A Model Checking Method for Security Exchange Protocol
A security exchange and model detection technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of the attacker model and the attacker model inapplicable to the verification of security attributes, and the inability to model cryptographic primitives. Save time and space requirements, solve state explosion problems, easy-to-use effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. If there are exemplary contents in these embodiments, they should not be construed as limiting the present invention.
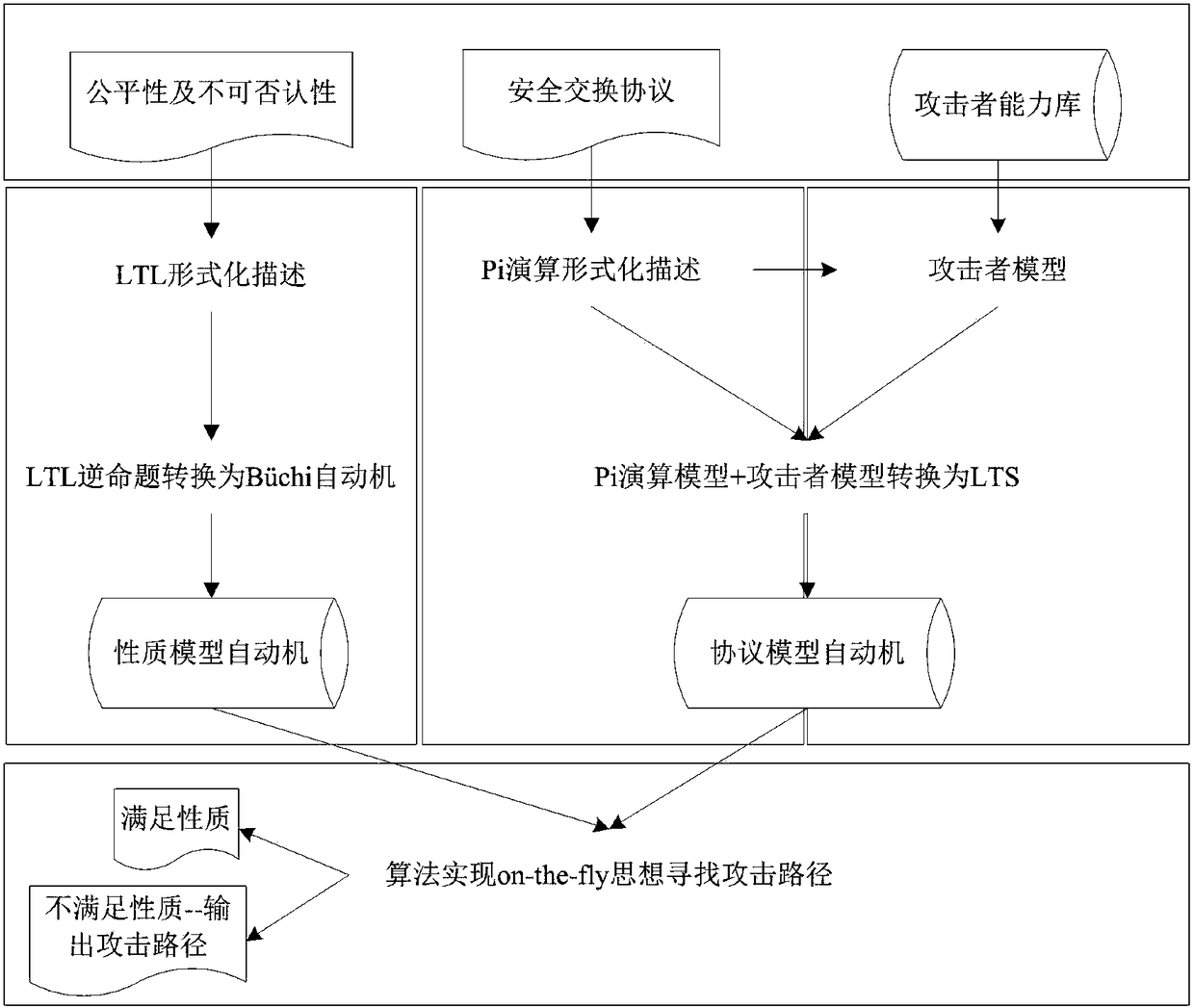
[0021] Such as figure 1 As shown, the present invention uses LTL linear sequential logic to describe the fairness and non-repudiation of the protocol participants, and converts it into an automaton, thereby facilitating verification. Detection methods for fairness and non-repudiation verification for secure exchange protocols. Specifically:
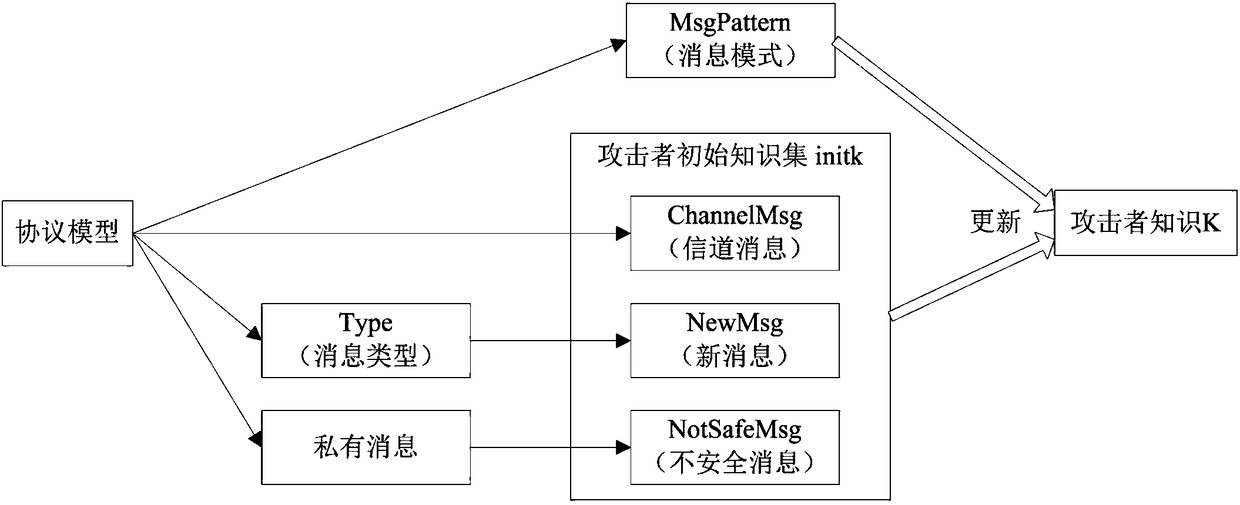
[0022] 1. Based on the Proverif modeling language Pi calculus, the selection operator is extended to formally describe the security exchange protocol. The operational semantics of the modeling language extended Pi calculus is realized based on the Labeled Transition System (LTS) , the extended Pi calculus can model cryptographic primitives;
[0023] 2. The fairness and non-repudiation o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com