Monitoring method and device for data access based on white list and related product
A data access and whitelist technology, applied in the blockchain field to reduce the risk of data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
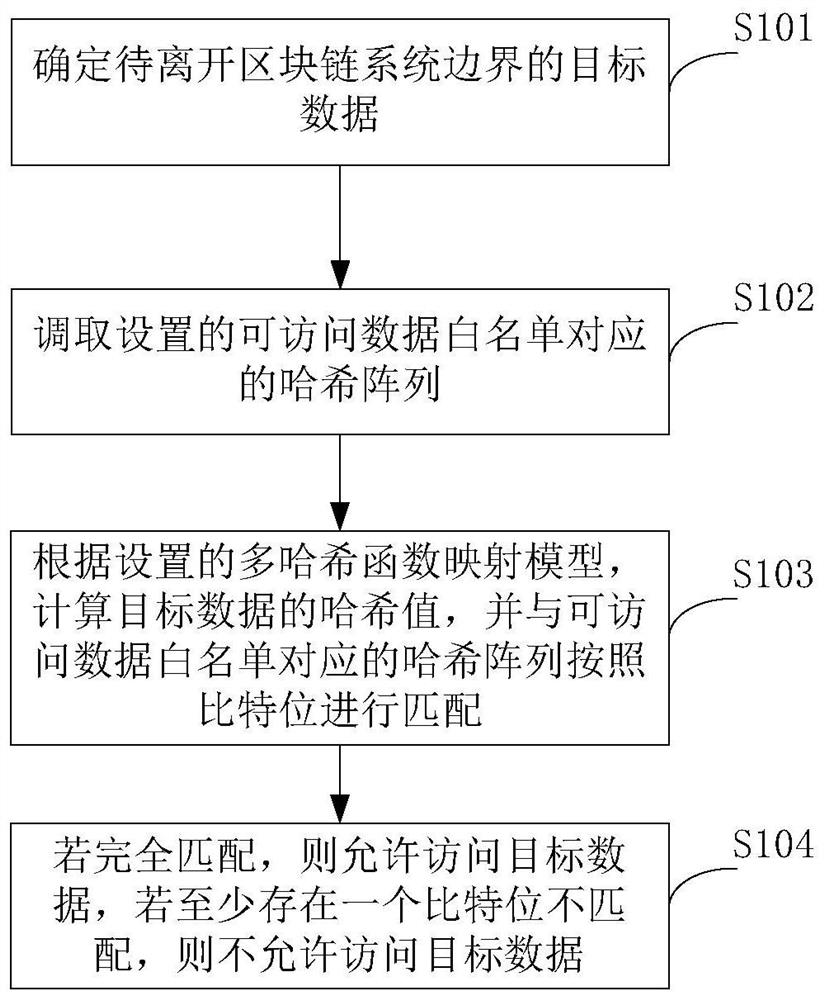
[0053] see figure 1 , the embodiment of the present application provides a monitoring method for data access based on a whitelist, including:
[0054] S101: Determine the target data to be left at the boundary of the blockchain system;
[0055] In this embodiment, the blockchain system boundary can be the alliance chain boundary, the public chain boundary, and the private chain boundary.
[0056] Optionally, in a specific implementation manner, the target data to be left at the boundary of the blockchain system includes sensitive data and / or non-sensitive data;
[0057] After determining the target data to leave the boundary of the blockchain system, it includes: parsing sensitive data and / or non-sensitive data from the target data to leave the boundary of the blockchain system.
[0058] For example, financial-related data, ID number, etc., are sensitive data, and user consumption data habits, etc., are non-sensitive data. Through this effective classification of sensitive an...
