Identity authentication method and device
A technology for identity authentication and identity authentication results, applied in the field of identity authentication methods and devices, can solve problems such as inability to guarantee information security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
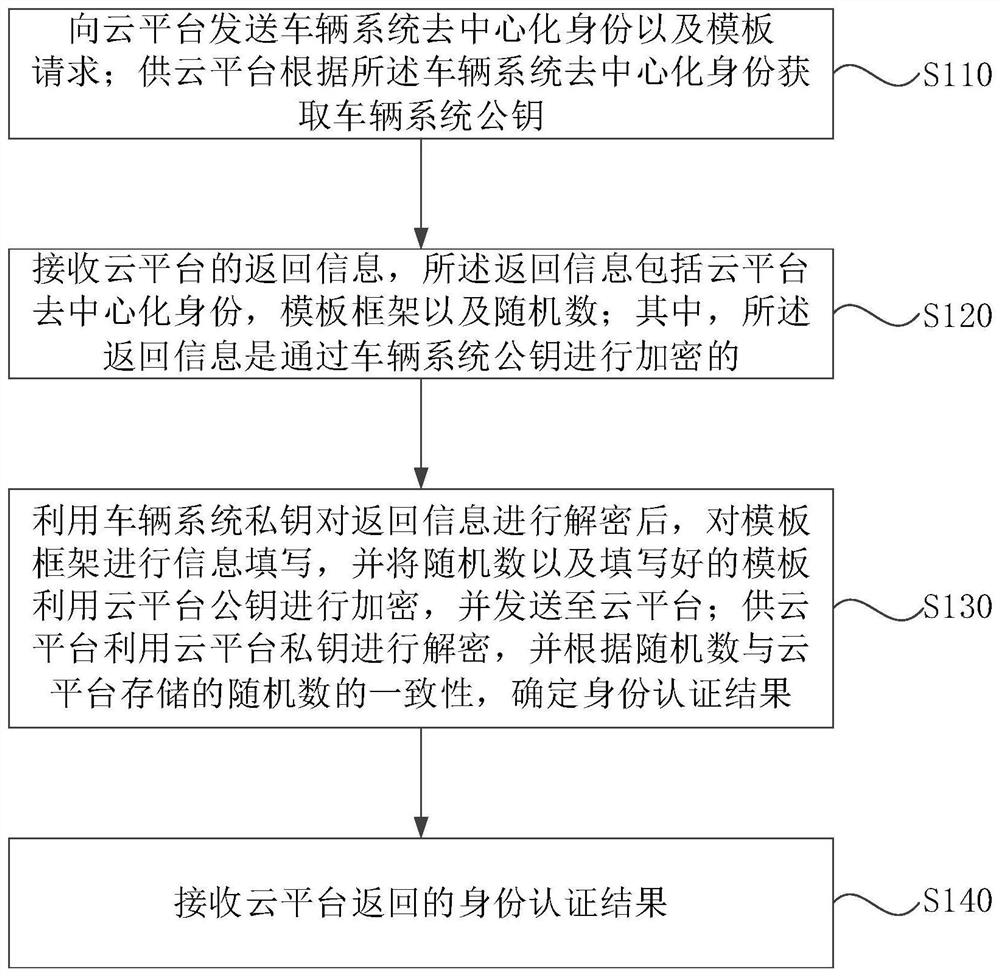
[0040] figure 1 It is a flow chart of the identity authentication method provided in Embodiment 1 of the present application. This embodiment is applicable to the situation of information interaction. The method can be executed by the identity authentication device provided in the embodiment of the present application. The device can be implemented by software and / or hardware and can be integrated into the vehicle system.
[0041] Such as figure 1 As shown, the identity authentication method includes:
[0042] S110. Send the vehicle system decentralized identity and a template request to the cloud platform; the cloud platform obtains the vehicle system public key according to the vehicle system decentralized identity.
