Source code protection method in project development process and storage medium
A development process and project technology, applied in the field of data security, can solve the problems of hacking, inconvenient, and unable to prevent the second type of accidents, and achieve the effect of preventing illegal attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
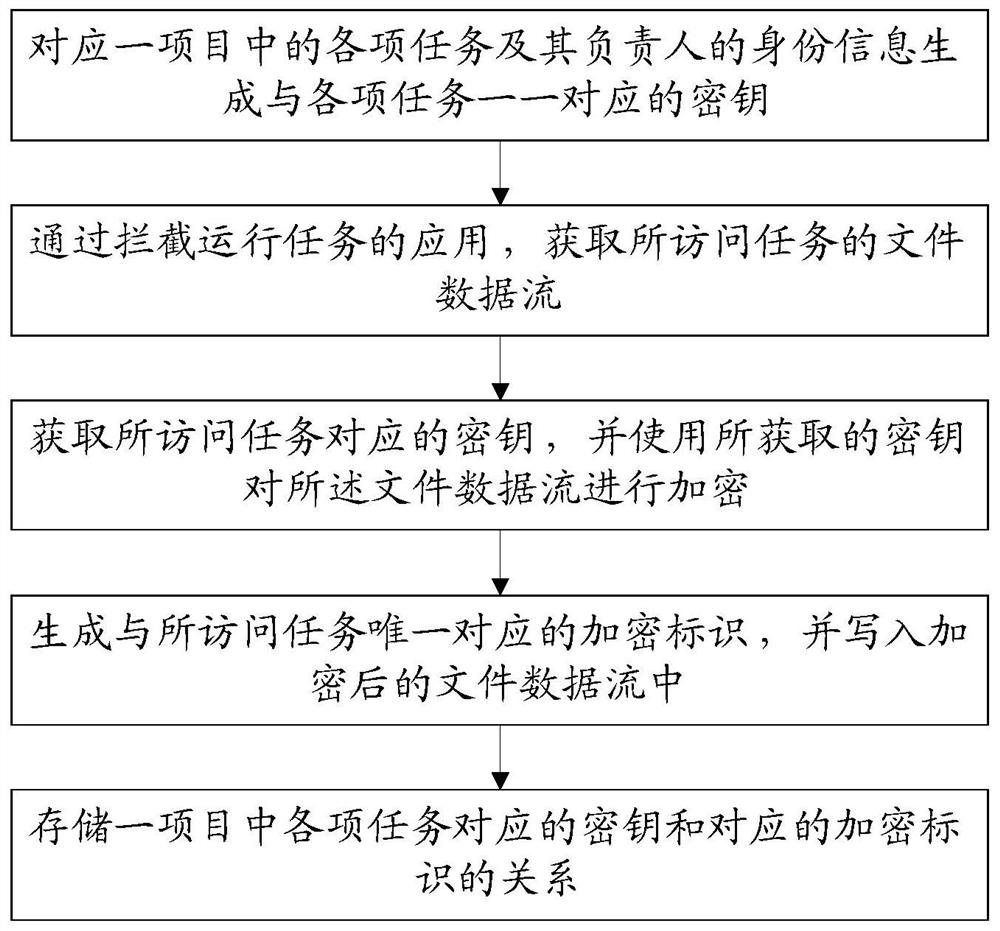
[0062] This embodiment provides a source code protection method in the project development process, which can effectively protect codes in the development stage for various tasks in a large project, and has the function of recovering responsibility after source code leaks.
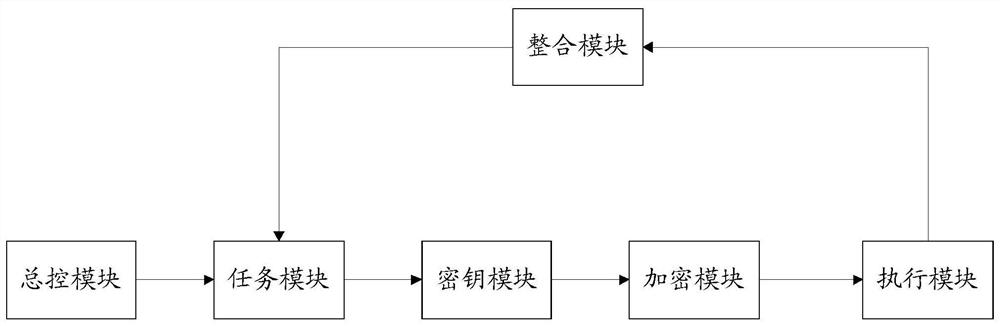
[0063] In a specific example, the composition and connection relationship of the functional modules corresponding to the method of this embodiment are as follows figure 2As shown, the master control module, the task module, the key module, the encryption module and the execution module are connected in sequence, and the integration module is connected with the execution module and the task module respectively. The deployment of tasks (assignment of specific tasks and corresponding responsible persons) is realized through the master control module, and the task module releases tasks (delivered to specific responsible persons); the keys of various tasks are generated through the key module; through the encry...
