Method for logging in terminal equipment by cloud user
A terminal device and cloud technology, applied in the field of network security, to achieve the effect of maintaining security and reliability and reducing risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
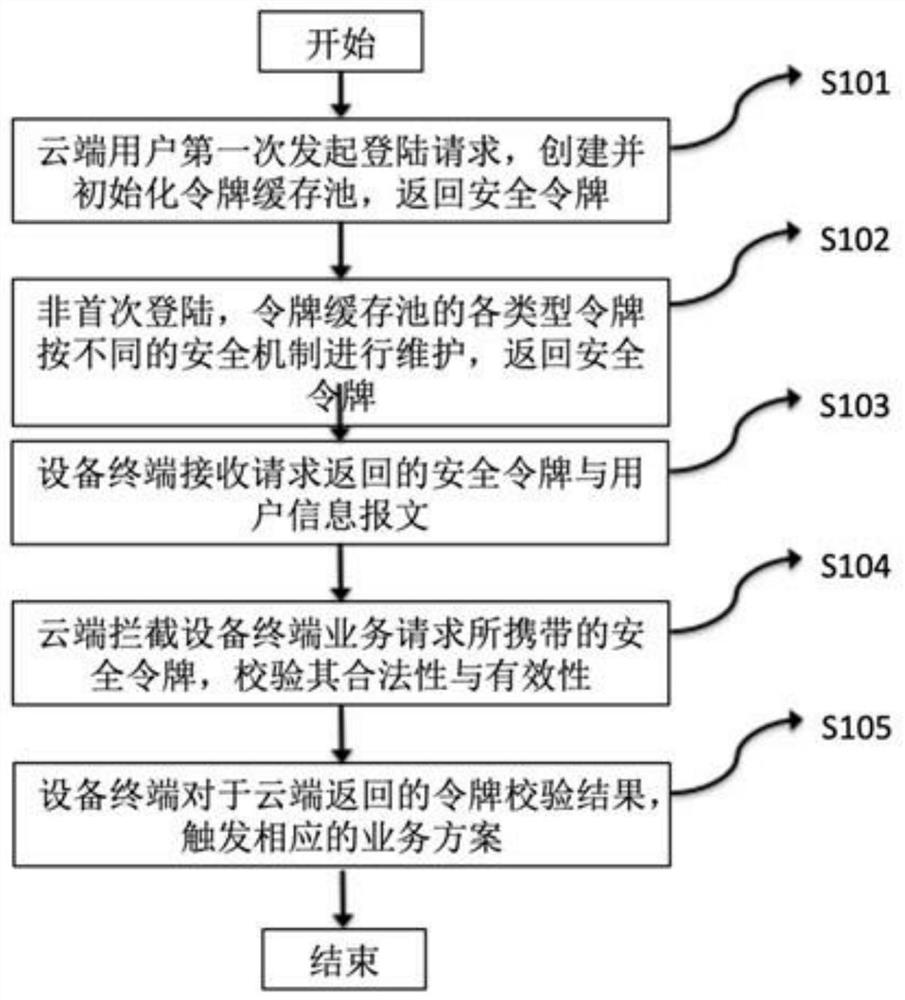
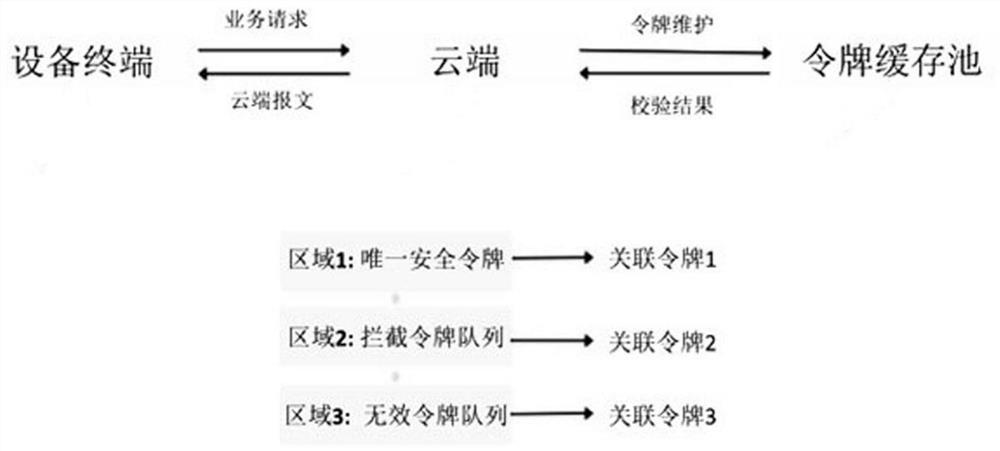
[0024] combine figure 1 and figure 2 As shown, a method for a cloud user to log in on a terminal device includes the following steps:
[0025] Step S101, the cloud user initiates a login request on the terminal device for the first time, the cloud creates and initializes a token cache pool, creates a security token and pushes it into area 1, and creates an associated token (associated token 1) of the security token at the same time, The terminal device initiates a login request to the cloud based on the entered user name, password, and device SN number; the cloud intercepts the user information reported by the terminal device, and verifies the validity of the password after the verification of the user name and SN number passes; if the password If it is illegal, it will return a message indicating that the password is wrong to the terminal device; if the password is legal, it will obtain the necessary basic data; according to the basic necessary data, create a security token...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com