Formalized modeling method of handshake protocol based on HCPN model
A technology of formal modeling and handshake protocol, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as blind selection of formal analysis tools for security protocols
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
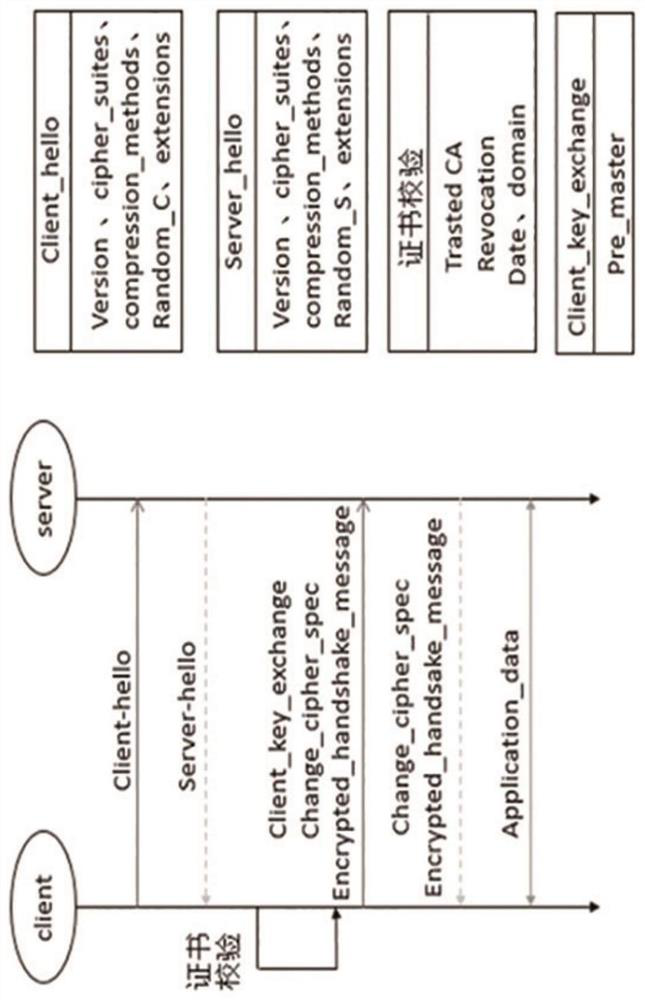
[0027] The present invention is based on the formal modeling method of the handshake agreement of HCPN model, and its steps are:
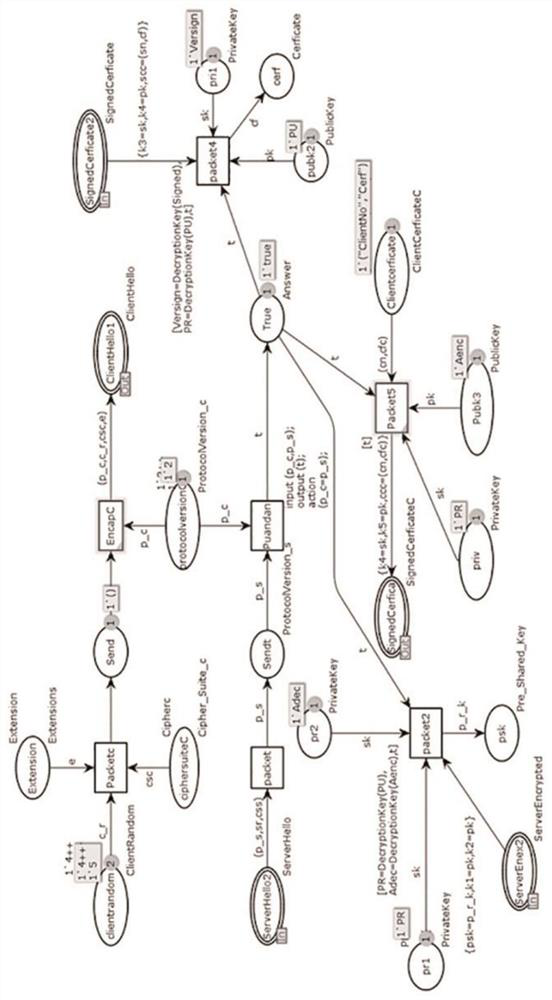
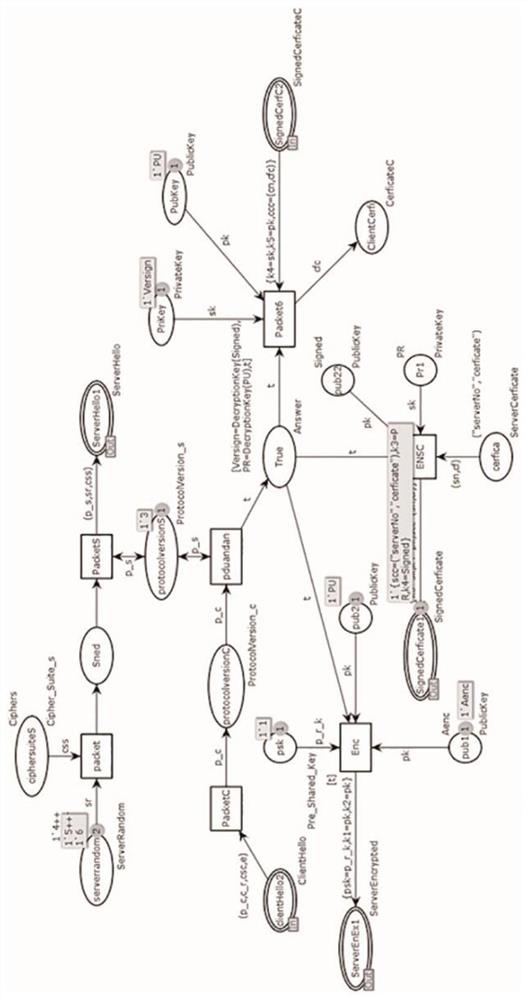
[0028] Step (1) Define the TLS1.3 handshake protocol based on the HCPN model, use a single color set and a composite color set to distinguish different data types of the protocol, and define data types such as places, transitions, arcs, encryption and decryption functions used by the protocol;
[0029] Step (2) Establish a formalized model of pre-master key transmission based on the HCPN model, the pre-master key is used as a key parameter, the client uses a symmetric encryption algorithm to encrypt and then sends it to the server, and the server decrypts it to obtain the pre-master key;
[0030] Step (3) Establish a formalized identity authentication model between the client and the server based on the HCPN model. The server sends encrypted identity information to the client. After the client decrypts, it queries the certificate chain to verify the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com