Power industry network security management system and method
A network security and power industry technology, applied in the transmission system, electrical digital data processing, computer security devices, etc., can solve the problems of hidden dangers of information security, inconsistent information, and inability to achieve collaborative work, etc., to improve information security, Realize the effect of collaborative work and avoid information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
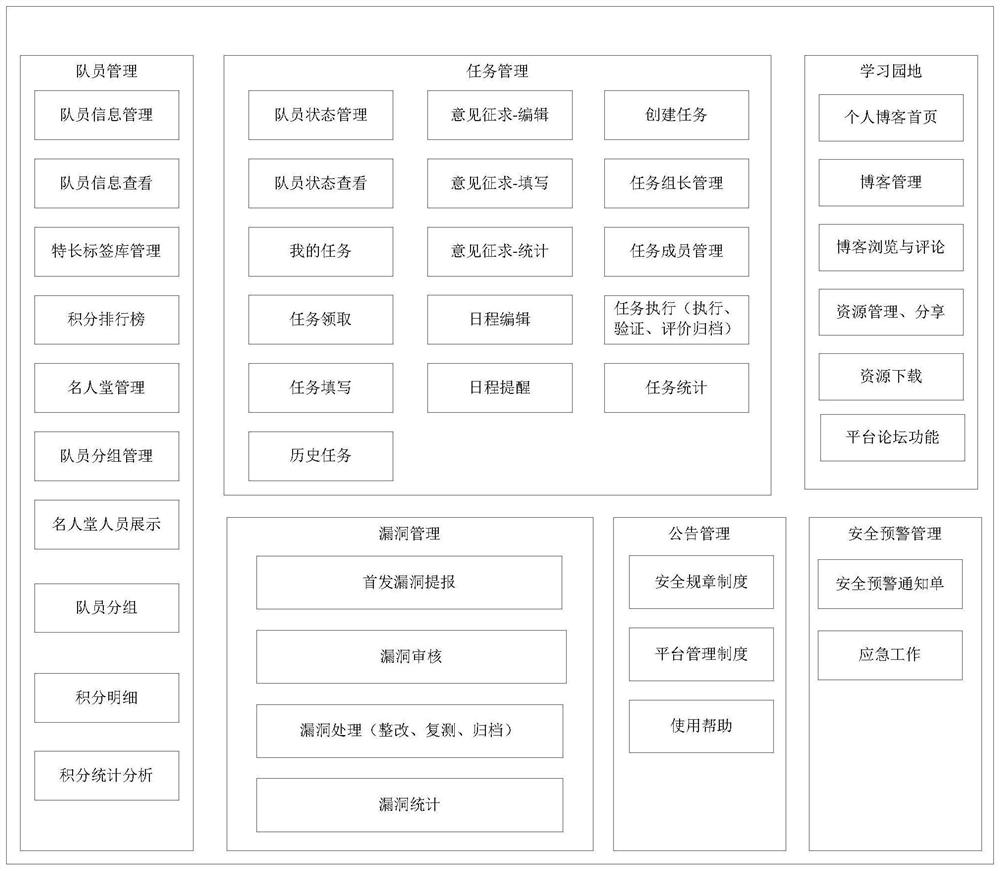
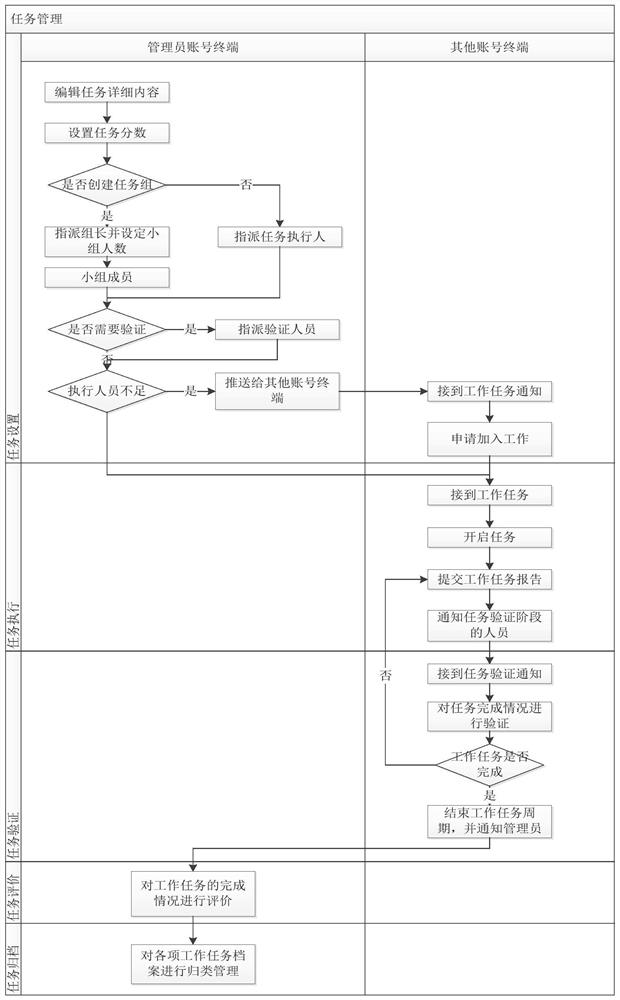
[0030] In one or more implementations, a power industry network security management system is disclosed, referring to figure 1 , including:
[0031] The account management module is configured to assign different data processing permissions to different accounts; at the same time, it can realize the management and maintenance of account basic information and status, manage the work schedule of different account terminals, basic personnel information, and score management statistics.
