Dynamic identity authentication method and device, server and storage medium
A technology for identity authentication and identity authentication results, which is applied in the fields of dynamic identity authentication methods, servers and storage media, and devices, and can solve the problems of complex terminals and unsuitable authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
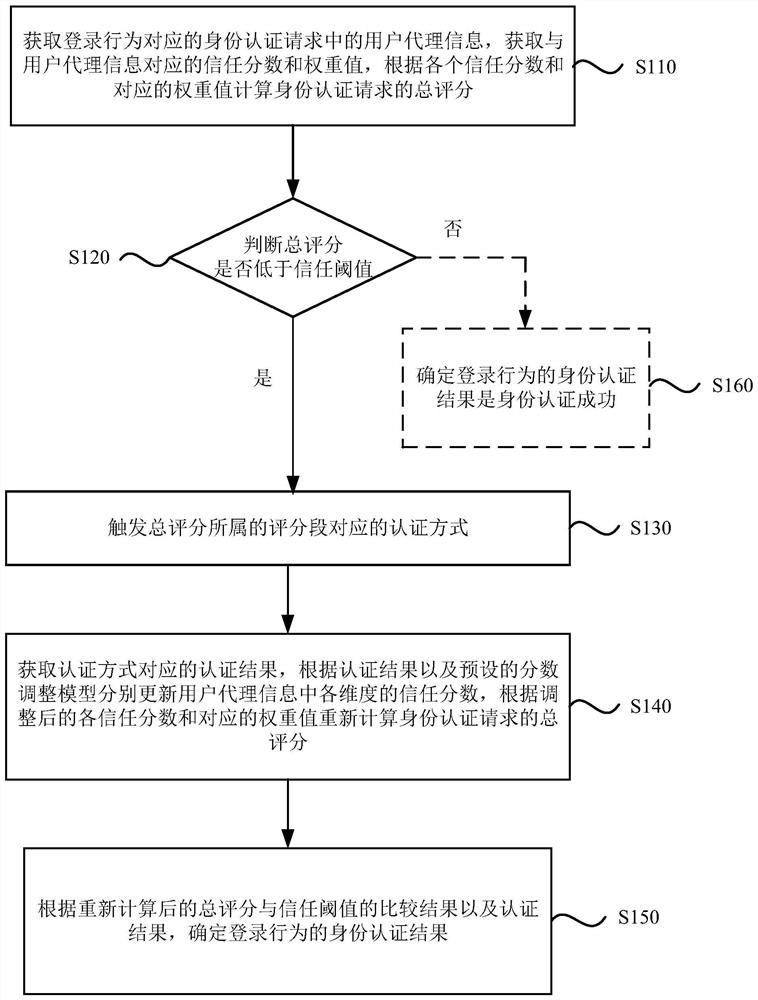
[0028] figure 1 It is a flow chart of a dynamic identity authentication method provided by Embodiment 1 of the present invention. This embodiment can be applied to perform identity authentication on the obtained login behavior, and judge whether to allow login according to the identity authentication result. This method can be implemented by dynamic The identity authentication device can be implemented by means of software and / or hardware. The device can be configured in the server. Such as figure 1 As shown, the method includes:
[0029] Step S110, obtain the user agent information in the identity authentication request corresponding to the login behavior, obtain the trust score and weight value corresponding to the user agent information, and calculate the total score of the identity authentication request according to each trust score and the corresponding weight value.
[0030] The login behavior may be a behavior generated based on a user account logging into the appli...