[0043] Wherein, the vehicle system may be a system for managing and controlling vehicle information, such as a vehicle manufacturer or the like. Before the vehicle system sends the decentralized identity, the local public key can be uploaded to the chain, an...
Embodiment 2
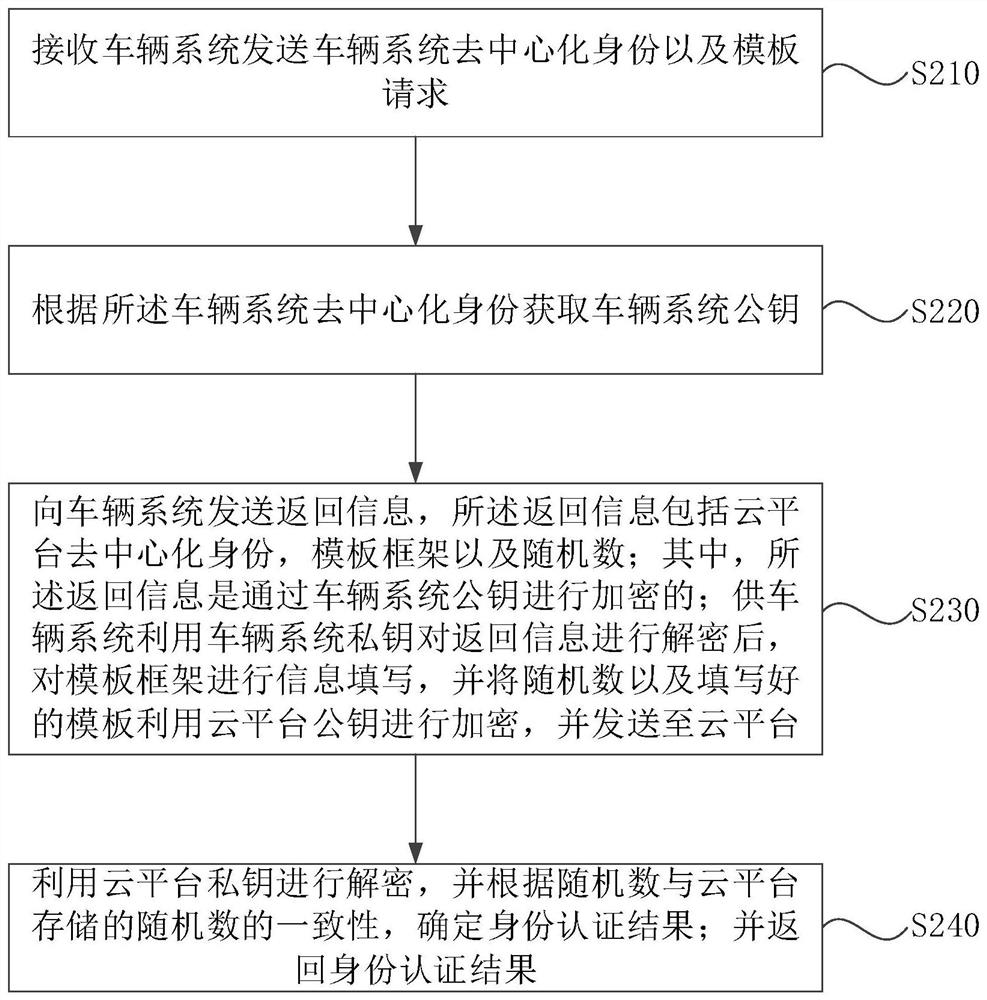
[0055] figure 2 It is a flow chart of the identity authentication method provided in Embodiment 2 of the present application. This embodiment is applicable to the situation of information interaction. The method can be executed by the identity authentication device provided in the embodiment of the present application. The device can be implemented by software and / or hardware way, and can be integrated in the cloud platform.
[0056] Such as figure 2 As shown, the identity authentication method includes:
[0057] S210. The receiving vehicle system sends the vehicle system decentralized identity and template request.
[0058] Among them, the cloud platform can receive the decentralized identity and template request sent by the vehicle system through the communication module.
