A method of penetrating a window with a magnifying glass based on windows system
A magnifying glass and window technology, which is applied in the field of remote conference sharing windows, can solve the problems of affecting the use of non-sharing windows, affecting the efficiency of sharing activities, and lack of intelligence, so as to prevent easy cracking and leakage, ensure accuracy, and good compatibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
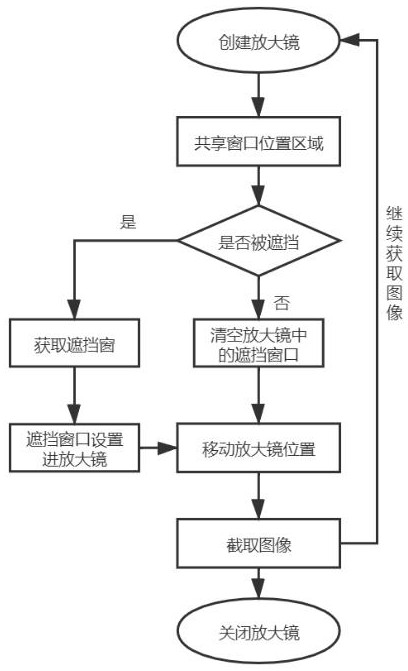
[0041] A method for a magnifying glass penetrating a window based on a windows system, comprising the following steps:
[0042] S10. Using the screen monitoring software disclosed in the prior art, regularly monitor whether the current shared window is blocked by a non-shared window, and the monitoring time interval is set to once every 5 seconds.
[0043] S11. When it is detected that the current shared window is blocked by a non-shared window, start a pre-programmed program to call the built-in magnifying glass application program under the windows system, and set the magnifying glass program as a hidden attribute, that is, the magnifying glass application is not displayed on the desktop of the computer Operation interface;
[0044] S12. Obtain the position and size of the current shared window on the screen through screen monitoring software or a program compiled separately;
[0045] S13. Select all non-shared window objects that block the shared window;
[0046] S14. Set...
specific Embodiment 2
[0052] A method for a magnifying glass penetrating a window based on a windows system, comprising the following steps:
[0053] S10. Call the screen capture application that comes with the windows system every preset time (for example, 5 seconds) to capture the computer screen, select and activate the current shared window at the same time, and call the screen capture application that comes with the windows system to capture the current screen again. Active window, and then call the image analysis software (you can use the AI code disclosed in the prior art, or you can write the program yourself) to compare and judge whether the intercepted current active window can completely overlap with the part of the corresponding intercepted computer screen , if the result is yes, it means that the current shared window is not blocked by other windows; if the result is no, it means that the current shared window is blocked by other windows.
[0054] S11. When it is detected that the cu...
specific Embodiment 3
[0063] A method for a magnifying glass penetrating a window based on a windows system, comprising the following steps:
[0064] S10. Call the screen capture application that comes with the windows system every preset time (for example, 5 seconds) to capture the computer screen, select and activate the current shared window at the same time, and call the screen capture application that comes with the windows system to capture the current screen again. Active window, and then call the image analysis software (you can use the AI code disclosed in the prior art, or you can write the program yourself) to compare and judge whether the intercepted current active window can completely overlap with the part of the corresponding intercepted computer screen , if the result is yes, it means that the current shared window is not blocked by other windows; if the result is no, it means that the current shared window is blocked by other windows.
[0065] S11. When it is detected that the cu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com