Data security calculation method and system, computer equipment, storage medium and terminal
A computing method and data security technology, applied in the field of information security, can solve the problems of lack of evidence chain in traditional solutions, raising the threshold of blockchain, and inability to guarantee the credibility of data sources, so as to ensure data privacy and not leak, and improve the security of multi-party computing. , The effect of simplifying the data flow process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
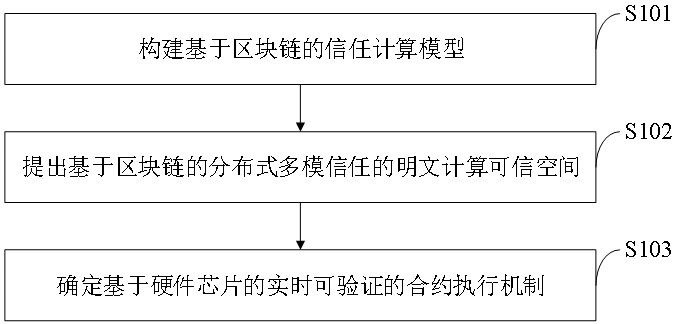
[0109] Aiming at the problems existing in the existing technology, the present invention provides a solution, hardware equipment, devices, and edge terminals based on block chain chips, software and hardware integration for data right confirmation, encrypted storage, and private data security multi-party computing. Improve privacy protection during data transfer and use.
[0110] Blockchain anonymous computing hardware (platform) is an integrated product of blockchain software and hardware developed for data authentication, secure storage, joint computing and trusted execution under the background of data sharing and use. The present invention proposes a blockchain-based trust computing model, and relies on cryptography (such as secure multi-party, zero-knowledge proof, etc.) technologies to realize the manageability, usability and verifiability of data under privacy protection. At the same time, the present invention provides users with a trusted distributed plaintext computi...
Embodiment 2
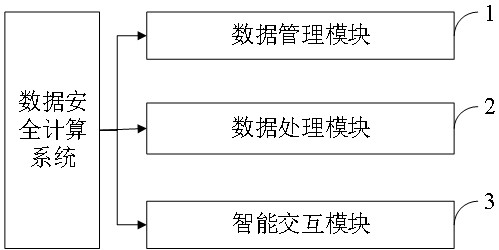
[0165] Blockchain anonymous computing hardware can realize the integration of software and hardware, and realize trusted collection of data sources, encrypted storage, verification of rights, and joint use. The blockchain anonymous computing hardware has a built-in node public and private key and a node startup program, and can build a private blockchain chain or connect to a blockchain (Ethereum) network with one click.
[0166] In one embodiment, such as Figure 5 Shown is the general process of data collection and processing by the blockchain anonymous computing hardware. The blockchain anonymous computing hardware is embedded with IoT chips, which can collect automation data, status data, and file data through technologies such as wireless networks (WIFI, 4G / 5G), sensors, wired connections, and radio frequency identification. In addition, the node is embedded with a GPS chip, which can realize the location tracking of the data source. The block chain anonymous computing ...
Embodiment 3
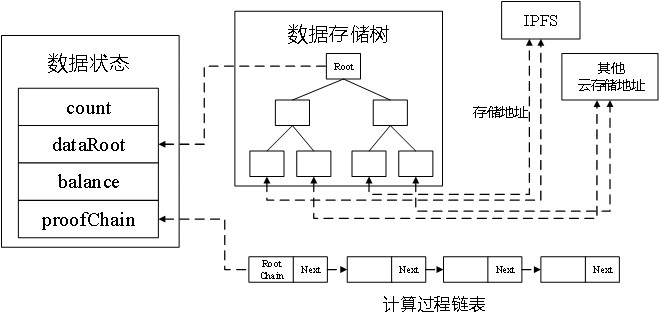
[0182] Blockchain anonymous computing hardware can perform secure privacy computing between data owners and data demanders. In one embodiment, such as Image 6 Shown is the joint calculation process between the data owner and the data demander. Through blockchain anonymous computing hardware, data owners and data demanders can conduct secure joint computing under the condition of protecting the privacy of data subjects.
[0183] Before describing the specific process of calculation, the initialization description is given first. As described in the first aspect of the summary of the invention, the following process will be sent to the blockchain network in the form of a transaction, which will be consensused by other nodes. The data address generated by the box for this data calculation is 0xdata_x, the count of this calculation is initialized to 0, the dataRoot is empty, the balance is empty, and the proofChain is initialized as the head node of this calculation process, wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com