[0059] S220. Obtain a vehicle system public key according to the vehicle system decentralized identity.
[0060] Among them, the decentralized identity of the vehicle system can be equivalent to the...
Embodiment 3
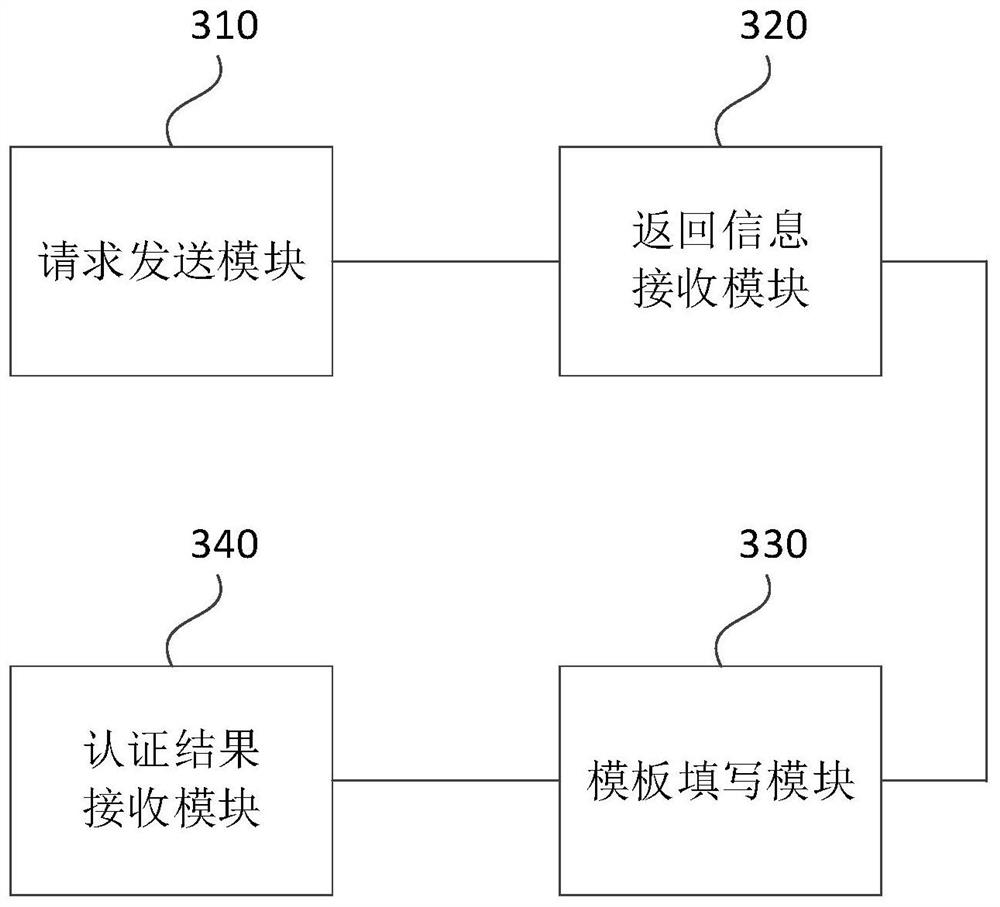
[0072] image 3 It is a schematic structural diagram of the identity authentication device provided in Embodiment 3 of the present application. Such as image 3 As shown, the identity authentication device is configured in a vehicle system, and the device includes:
[0073] The request sending module 310 is used to send the vehicle system decentralized identity and template request to the cloud platform; the cloud platform obtains the vehicle system public key according to the vehicle system decentralized identity;
[0074] The return information receiving module 320 is used to receive the return information of the cloud platform, and the return information includes the decentralized identity of the cloud platform, template framework and random numbers; wherein, the return information is encrypted by the public key of the vehicle system;
[0075] The template filling module 330 is used to use the private key of the vehicle system to decrypt the returned information, fill in ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap