Network attack defense method and device and electronic bidding and tendering transaction platform
A network attack and trading platform technology, applied in electrical components, transmission systems, etc., can solve the problem of network firewalls that are difficult to adapt to rapidly changing assault penetration attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
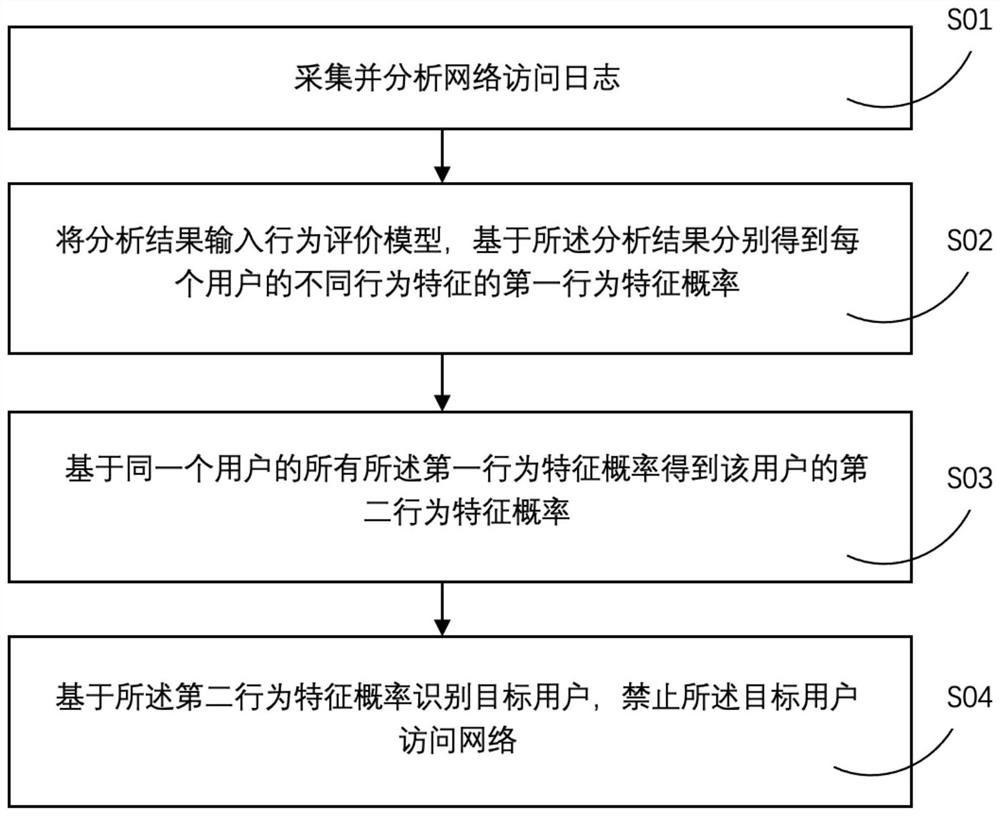
[0053] figure 1 Shown is a schematic flowchart of a network attack defense method provided by an embodiment of the present invention.
[0054] refer to figure 1 , this embodiment provides a network attack defense method, the network attack defense method comprising:
[0055] Step S01: Collect and analyze network access logs. Collect the original access log text of the network, and parse the access log. The parsed access log has structured data grouped by user IP.
[0056] Step S02: Input the analysis results into the behavior evaluation model, and obtain the first behavior characteristic probabilities of different behavior characteristics of each user based on the analysis results. Wherein, before inputting the analysis results into the behavior evaluation model, the behavior evaluation model needs to be established. Optionally, the method for establishing the behavior evaluation model includes: summarizing the first behavior characteristic probabilities of all the target u...
