Network vulnerability scanning method and device
A scanning method and technology of a scanning device are applied in the field of network security and can solve the problems of low scanning efficiency, low efficiency of manual scanning methods, poor applicability and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
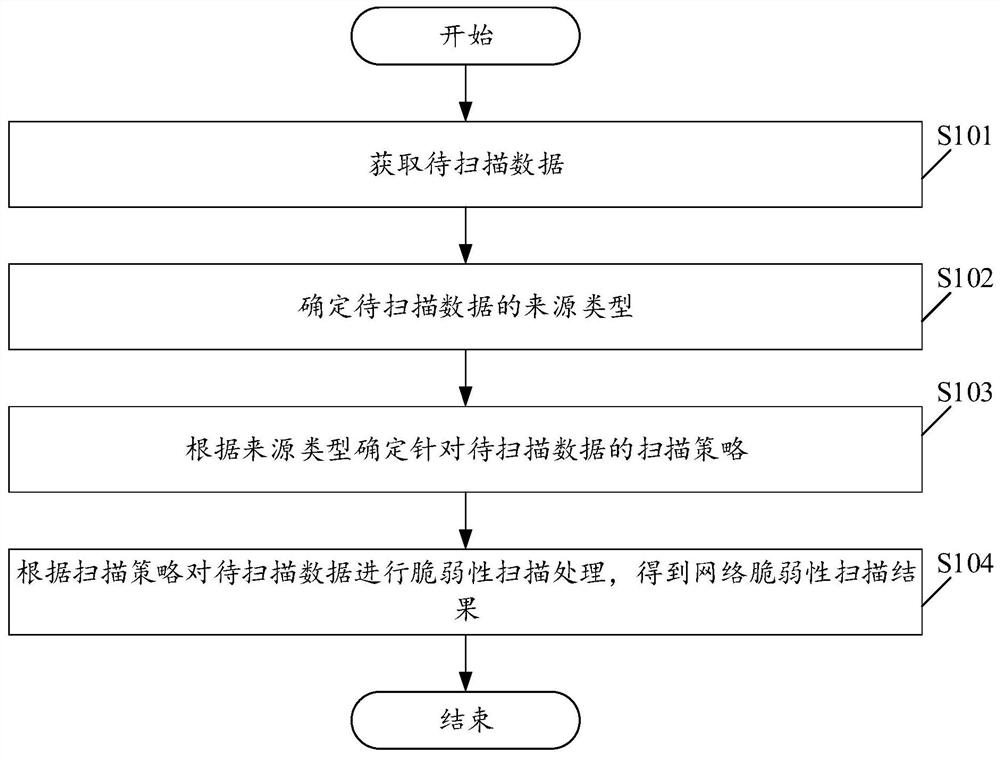
[0055] Please see figure 1 , figure 1A schematic flowchart of a network vulnerability scanning method is provided for the embodiment of the present application. Wherein, the network vulnerability scanning method includes:
[0056] S101. Obtain data to be scanned.
[0057] In the embodiment of the present application, the data to be scanned may be log data, scanning target data, etc., which is not limited in the embodiment of the present application.
[0058] In this embodiment of the present application, the scanning target is preset, and specifically may be a network address target, such as a URL (Uniform Resource Locator, Uniform Resource Locator, Uniform Resource Locator) and the like.
[0059] In this embodiment of the present application, the subject of execution of the method may be a scanning device.
[0060] In the embodiment of the present application, the scanning device may be a computing device such as a computer or a server, which is not limited in this embodi...
Embodiment 2
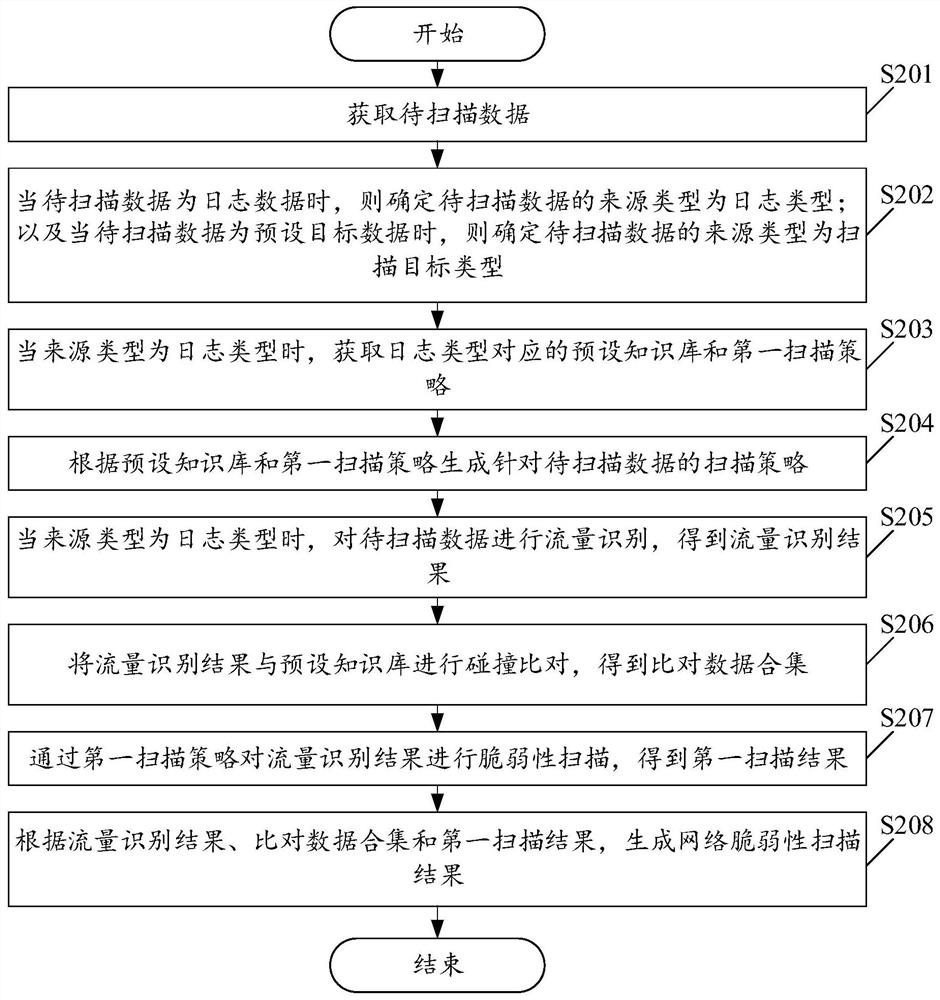
[0087] Please see figure 2 , figure 2 It is a schematic flowchart of a network vulnerability scanning method provided in the embodiment of the present application. Such as figure 2 As shown, wherein, the network vulnerability scanning method includes:
[0088] S201. Obtain data to be scanned.