[0032] In this embodiment, the account terminals include: an administrator account terminal, a task executor account terminal, a task retester account terminal, and a task verifier account terminal.
[0033] The network security vulnerability monitoring module is configured to receive network security vulnerability information, generate a vulnerability review task, and send it to the account terminal with corresponding authority for vulnerability review, and perform a security risk assessment on ...
Embodiment 2
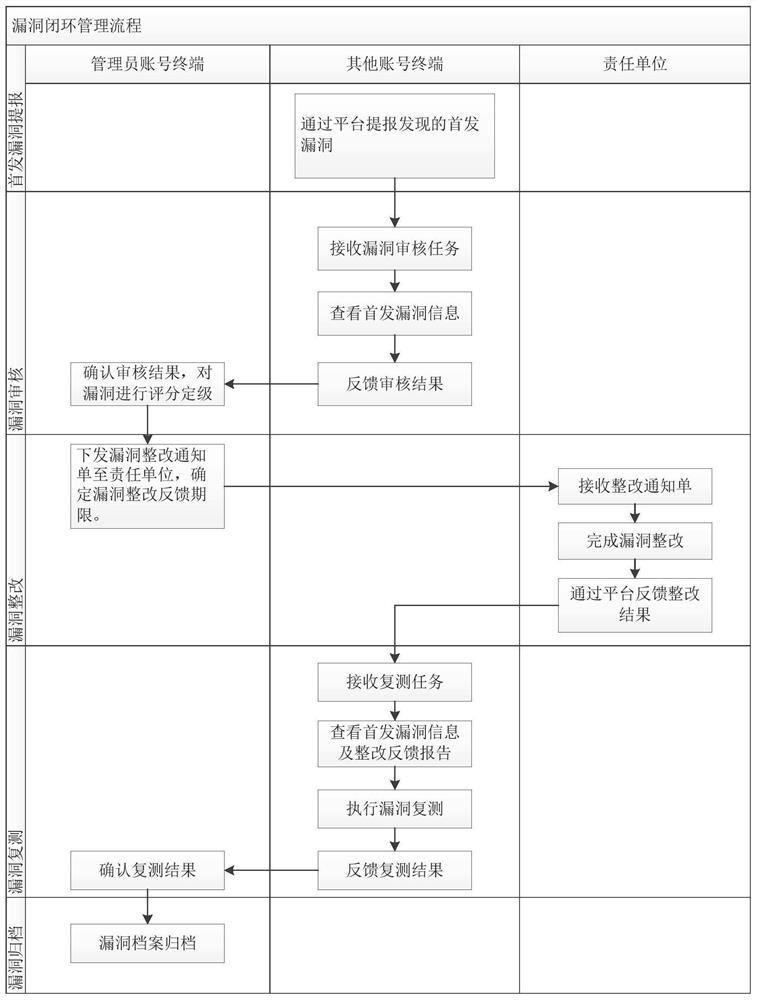
[0055] In one or more implementations, a method for network security management in the electric power industry is disclosed, referring to figure 2 , including the following procedures:
[0056] (1) Receive network security vulnerability information, generate a vulnerability audit task, and send it to the account terminal with corresponding authority for vulnerability audit;
[0057] Regarding the reporting of network security vulnerability information, the account terminal can report the first discovered vulnerabilities, and the administrator account terminal can rate the reported vulnerabilities and initiate a loophole closed-loop management process; the system provides a first-time vulnerability report template, in the template After filling in the vulnerability-related information and submitting it, the vulnerability can be directly pushed to the relevant responsible unit. The vulnerability report template can generate a Word document, so there is no need to repeatedly wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com