Proxy access method, control network equipment and proxy access system
A technology for controlling network and access method, applied in the field of network communication, can solve problems such as strong networking limitations and inability to achieve normal communication, and achieve the effects of ensuring interoperability, reducing the probability of being stolen, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
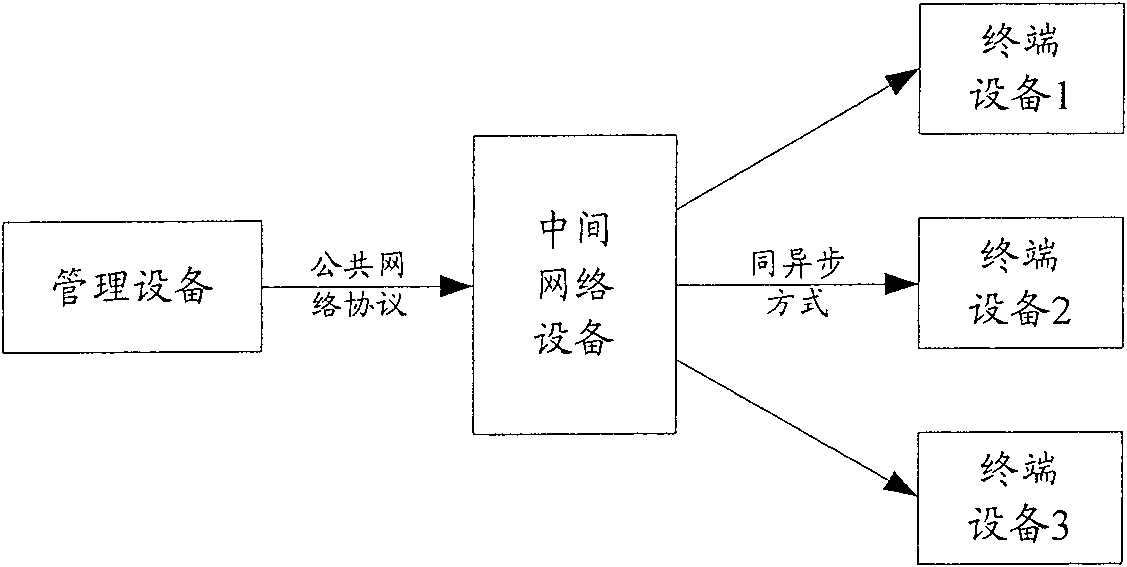
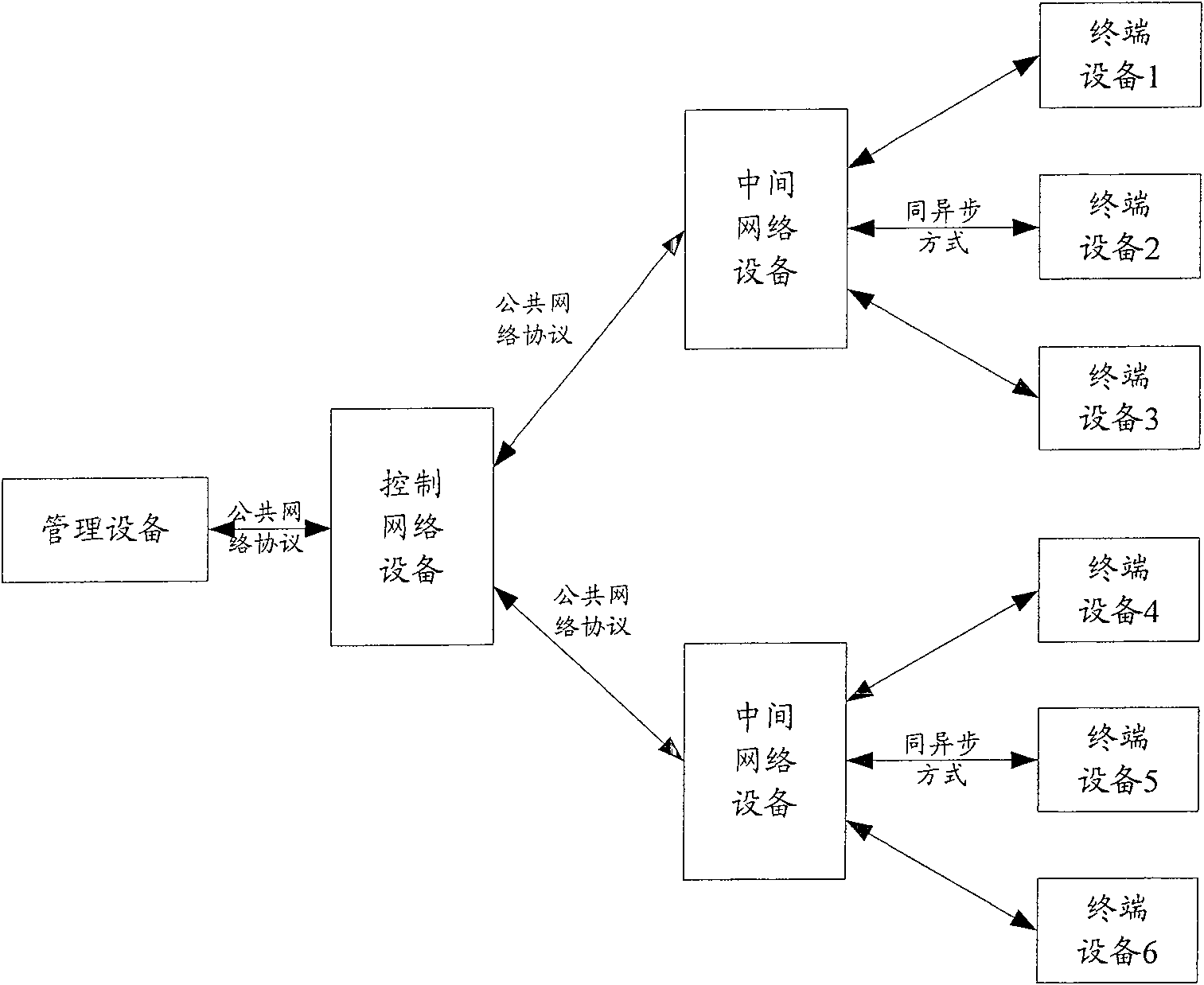
[0071] This embodiment is aimed at a proxy access system in which a management device actively initiates an access type. image 3 A schematic structural diagram of the proxy access system in this embodiment is shown. see image 3 , the system includes: management equipment, control network equipment, intermediate network equipment and terminal equipment. The management device and the control network device have fixed IP addresses; the management device indicates the identity of the terminal device to be accessed when initiating access, and the control network device converts the information of the management device to the intermediate network device before forwarding the information to The format of the network protocol that the intermediate network device and the terminal device