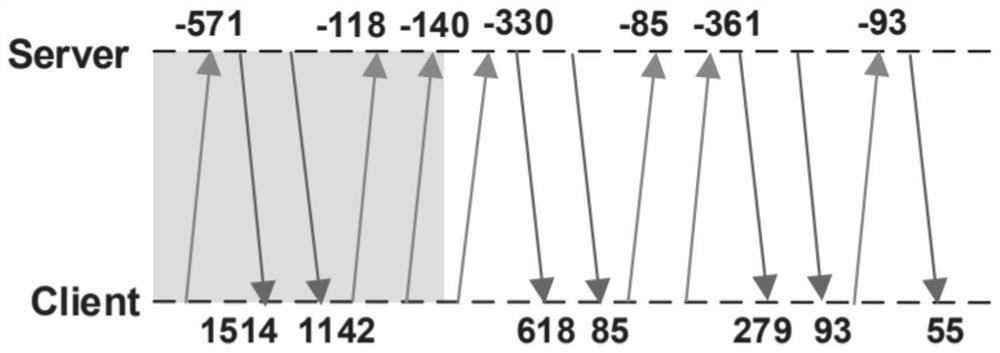
[0032] This embodiment is based on the graph-structured encrypted traffic feature extraction performed in steps 1 to 7. figure 1 It is the data packet interaction process between the client and the server. The length of the uplink data packet is set to negative, and the length of the downlink data packet is set to positive. The gray and white blocks represent the handshake protocol and record protocol in the SSL / TLS protocol respectively.
[0033] Step 1: According to network encryption flow P=(-571, 1514, 1142, -118, -140, -330, 618, 85, -85, -361, 279, 93, -93, 55).
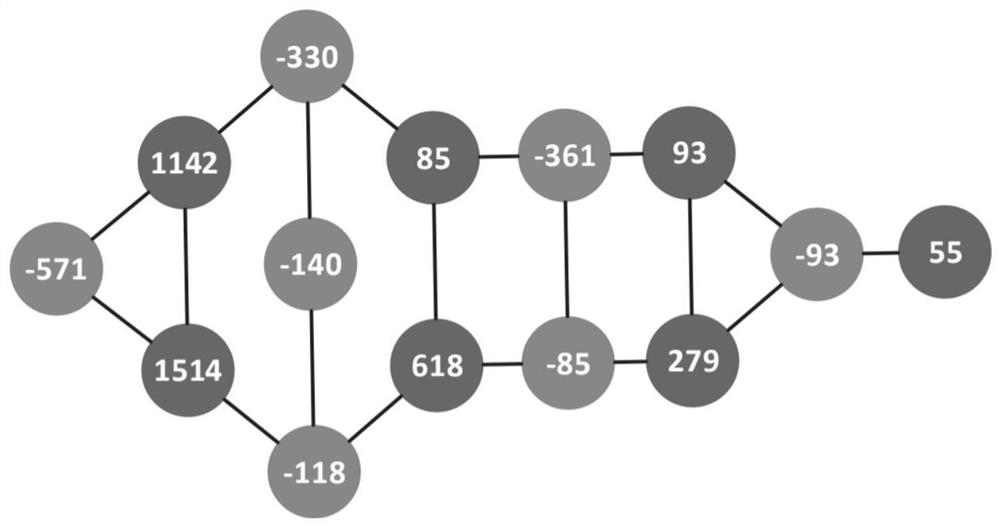
[0034] Step 2: Initialize the vertex set V and the edge set E to be empty.
[0035] Step 3: Add vertices to the vertex set. According to the order of the elements in P, pi is associated with vertex vi in turn and added to the vertex set V, and the vertex set V=[-571, 1514, 1142, -118, -140, -330, 618, 85, -85, - 361,279,93,-93,55].
[0036] Step 4: Divide the vertex set V into burst traffic sets B=[[-571],...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com