Encryption system adapted for various key types
An encryption system and key technology, which is applied in the field of key management system, can solve the problems of poor scalability of the chip card encryption system, poor transaction security, inability to adapt to various types of keys, etc., and achieve high transaction security and expansion good sex effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with specific embodiments of the present invention. Obviously, the described embodiments are only some of the embodiments of the present invention, not all of them.
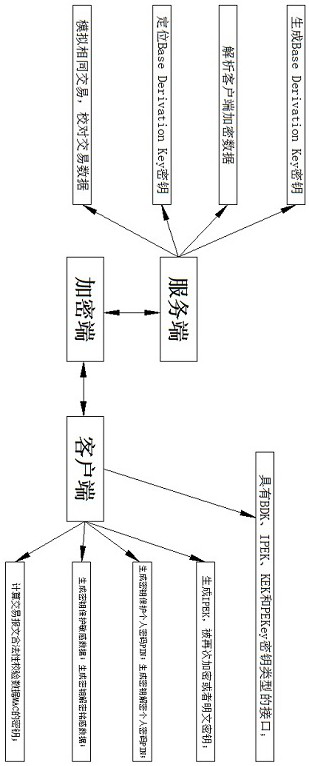
[0018] refer to figure 1 , an encryption system adapted to multiple key types provided by this scheme, including a server, a client and an encryption end based on Derived Unique Key Per Transaction, the encryption end is used to encrypt transactions between the server and the client .
[0019] The server, the server generates a key, and imports the Derived Unique Key Per Transaction application into the transaction card; the transaction card uses an on-chip COS system; the server generates an Initial PIN Encryption Key according to the Key Serial Number as a backup .
[0020] The client injects the Initial PIN Encryption Key into the terminal application, encrypts the personal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com