Virtual key distribution method, server and distribution system
A technology of virtual key and distribution method, applied in instruments, time register, single input/output register, etc., can solve the problem of increasing hotel workload, affecting guest check-in experience, virtual key promotion and application inconvenience, etc. problems, to reduce labor and operating costs, facilitate application and promotion, and improve occupancy experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
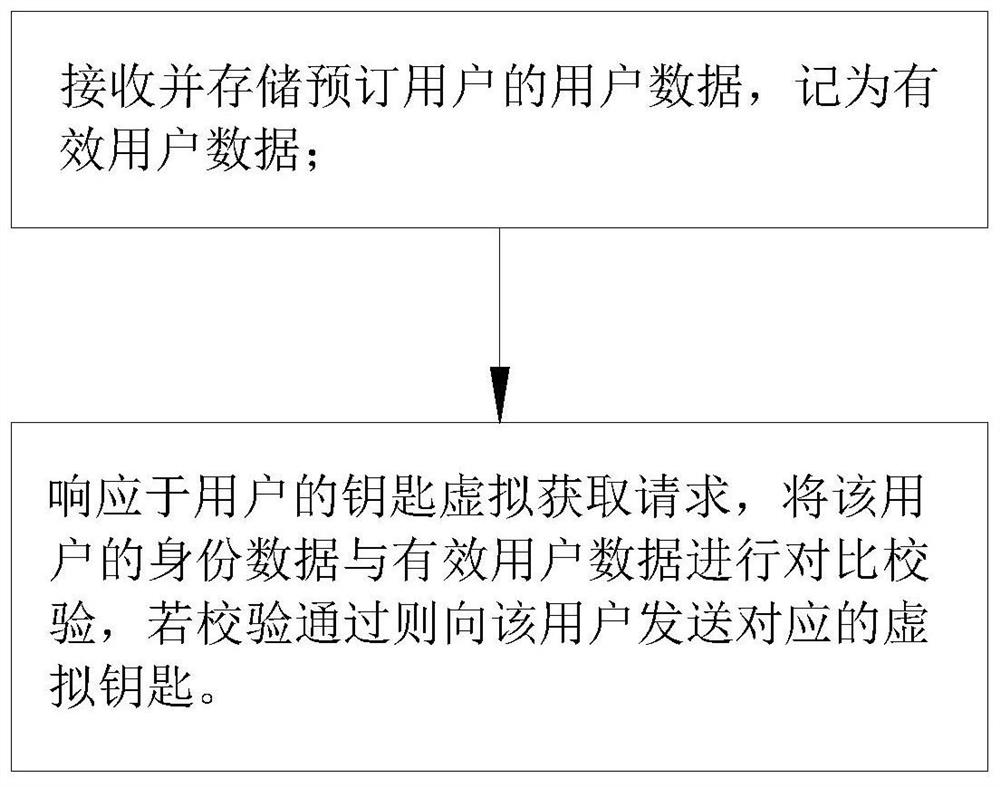
[0039] Such as figure 1 As shown, a method for distributing a virtual key according to the present invention includes the following steps:
[0040] Receive and store the user data of the subscribing user, and record it as valid user data; specifically, subscribing users represent different groups of people according to different application scenarios, and the ways and conditions for completing the booking are also different. Exemplarily, in a hotel application scenario, a reservation user refers to a guest who has reserved a room in the hotel. Generally speaking, the condition for completing a reservation should be that the guest uploads the relevant identity information as required and specifies the room to be booked And paid the corresponding room fee, it is considered that the user has completed the reservation, the user is regarded as the reserva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com