can recognize, and modify the source IP address to its own IP address. In this way, in this embodiment, in addition to ensuring the normal communication between the management device, the intermedia...
Embodiment 2
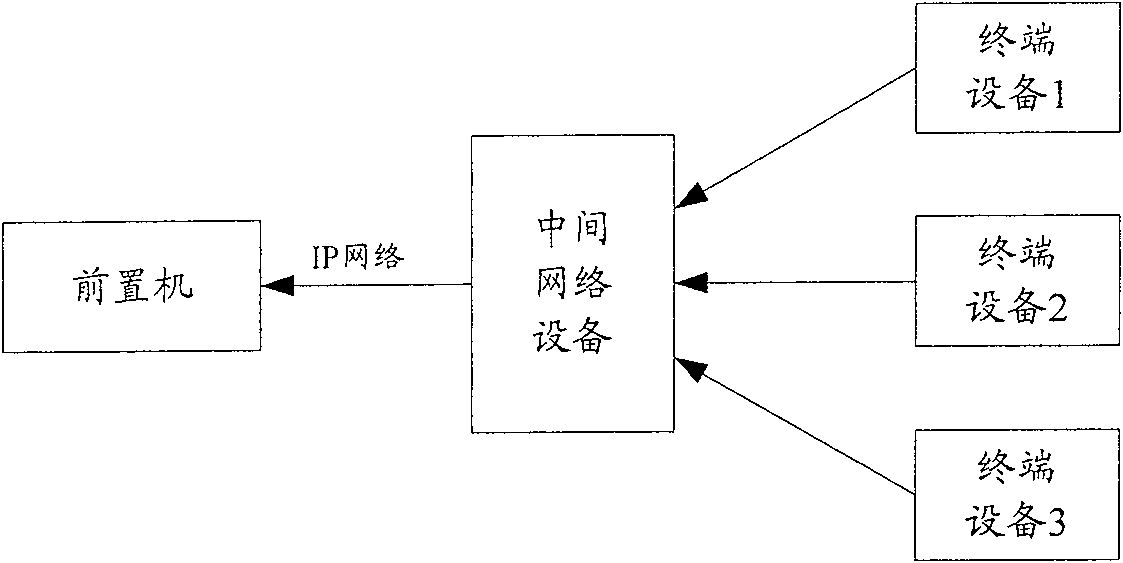
[0115] This embodiment is aimed at a proxy access system in which a terminal device actively initiates an access type. This embodiment can still use image 3 The structure of the proxy access system is shown. see image 3 , the system includes: management equipment, control network equipment, intermediate network equipment and terminal equipment. The management device and the control network device have fixed IP addresses; the terminal device first initiates access through the intermediate network device, and the control network device converts the information into a network protocol that the management device can recognize before forwarding the information from the intermediate network device Change the source IP address to its own IP address. In this way, this embodiment can not only ensure the normal communication of each device, but also improve the security of the access process.
[0116] Correspondingly, when performing access in this embodiment, after the control ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com