Internet of Vehicles position information encryption cloud platform, terminal, system and method
A location information and cloud platform technology, applied in location information-based services, transmission systems, vehicle wireless communication services, etc., can solve problems such as Internet of Vehicles equipment and user privacy and security threats, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
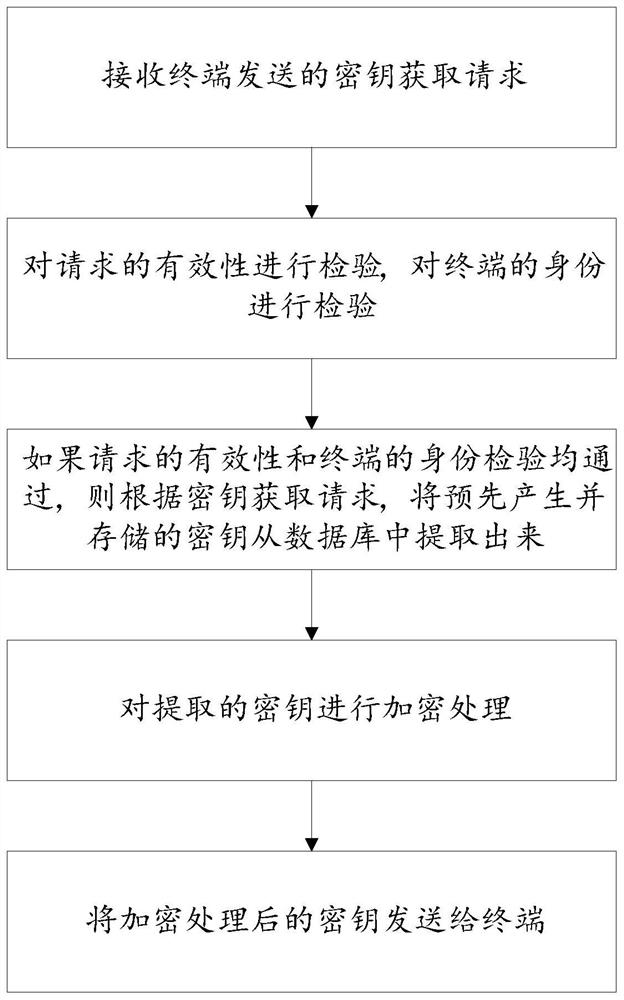
[0049] This embodiment provides a cloud platform for encrypting location information of the Internet of Vehicles;
[0050] Such as figure 1 As shown, the Internet of Vehicles location information encryption cloud platform is configured as:
[0051] receiving the key acquisition request sent by the terminal;
[0052] Verify the validity of the request and verify the identity of the terminal;
[0053] If the validity of the request and the identity verification of the terminal pass, the pre-generated and stored key is extracted from the database according to the key acquisition request;
[0054] Encrypt the extracted key;
[0055] Send the encrypted key to the terminal.
[0056] Further, the validity of the request is checked, and the identity of the terminal is checked; the specific steps include:
[0057] The cloud platform obtains the AC private key of the terminal;
[0058] Based on the AC private key of the terminal, the cloud platform uses ACA to verify the validity ...
