A trust-based task scheduling method for mobile edge users
A trustworthy and task-based technology, applied in specific environment-based services, vehicle wireless communication services, communication between vehicles and infrastructure, etc., can solve the problem of being easily deceived, unable to evaluate trustworthiness, and unable to obtain mobile data collection Issues such as interactive behavior of the user can be solved to achieve the effect of improving objectivity and accuracy and increasing the rate of credible data collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
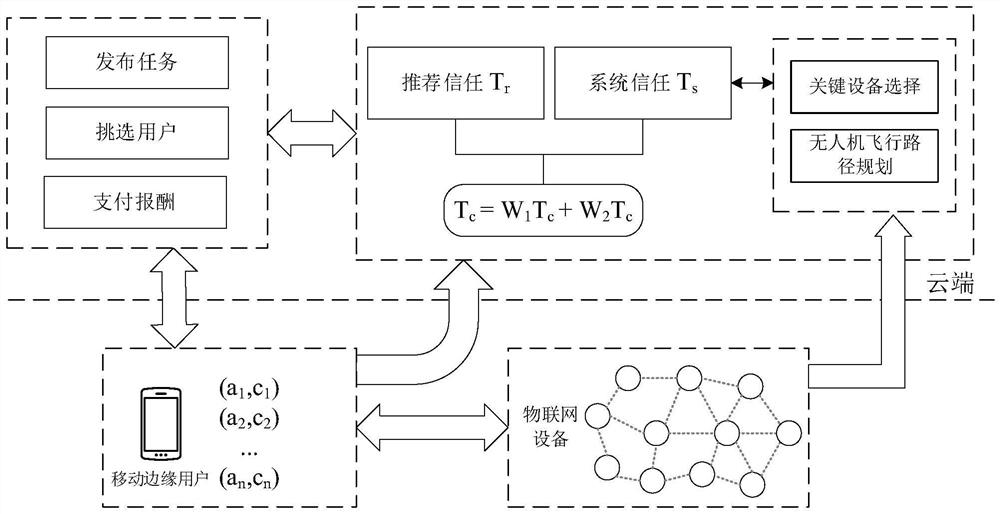
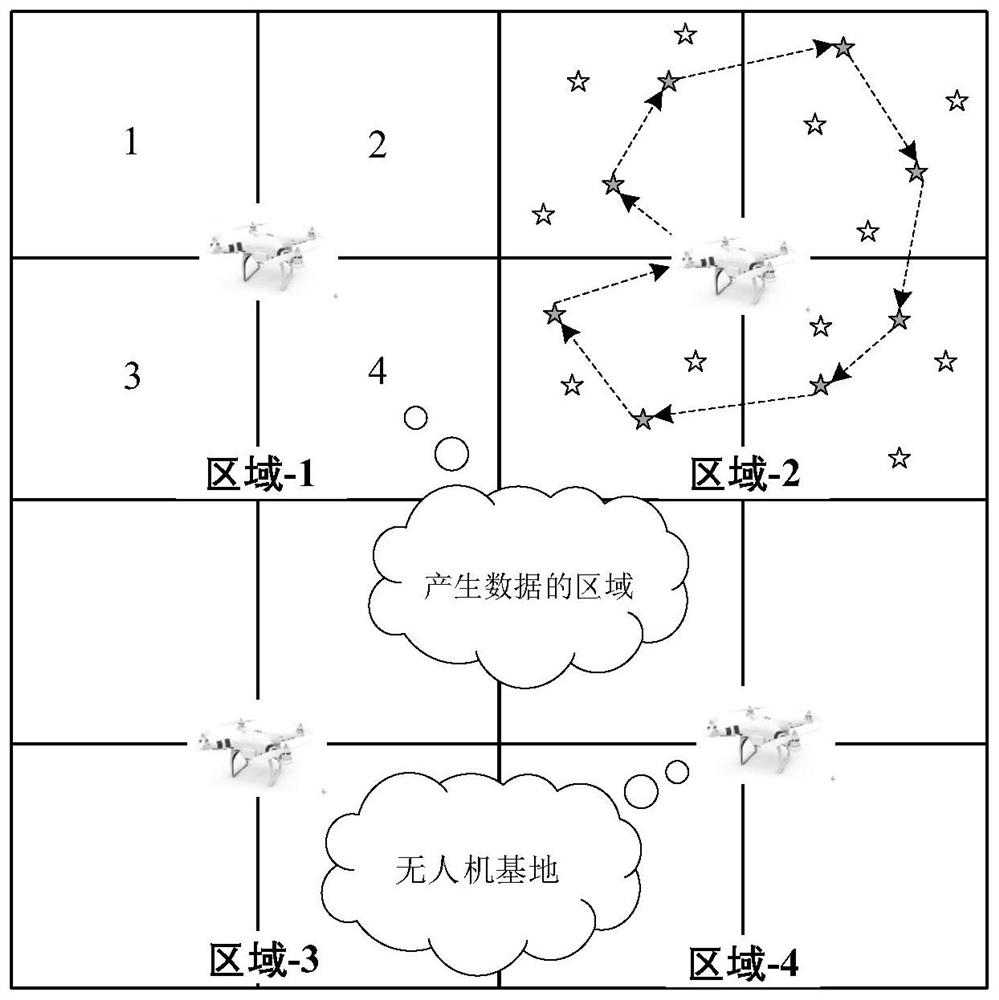
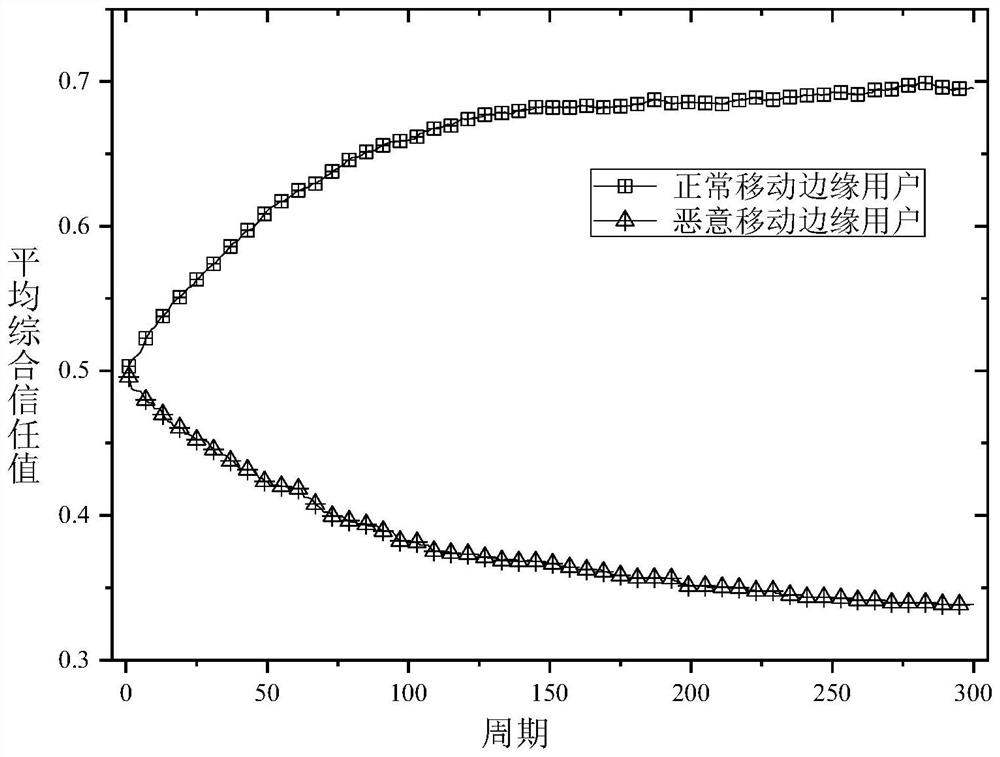
[0046] This embodiment is a task scheduling method for mobile edge users based on trust. First, the cloud publishes evaluation tasks to all available mobile edge users, and releases information about the network topology and the location of each IoT device in the network. After receiving the release task, interested mobile edge users will participate in the bidding, and the user's bidding value is B i =(a i , c i ), where a i Indicates the evaluation capability of mobile edge users, which is related to the number of IoT devices in the evaluation area of mobile edge users, c i Indicates the bidding price, that is, the expected remuneration of mobile edge users. Then, based on the greedy selection algorithm considering the trust degree, the cloud selects reliable users from the candidate mobile edge user set to perform the evaluation task. The spec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com