Computer-oriented symmetric password formalized description method and system
A formal description, symmetric encryption technology, applied in encryption devices with shift registers/memory, digital data authentication, etc., can solve the problem of low efficiency of symmetric encryption algorithm implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
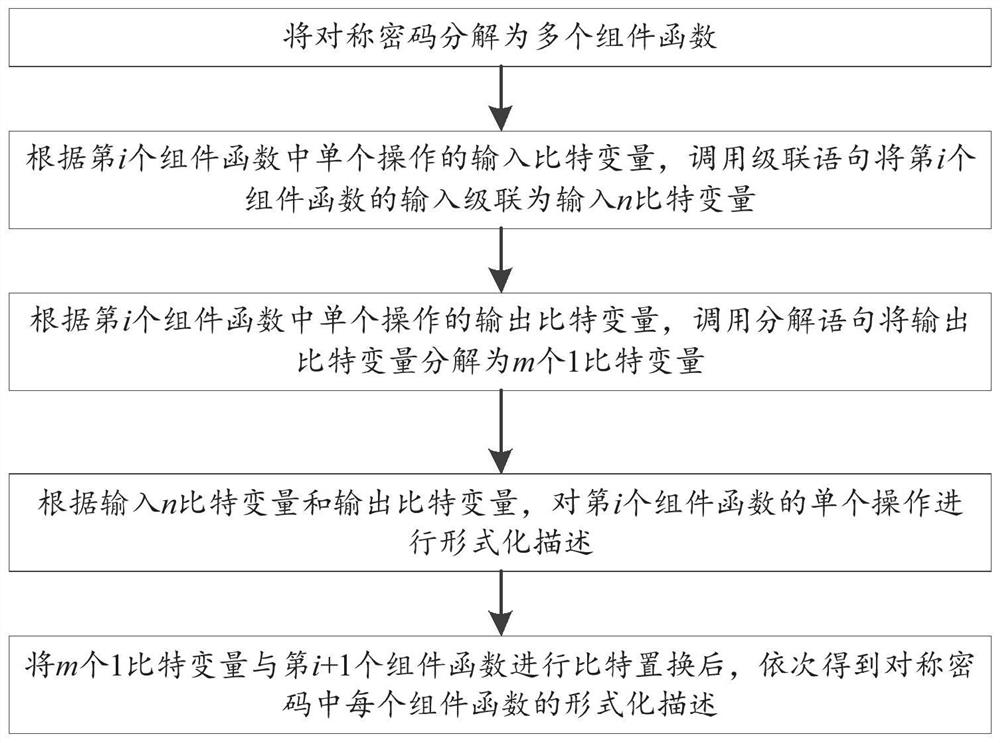
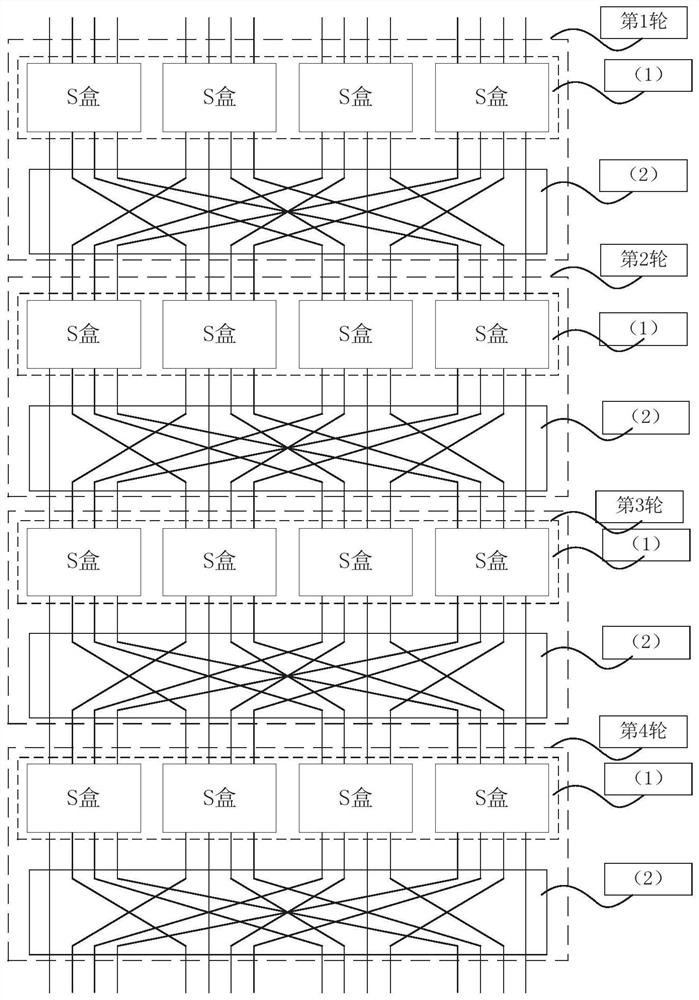
[0051] like figure 1 As shown, this embodiment provides a computer-oriented symmetric cryptographic formal description method, including:
[0052] S1: Decompose a symmetric cipher into multiple component functions;
[0053] S2: According to the input bit variable of the single operation in the ith component function, call the cascade statement to cascade the input of the ith component function into the input n 1 bit variable;
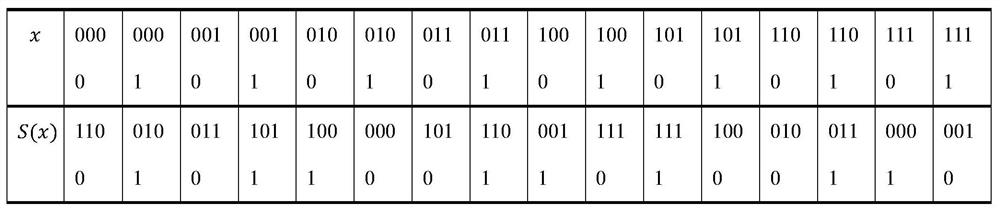
[0054] S3: According to the output bit variable of a single operation in the i-th component function, call the decomposition statement to decompose the output bit variable into n 2 a 1-bit variable;
[0055] S4: According to the input n 1 Bit variables and output bit variables, which formally describe the single operation of the i-th component function;
[0056] S5: put n 2 After the bit permutation of the 1-bit variable and the i+1th component function, the formal description of each component function in the symmetric cipher is obtained in turn....
Embodiment 2
[0158] This embodiment provides a computer-oriented symmetric cryptographic formal description system, including:
[0159] A decomposition module for decomposing a symmetric cipher into multiple component functions;
[0160] The cascade module is used to call the cascade statement to cascade the input of the ith component function into the input n according to the input bit variable of the single operation in the ith component function 1 bit variable;
[0161] The decomposition module is used to decompose the output bit variable into n by calling the decomposition statement according to the output bit variable of a single operation in the ith component function 2 a 1-bit variable;
[0162] describe module for input n according to 1 Bit variables and output bit variables, which formally describe the single operation of the i-th component function;
[0163] iterative description module for converting n 2 After the bit permutation of the 1-bit variable and the i+1th componen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com