Embodiment 2
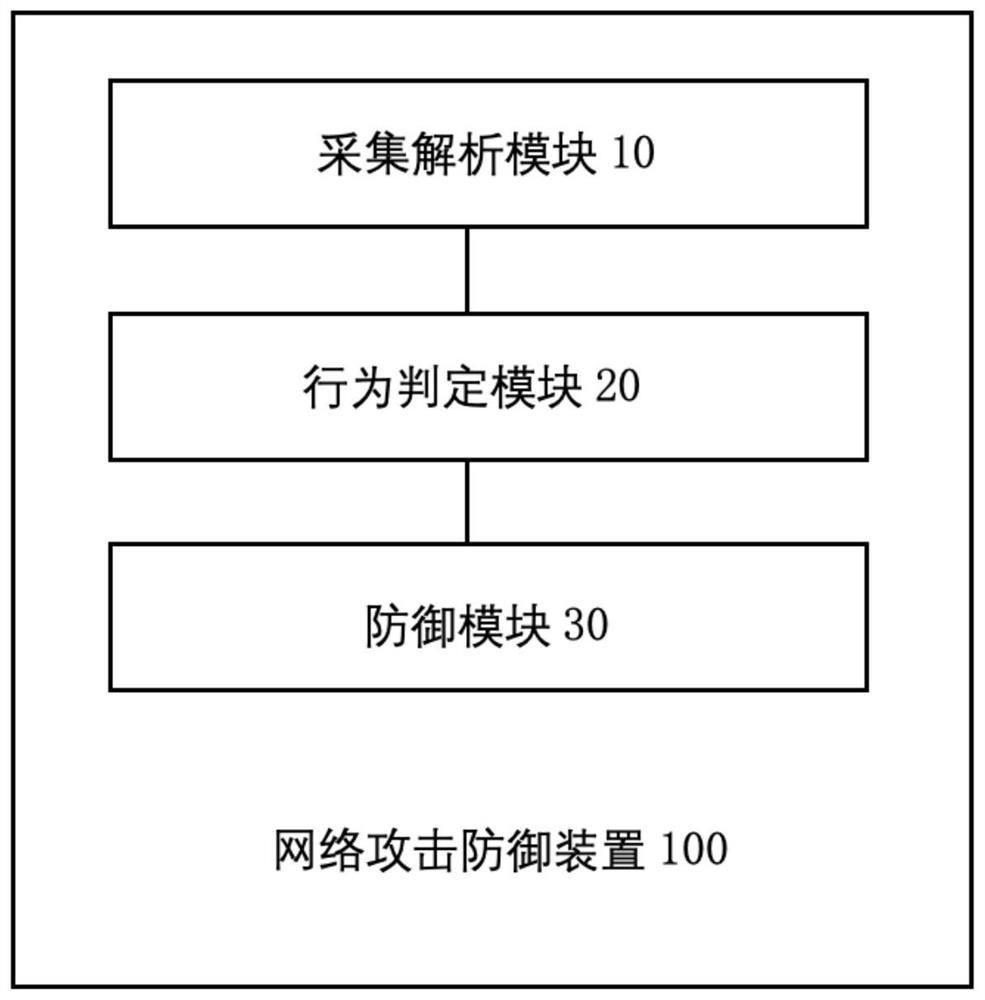
[0071] figure 2 Shown is a schematic structural diagram of a network attack defense device provided by an embodiment of the present invention.
[0072] refer to figure 2 In one embodiment of the present invention, a network attack defense device 100 is provided, and the network attack defense device 100 includes: a collection and analysis module 10 , a behavior determination module 20 and a defense module 30 . Wherein, the function of collection and analysis module 10 is to collect and analyze the network access log; the function of behavior determination module 20 is to input the analysis results into the behavior evaluation model, and obtain the first behavior characteristics of different behavior characteristics of each user based on the analysis results respectively. Probability; obtain the second behavior characteristic probability of the user based on all the first behavior characteristic probabilities of the same user; identify the target user based on the second beh...
Embodiment 3
[0077] This embodiment provides an electronic bidding and bidding transaction platform, and the electronic bidding and bidding trading platform adopts the network attack defense method described in one of the above embodiments to defend against network attacks. Specifically, the steps are as follows:
[0078] Step 1: collecting and analyzing the access logs of the electronic bidding trading platform;
[0079] Step 2: Input the analysis results into the behavior evaluation model, and obtain the first behavior characteristic probabilities of different behavior characteristics of each user based on the analysis results;
[0080] Step 3: Obtain the second behavior characteristic probability of the user based on all the first behavior characteristic probabilities of the same user;
[0081] Step 4: Identify the target user based on the probability of the second behavior characteristic, and prohibit the target user from accessing the electronic bidding trading platform.
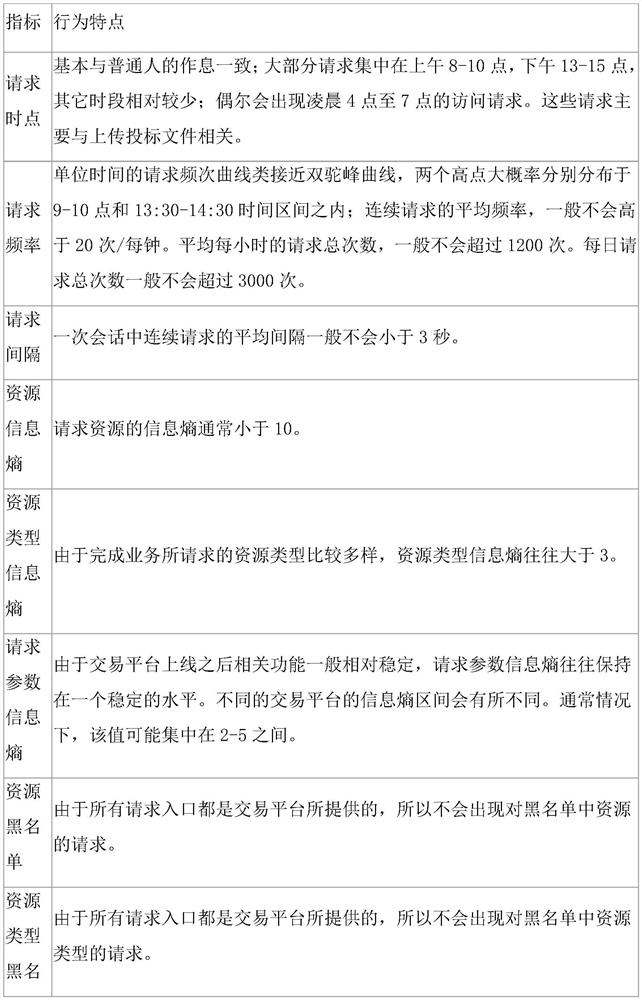
[0082] Wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com