Security policy self-feedback method based on security log association analysis
A correlation analysis and security policy technology, applied in the field of network information security, can solve problems such as inconsistent log formats of business protection systems, difficulty in automating security policies, and high rate of false positives in alarm notifications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
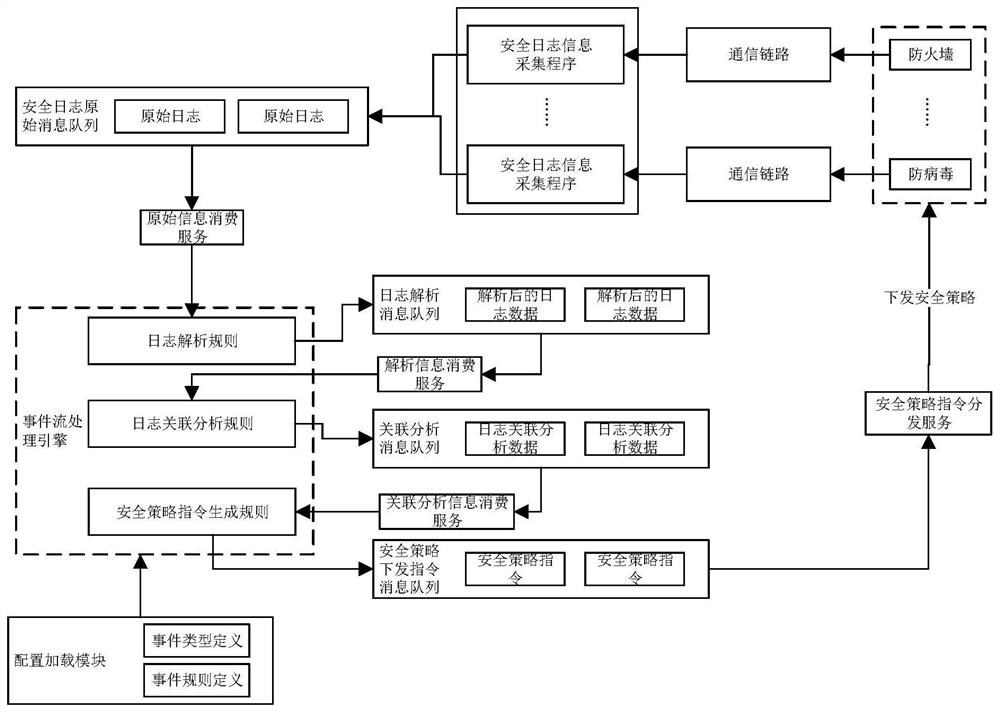
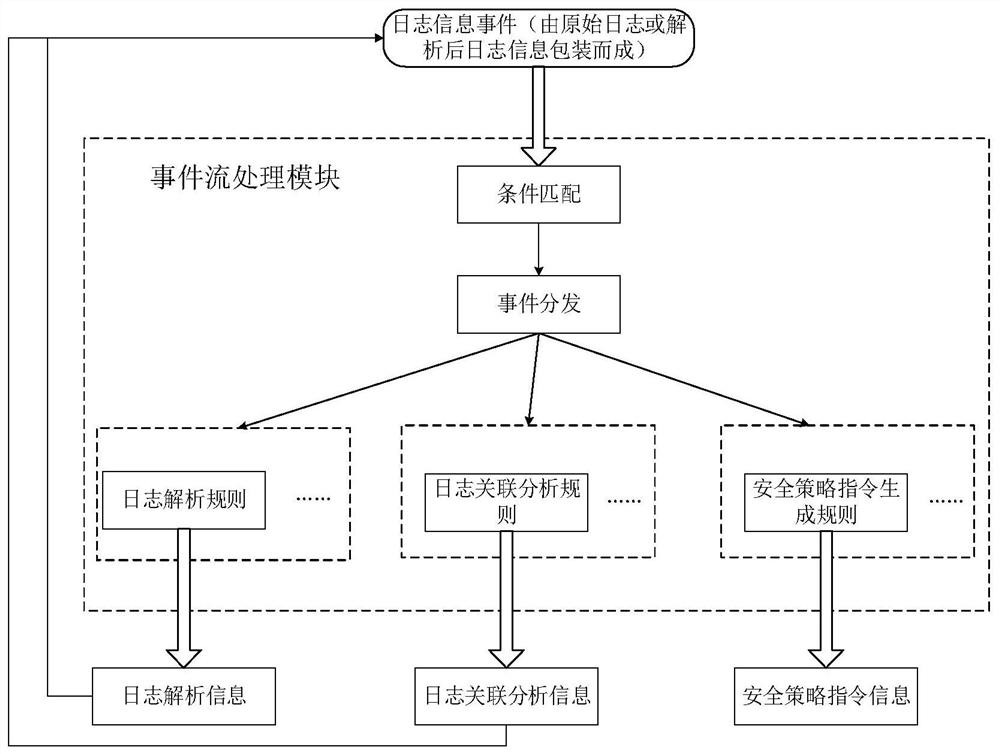
[0064] The embodiment of the present invention discloses a security policy self-feedback method based on the correlation analysis of security logs. This method is applied to the scene where multiple network security protection devices work together in an enterprise. By using this method, multiple independent network security protection devices are formed. A network security protection system with self-control and self-feedback capabilities can automatically respond to external attacks and threats and issue security policies. In order to do a good job in network security protection, enterprises usually purchase multiple network security protection devices, such as intrusion detection devices, firewalls, security auditing, anti-virus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com