Data sharing method and related equipment
A technology of data sharing and equipment, applied in the direction of file metadata retrieval, special data processing applications, file access structure, etc., can solve the problems of high search complexity, low sharing efficiency, low efficiency, etc., to ensure sharing efficiency and security and privacy effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
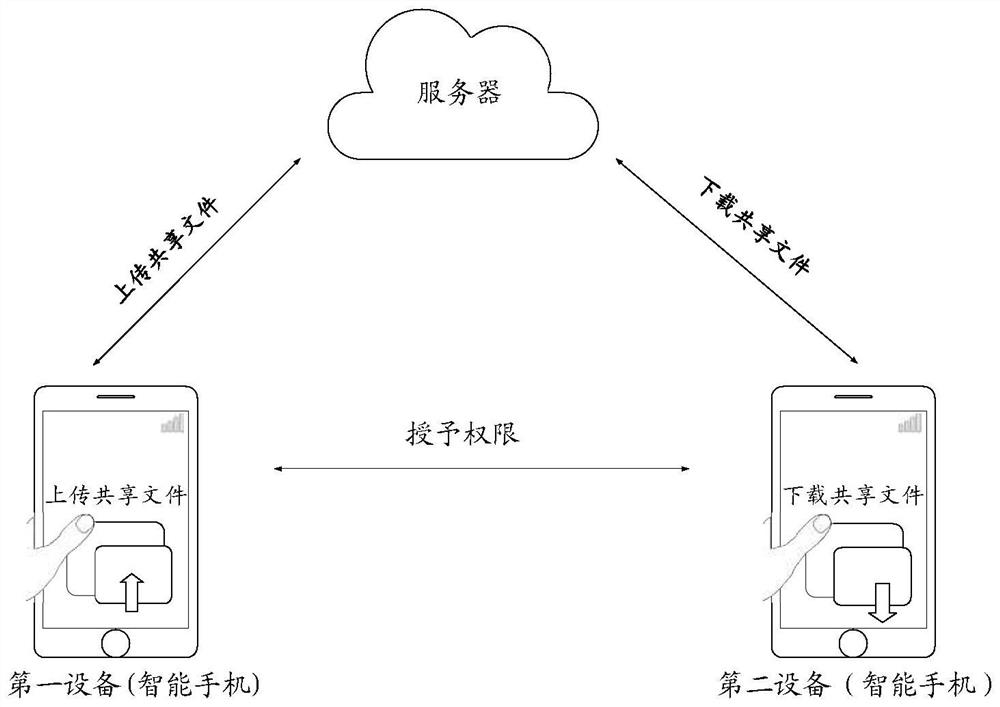
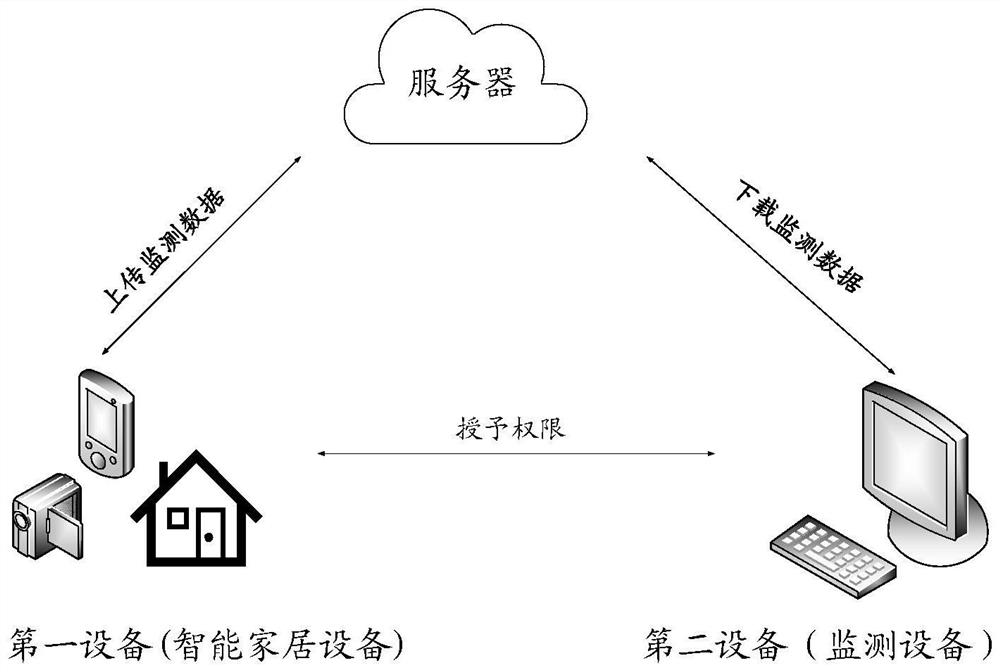
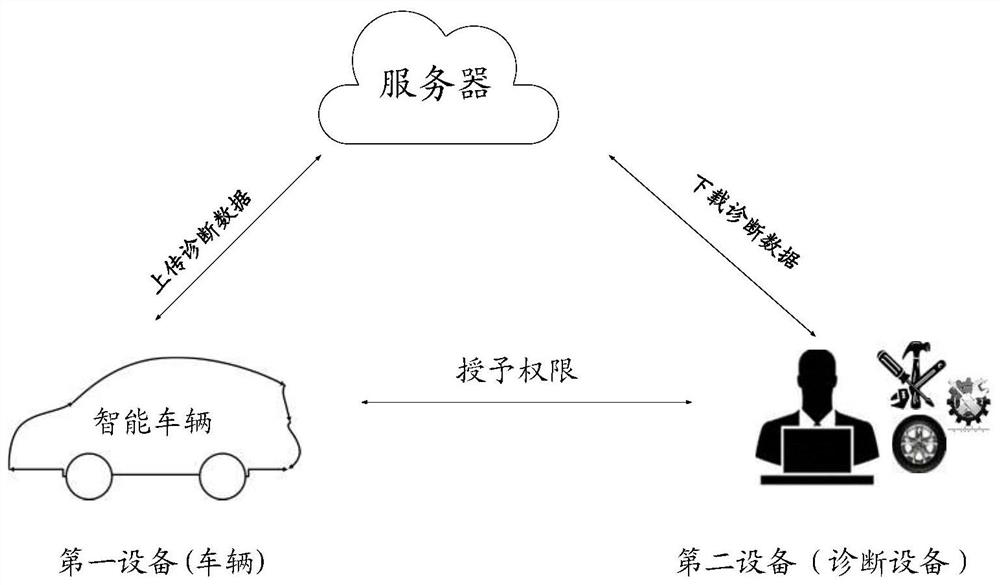
[0200] Mode 1, the first device uses the second key and the target index plaintext, uses a trapdoor generation algorithm to generate the query trapdoor, and sends the query trapdoor to the second device, and the second device The query trapdoor sent by the first device is received, wherein the target index plaintext is an index plaintext corresponding to the target index ciphertext, and the second key is a symmetric key. Alternatively, the first device uses the first private key and the target index plaintext, uses a trapdoor generation algorithm to generate the query trapdoor, and sends the query trapdoor to the second device, and the second key is the first public key of the first device, and the first private key is a private key corresponding to the second key. That is, in the embodiment of the present invention, for the encryption of the index plaintext, a symmetric key can be used, and then the corresponding query trapdoor can also use the same symmetric key; or, for the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com