Visual dynamic honeynet custom topology deployment method
A custom, honeynet technology, applied in the computer field, can solve the problems of difficult analysis due to limited view, troublesome deployment, single selection, troublesome maintenance and time-consuming management, etc., to reduce the limited analysis view, reduce complexity, and improve construction efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
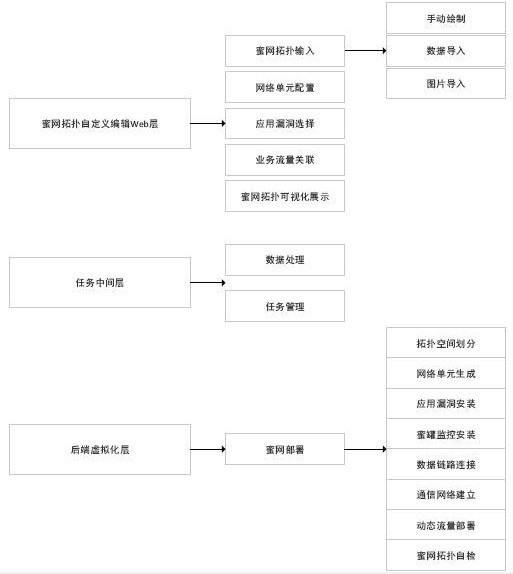
[0036] Please refer to figure 1 As shown, the present invention discloses a method for deploying a visualized dynamic honeynet custom topology, including the following steps:
[0037] (1) Input the topology to the honeynet topology custom editing page by manual drawing, data import or picture import. In this embodiment, the manual drawing import method refers to manually dragging the network unit control based on jQuery to enter the topology canvas to generate a preliminary honeynet topology; the middle data import method refers to the import including but not limited to Json, txt, xml Parameter files in other formats to generate a preliminary honeynet topology; the image import method refers to importing image files and generating a preliminary honeynet topology through identification. The image file types include but are not limited to bmp, jpg, png, tif, etc.
[0038] (2) Visually display the preliminary honeynet topology obtained from step (1) on the honeynet topology cus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com