Embodiment 2
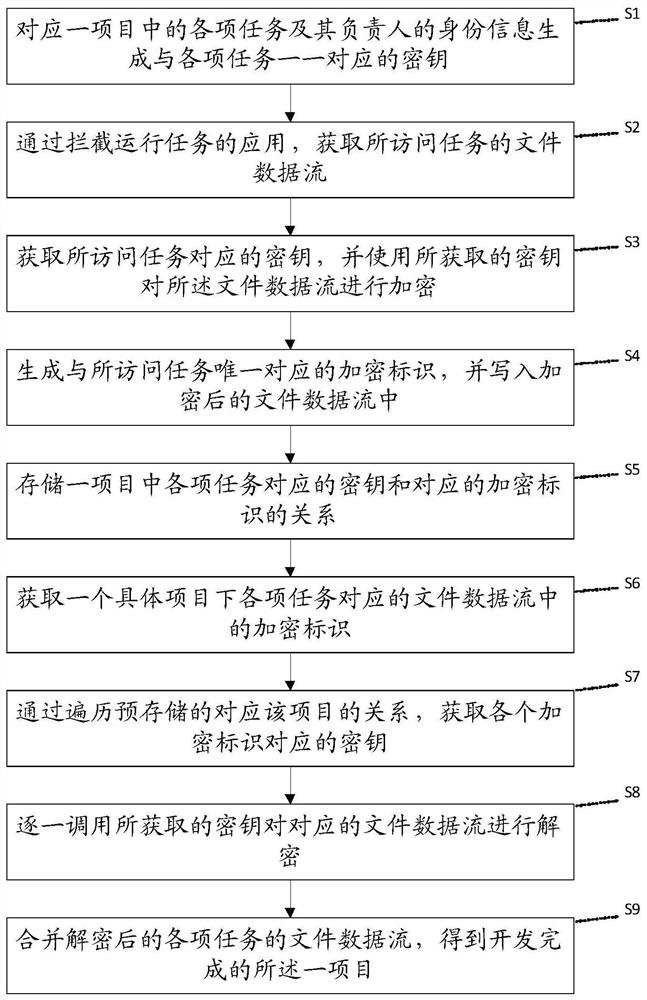
[0080] see image 3 , this embodiment makes further supplements on the basis of Embodiment 1, and provides the specific operation process after the completion of various tasks under the project:
[0081] S6: Obtain the encryption identifier in the file data stream corresponding to each task under a specific project;
[0082] S7: By traversing the pre-stored relationship corresponding to the item, that is, the relationship stored in step S5, to obtain the key corresponding to each encryption identifier;
[0083] S8: calling the obtained keys one by one to decrypt the corresponding file data stream;
[0084] S9: Merge the decrypted file data streams of various tasks to obtain the developed project.
[0085] In a specific example, the integration of tasks under the project is realized through the integration module, which is respectively connected with the task module and the execution module.
[0086] Specifically, the integration module calls a project, traverses all the HAS...
Embodiment 3
[0089] This embodiment corresponds to Embodiment 1 or Embodiment 2, and describes in detail the functions of task source code protection and accountability respectively:
[0090] (1) Task source code prevention and protection
[0091] (1) Operation protection
[0092] SS1: Use identity information to log in and specify the tasks to be accessed;
[0093] SS2: According to the relationship, confirm that the identity information of the person in charge corresponding to the task to be accessed is consistent with the currently logged-in identity information;
[0094] If inconsistent, deny access and end the process;
[0095] If they are consistent, determine whether the task to be accessed has been encrypted; if not, obtain the key corresponding to the task, and use the obtained key to encrypt the file data stream corresponding to the task, and generate the corresponding encryption key at the same time. key; if it has been encrypted, obtain the encrypted identifier in the file d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com