Embodiment 2
[0084] This embodiment provides a terminal for encrypting location information of the Internet of Vehicles;
[0085] The location information encryption terminal of the Internet of Vehicles is configured as:
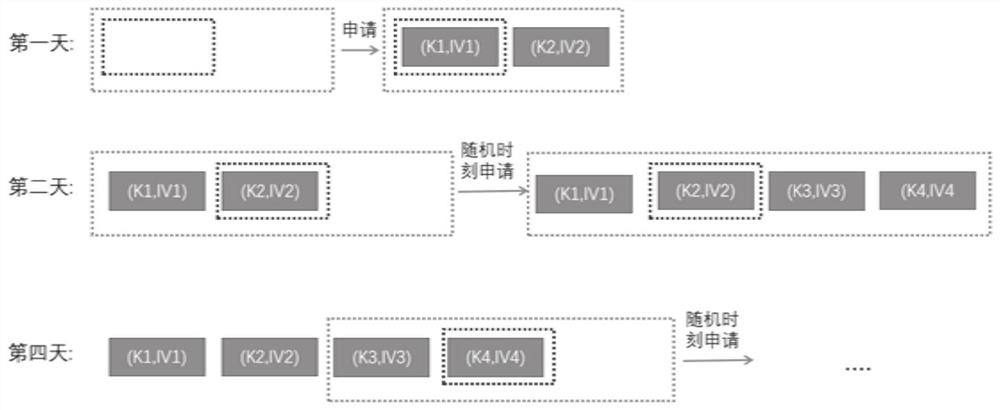
[0086] Send an application for obtaining a key to the cloud platform;
[0087] The key to receive feedback from the cloud platform;
[0088] Decrypt the feedback key;
[0089] Encrypt the location information of the Internet of Vehicles to be encrypted based on the decrypted key;
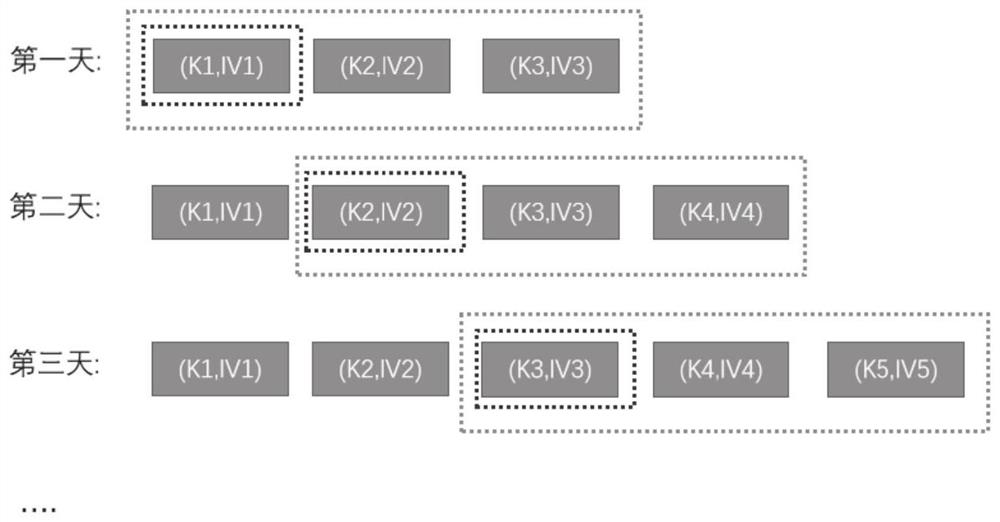
[0090] Wherein, the key fed back by the cloud platform is a key generated and stored by the cloud platform; the key is updated regularly.
[0091] It should be understood that the terminal in this application applies for the location information encryption key from the cloud platform to meet the following security requirements: the security and credibility of the application process; the use of AC private key signatures to prove its identity; the security of key calculation and storage ;Ke...
Embodiment 3
[0112] Embodiment 3, the present application provides a system for encrypting location information of the Internet of Vehicles;
[0113] IoV location information encryption cloud system, including: terminal and cloud platform;
[0114] The cloud platform is configured to: receive a key acquisition request sent by a terminal; check the validity of the request and check the identity of the terminal; if both the validity of the request and the identity of the terminal pass, then according to the key Get the request, extract the pre-generated and stored key from the database; encrypt the extracted key; send the encrypted key to the terminal;
[0115] The terminal is configured to: send an application for obtaining a key to the cloud platform; receive a key fed back by the cloud platform; decrypt the fed back key; encrypt the location information of the Internet of Vehicles to be encrypted based on the decrypted key; Wherein, the key fed back by the cloud platform is a key generat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com