Deciphering method for ciphering service, conditional access system and smartcard
An encryption service and conditional access technology, applied in analog security/charging systems, transmission systems, digital transmission systems, etc., can solve problems such as large user cards, and achieve the effect of strengthening protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
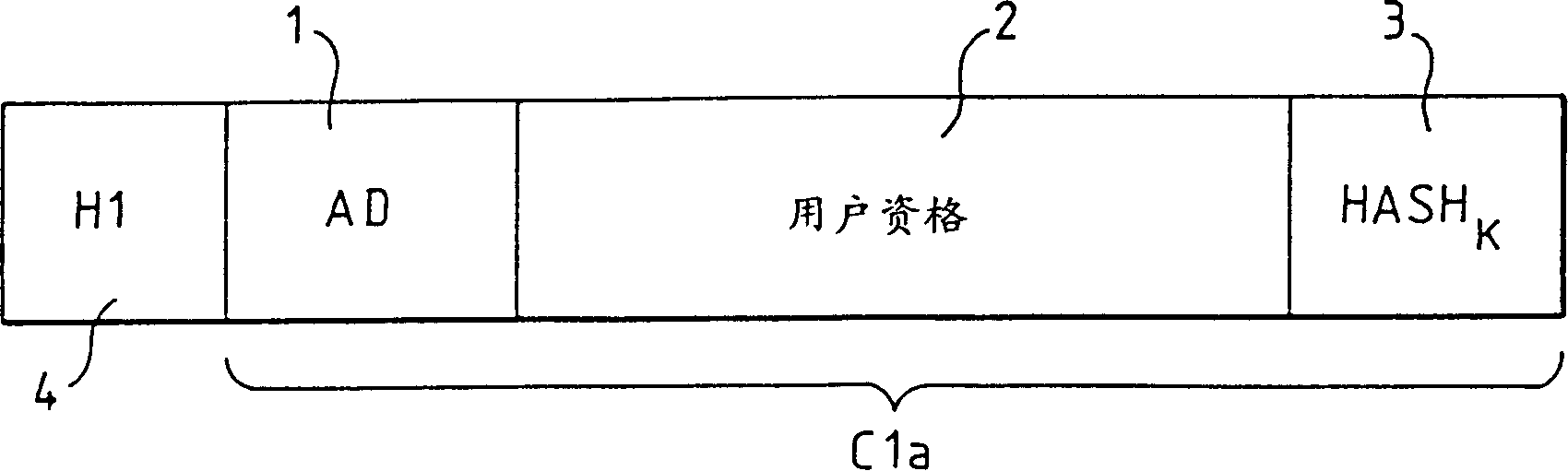
[0031] Figure 1a represents a first EMM format according to the prior art.
[0032] Figure 1a The EMM represented in has a body C1a containing the three main items described earlier and a heading 4 whose content (H1) gives, among other things, the type and size of the items contained in body C1a.
[0033] Subject C1a includes item 1 containing user card address (AD), item 2 containing user qualification description and a trailing prompt HASH K Item 3. Tail tip HASH K depends on the password K and enables it to perform the aforementioned analysis of EMMs.
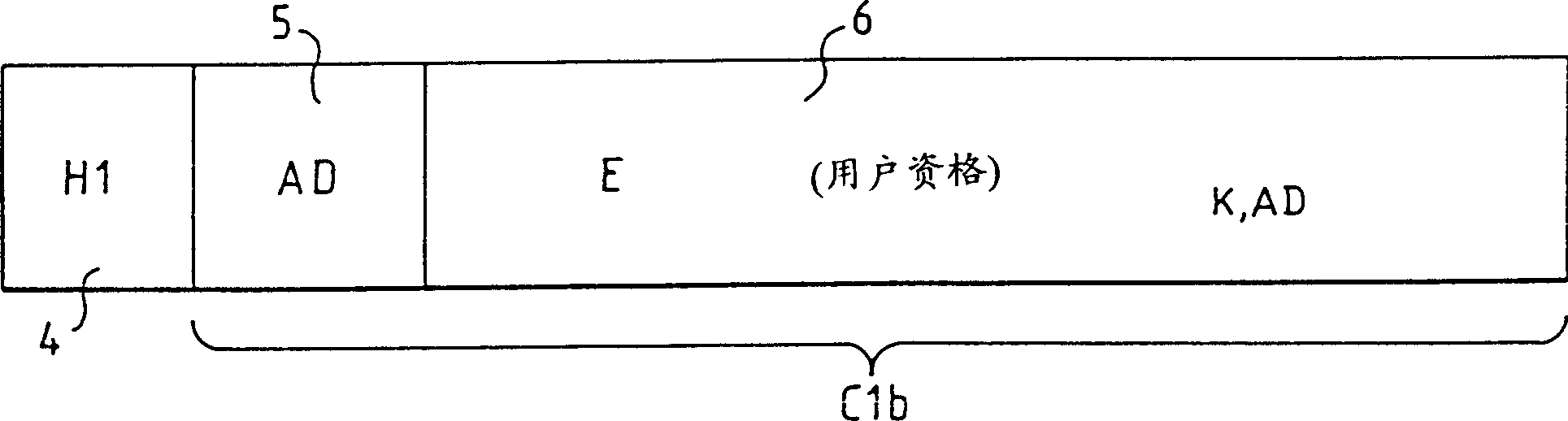
[0034] Figure 1b Represents a second EMM format according to the prior art.
[0035] The EMM includes a header 4 and a body C1b.
[0036] The subject C1b includes the address AD containing the user card and the description of the user qualification encrypted with the algorithm with the password K and related to the address AD (E(user qualification) K,AD ). According to this EMM format, verification and validation o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com