Digital product secure transaction system and method based on blockchain technology
A digital product and secure transaction technology, applied in the field of computer security, can solve problems such as reselling, leakage, transaction process control and data security and privacy protection cannot be guaranteed, to solve security problems, improve security, and improve auditability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
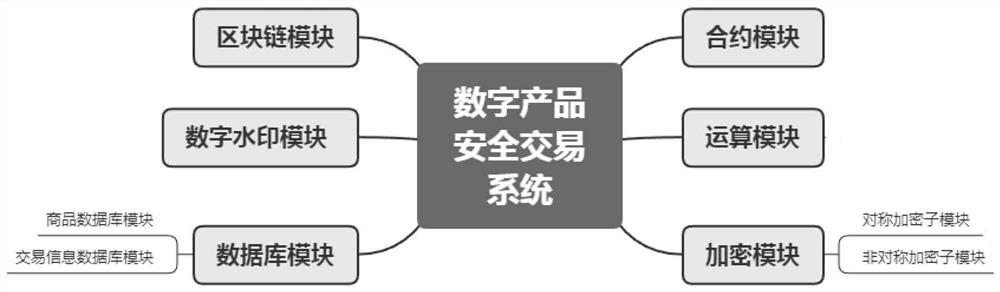
[0048] Such as figure 1 As shown, the digital product security transaction system based on blockchain technology of the present invention includes: a contract module, an operation module, an encryption module, a database module, a digital watermark module, and a blockchain module.
[0049] Specifically, the contract module is used to send commodity demander information and commodity demand information to the commodity database module in the database module.
[0050] The operation module is used to perform hash operation on the watermarked digital commodity to form a first hash value, and transmit the first hash value to the asymmetric encryption sub-module and the transaction database module.
[0051] The encryption module includes a symmetric encryption sub-module and the asymmetric encryption sub-module, the symmetric encryption sub-module is used to use the generated symmetric encryption key to encrypt the digital commodity containing the watermark to form a first ciphertex...
Embodiment 2
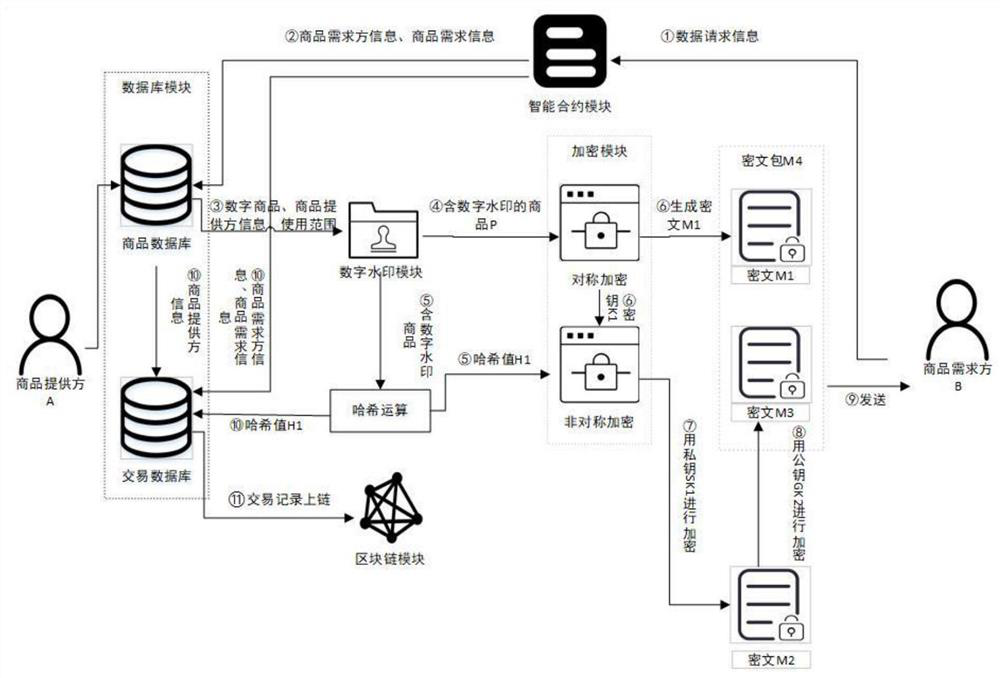
[0061] Such as Figure 3-4 As shown, this embodiment discloses a digital product security transaction method based on blockchain technology, including the following steps:
[0062] Step 1, after payment is completed, commodity demander B sends a data request message to the system and calls the contract module;
[0063] Step 2, the contract module sends the commodity demander information and commodity demand information to the commodity database module in the database module;
[0064] Step 3, the commodity database module sends the digital commodity, commodity provider information and usage range information to the digital watermark module according to commodity demand information;
[0065] Step 4, the digital watermark module marks the product provider information and product use range information in the digital product in the form of data watermark; the digital watermark module transmits the watermarked digital product P to the symmetric encryption sub-module;
[0066] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com