[0089] S202. When the data to be scanned is log data, determine that the source type of the data to be scanned is a log type; and when the data to be scanned is preset target data, determine that the source type of the data to be scanned is a scan target type.
[0090] In the embodiment of the present application, the source type of the data to be scanned can be determined by implementing the above step S202.
[0091] S203. When the source type is a log type, acquire a preset knowledge base and a first scanning policy corresponding to the log type.
[0092] In this embodiment of the present application, before step S201, detection parameters may also be pre-configured, which are...
Embodiment 3
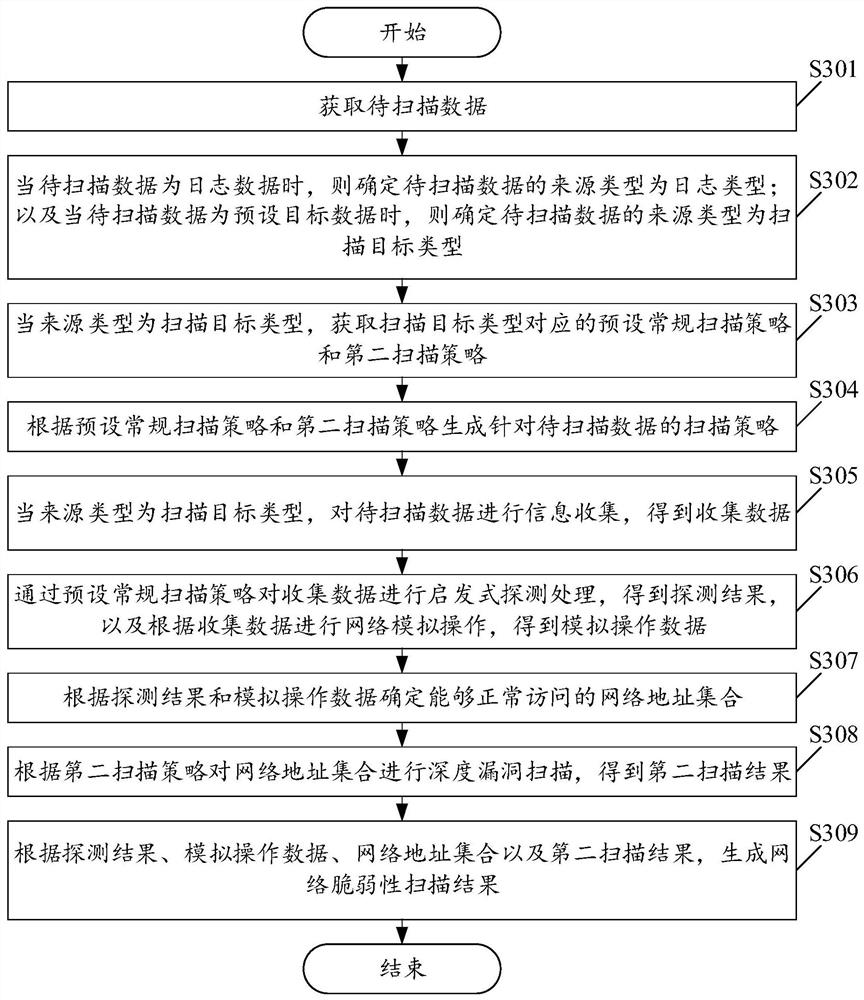
[0126] Please see image 3 , image 3 It is a schematic flowchart of a network vulnerability scanning method provided in the embodiment of the present application. Such as image 3 As shown, wherein, the network vulnerability scanning method includes:
[0127] S301. Obtain data to be scanned.
[0128] S302. When the data to be scanned is log data, determine that the source type of the data to be scanned is a log type; and when the data to be scanned is preset target data, determine that the source type of the data to be scanned is a scan target type.
[0129] In the embodiment of the present application, the source type of the data to be scanned can be determined by implementing the above step S302.
[0130] In the embodiment of the present application, when the source type is the scanning target type, it is the scanning target preset in the scanning device. After the scanning parameters are configured, a collection of scanning strategies will be loaded. For example, an i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com