Traceable verification two-dimensional code encryption anti-counterfeiting method
A technology of two-dimensional code and verification system, which is applied in the field of two-dimensional code encryption and anti-counterfeiting, which can solve the problem that anti-counterfeiting technology cannot solve the problem of counterfeiting damage to genuine brands, and achieve the effect of reducing the cost of counterfeiting and increasing the cost of counterfeiting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
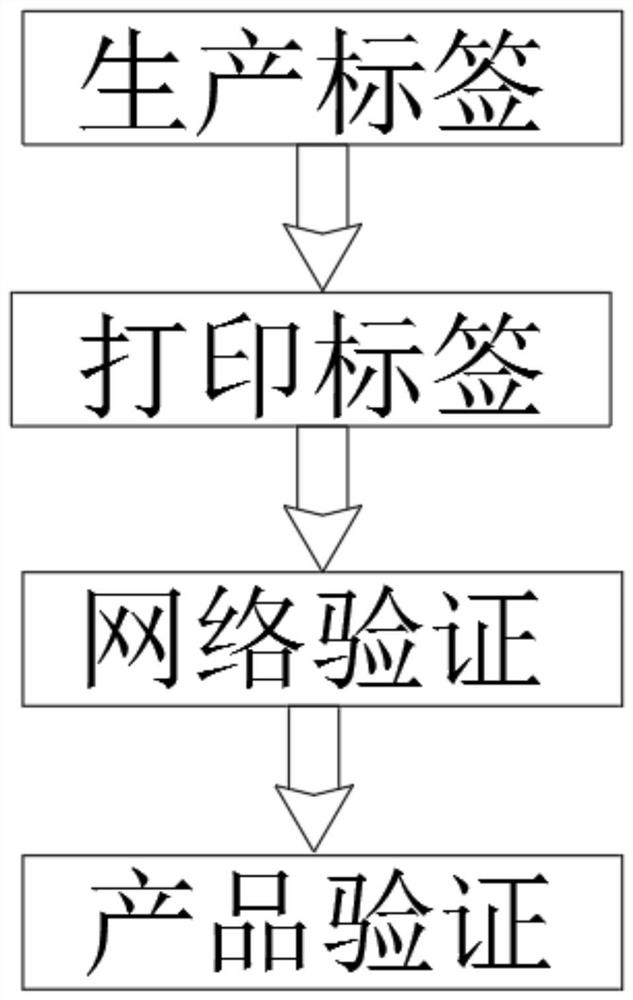
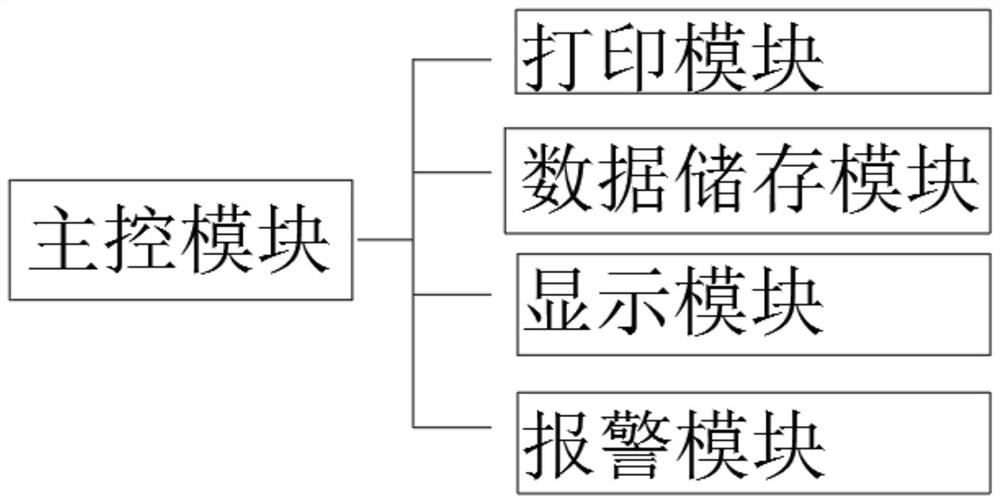
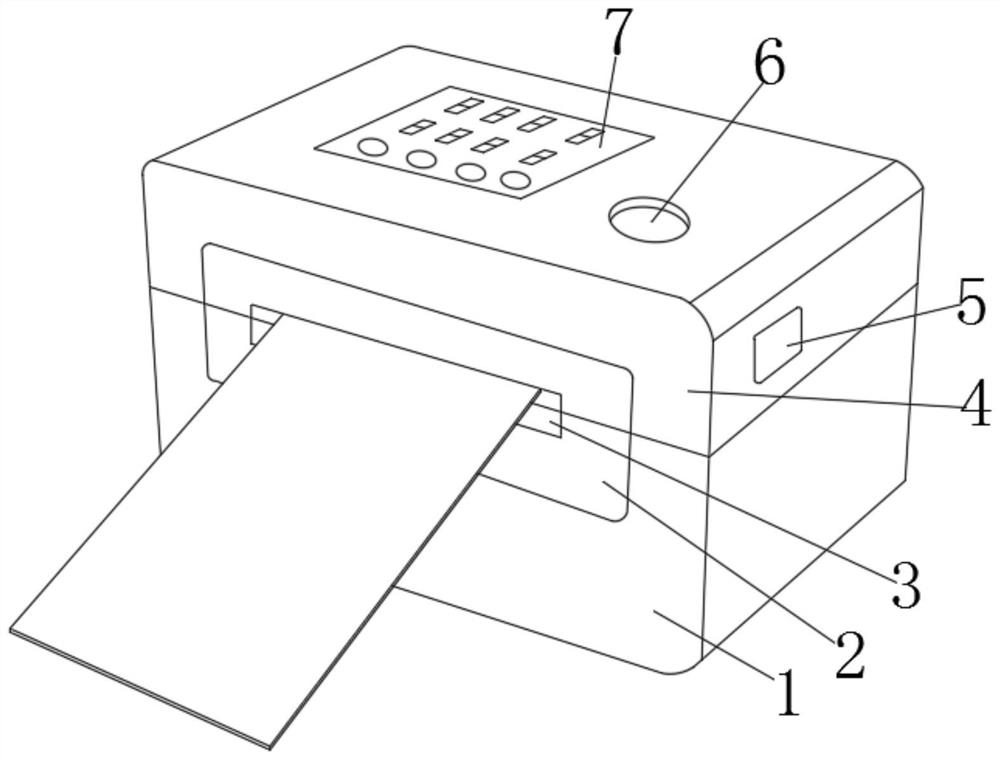
[0033] refer to Figure 1-3 , a traceable verified two-dimensional code encryption anti-counterfeiting method, comprising the following steps:
[0034] S1: Generate labels, and automatically generate labels through the manufacturer's terminal equipment;
[0035] S2: Print labels, use the label printer to print the generated labels. The label machine needs to have a liquid crystal display when printing labels. It shows that the label being printed is a certain type of product from the manufacturer. The label machine automatically obtains the manufacturer’s product model information from the network when printing. Then send a label generation request to the network verification system;
[0036] S3: Network verification, verify the label through the network, check the authenticity, the network verification system uses the product model + time + random salt provided by the manufacturer to generate a two-dimensional code for logistics, send it to the label machine terminal, and th...
Embodiment 2
[0043] refer to Figure 1-3 , a traceable verified two-dimensional code encryption anti-counterfeiting method, comprising the following steps:
[0044]S1: Generate labels, and automatically generate labels through the manufacturer's terminal equipment;
[0045] S2: Print labels, use the label printer to print the generated labels. The label machine needs to have a liquid crystal display when printing labels. It shows that the label being printed is a certain type of product from the manufacturer. The label machine automatically obtains the manufacturer’s product model information from the network when printing. Then send a label generation request to the network verification system;
[0046] S3: Network verification, verify the label through the network, check the authenticity, the network verification system uses the product model + time + random salt provided by the manufacturer to generate a two-dimensional code for logistics, send it to the label machine terminal, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com