Embodiment 2
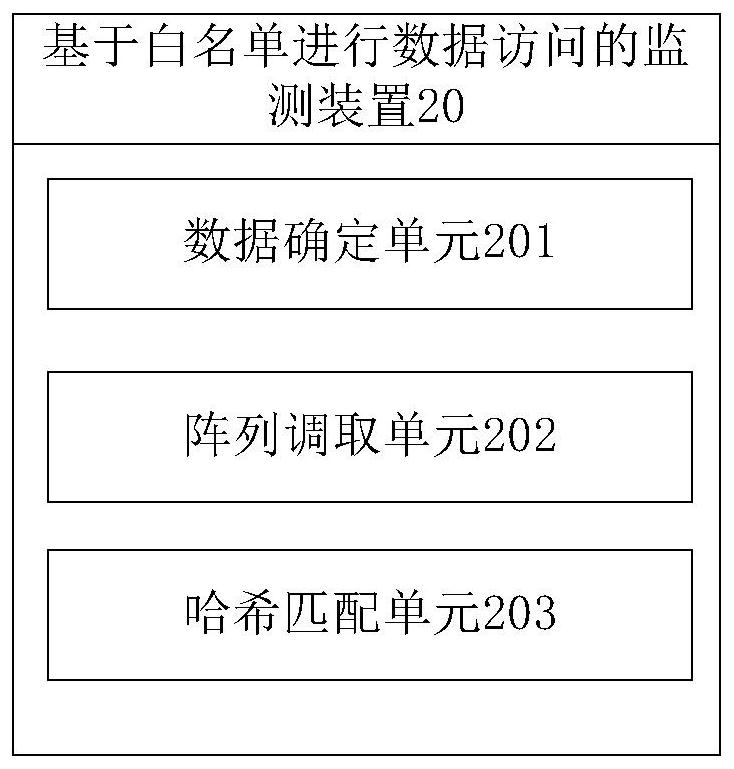
[0095] see figure 2 , the embodiment of the present application provides a monitoring device 20 for data access based on a whitelist, including:
[0096] A data determination unit 201, configured to determine target data to be left at the boundary of the blockchain system;
[0097] An array calling unit 202, configured to call a hash array corresponding to the set accessible data whitelist;
[0098] The hash matching unit 203 is configured to calculate the hash value of the target data according to the set multi-hash function mapping model, and match the hash array corresponding to the accessible data whitelist according to bits;
[0099] If there is an exact match, access to the target data is allowed, and if there is at least one bit mismatch, access to the target data is not allowed.
[0100] The specific instructions are as follows:
[0101] A data determination unit 201, configured to determine target data to be left at the boundary of the blockchain system;
[0102]...
Embodiment 3
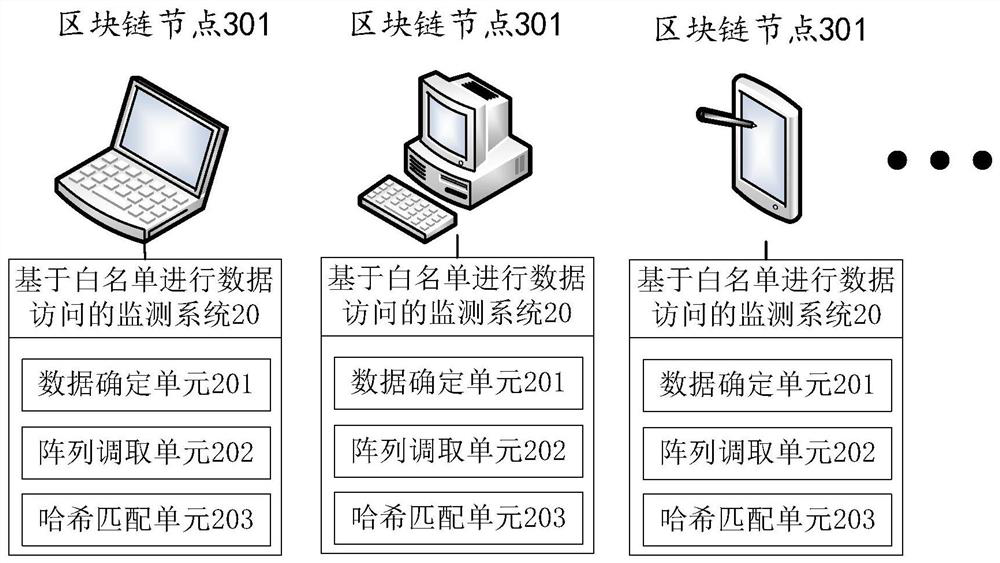
[0142] see image 3 , the embodiment of the present application provides a blockchain system 30, including: a plurality of blockchain nodes 301, and each blockchain node 301 is provided with a monitoring device 20 for data access based on a whitelist, which includes:
[0143] A data determination unit 201, configured to determine target data to be left at the boundary of the blockchain system;
[0144] An array calling unit 202, configured to call a hash array corresponding to the set accessible data whitelist;
[0145] The hash matching unit 203 is configured to calculate the hash value of the target data according to the set multi-hash function mapping model, and match the hash array corresponding to the accessible data whitelist according to bits;
[0146] If there is an exact match, access to the target data is allowed, and if there is at least one bit mismatch, access to the target data is not allowed.
[0147] The specific instructions are as follows:
[0148] A data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com