A method for traceability of IP address organization based on knowledge graph
A technology of IP addresses and knowledge graphs, applied in the field of network information, can solve problems such as clustering errors, reduced solution efficiency, and inaccurate clustering results, and achieve the effect of ensuring accuracy and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
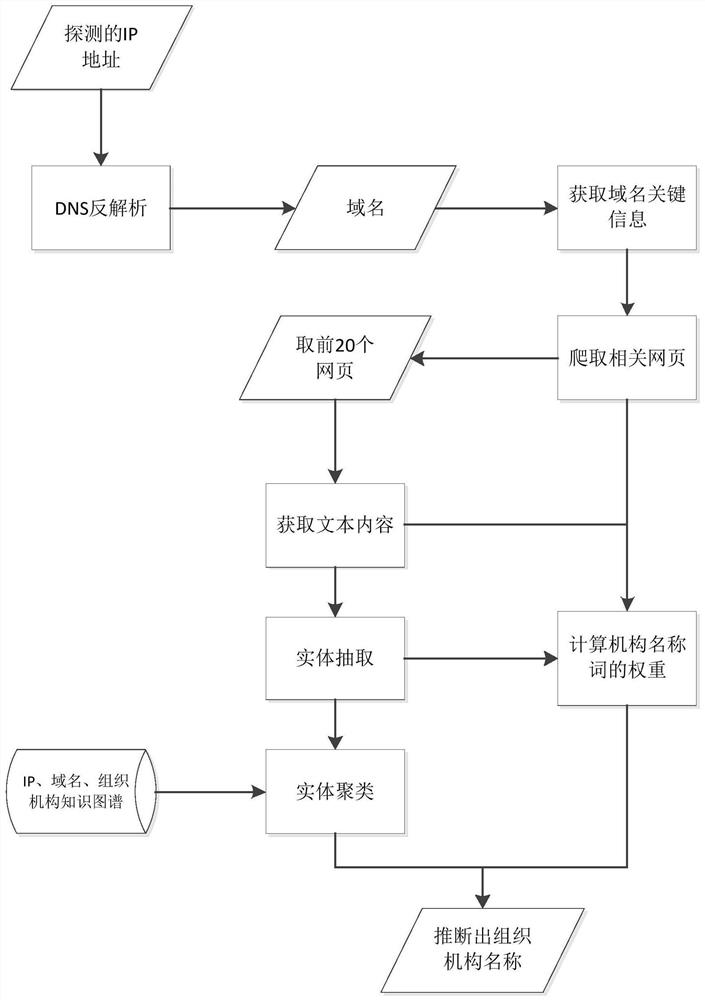
[0047] This embodiment aims at many problems of information security in cyberspace in the prior art, especially the situation where it is difficult to trace back to its affiliated organization under the current situation of isolated and scattered security information, and proposes a way of tracing the source, which can be based on the hidden information contained in the IP address. Find the available information in , and calculate and extrapolate the most likely said institution.
[0048] Specifically, such as figure 1 As shown, this embodiment discloses a method for traceability of IP address institutions based on knowledge graphs, including:
[0049] S01. Obtain domain name information: for the effective IP address of the institution to be inferred, obtain the domain name information corresponding to the IP address through DNS reverse analysis;
[0050] S02. Obtain key domain name information: truncate and screen the domain name information to obtain key information in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com