Embodiment 2
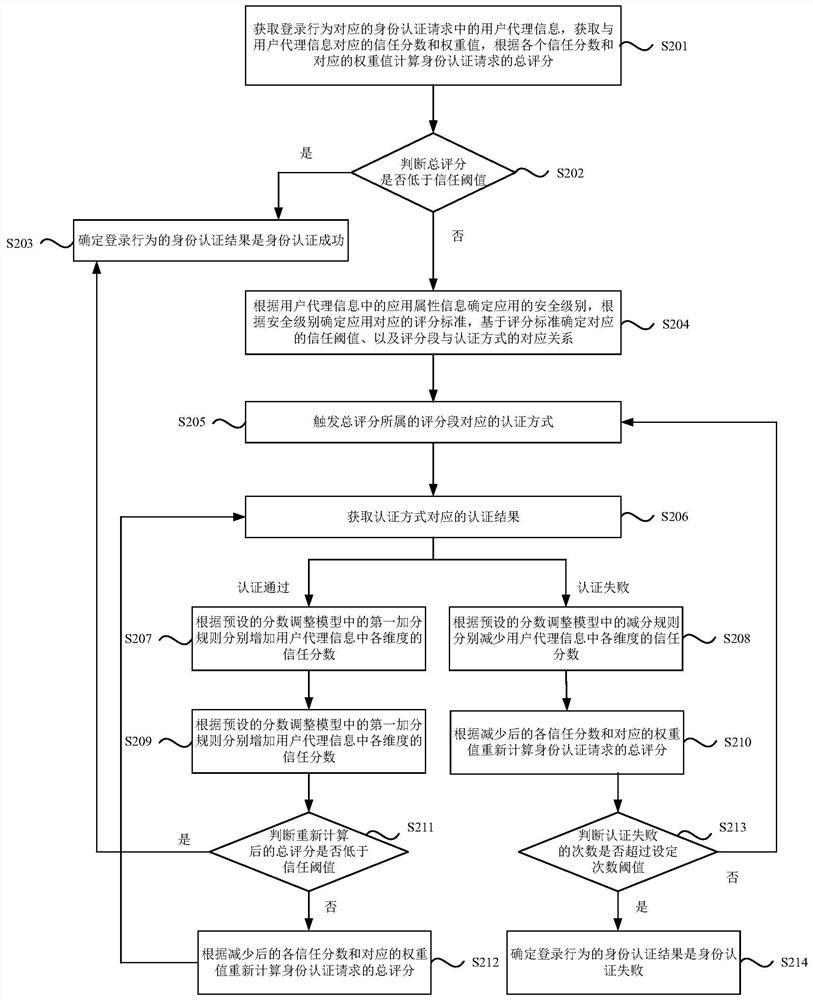
[0051] figure 2 It is a flow chart of another dynamic identity authentication method provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the above embodiments, as shown in figure 2 As shown, the method includes:
[0052] Step S201. Obtain the user agent information in the identity authentication request corresponding to the login behavior, obtain the trust score and weight value corresponding to the user agent information, and calculate the total score of the identity authentication request according to each trust score and the corresponding weight value.
[0053] Wherein, the user agent information is determined based on login information and application attribute information.
[0054] Step S202, determine whether the total score is lower than the trust threshold, if yes, execute step S203, otherwise, execute step S204.
[0055] Step S203, determining that the identity authentication result of the login behavior is that the iden...
Embodiment 3
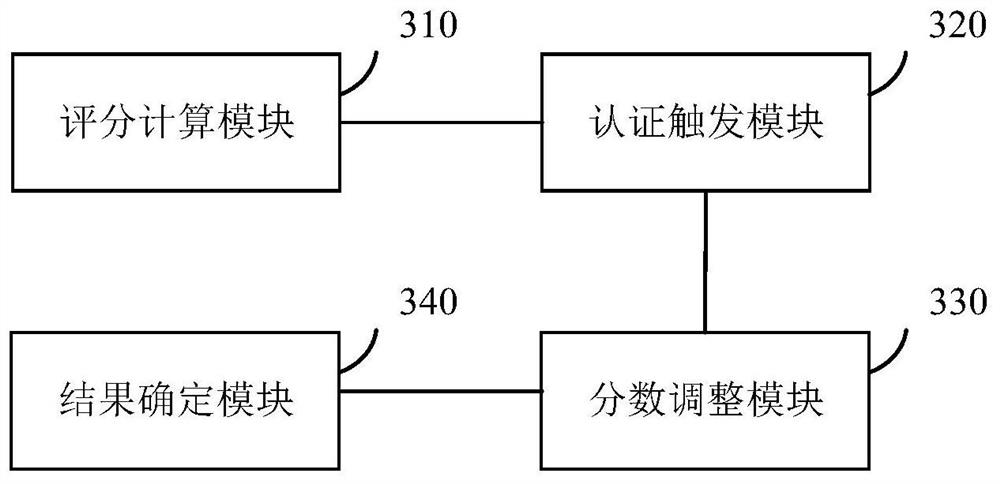
[0103] image 3 It is a schematic structural diagram of a dynamic identity authentication device provided by Embodiment 3 of the present invention. The device can be implemented by software and / or hardware, and generally can be integrated in a server, and can implement dynamic identity authentication for login behavior by implementing a dynamic identity authentication method, thereby improving the security of identity authentication. Such as image 3 As shown, the device includes:
[0104] The score calculation module 310 is configured to obtain user agent information in the identity authentication request corresponding to the login behavior, obtain trust scores and weight values corresponding to the user agent information, and calculate the described trust scores and corresponding weight values according to each of the trust scores and corresponding weight values. A total score of identity authentication requests, wherein the user agent information is determined based o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com