Trusted address generation method and system
A technology for address generation and trusted addresses, applied in digital data protection, computer security devices, structured data retrieval, etc., can solve problems such as technology and credit credibility, and achieve the effect of solving complexity and improving single use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
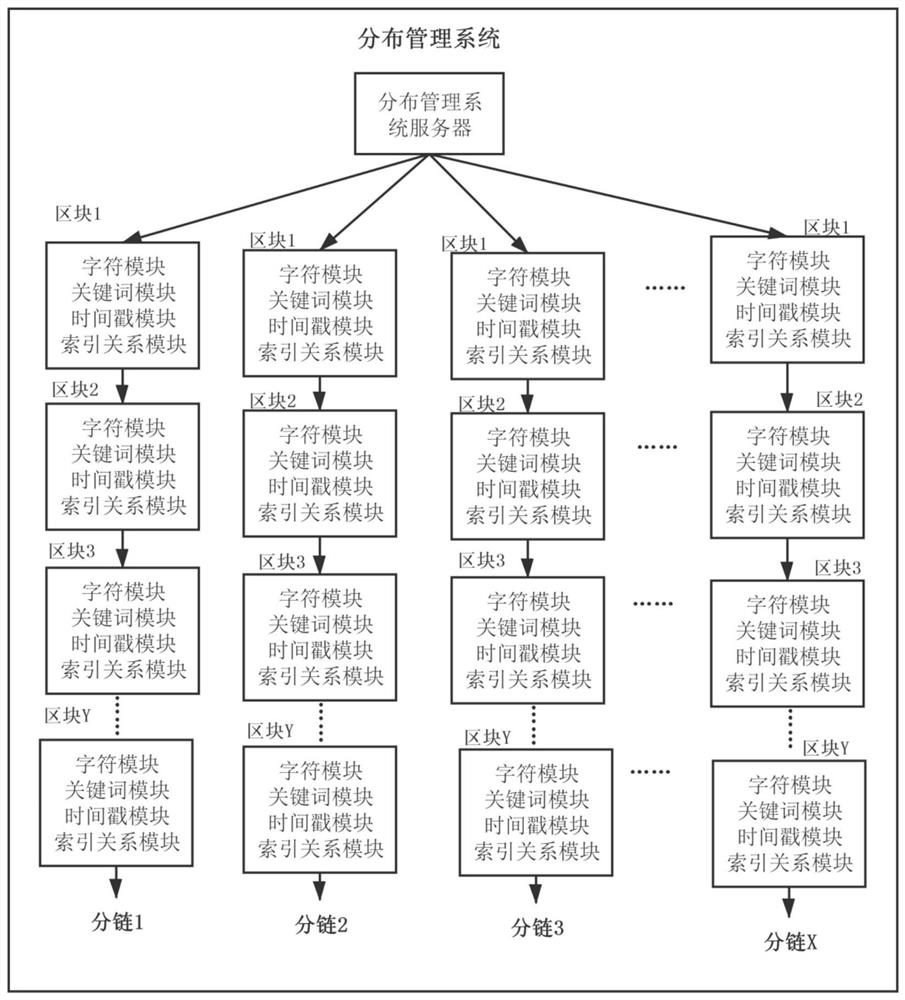
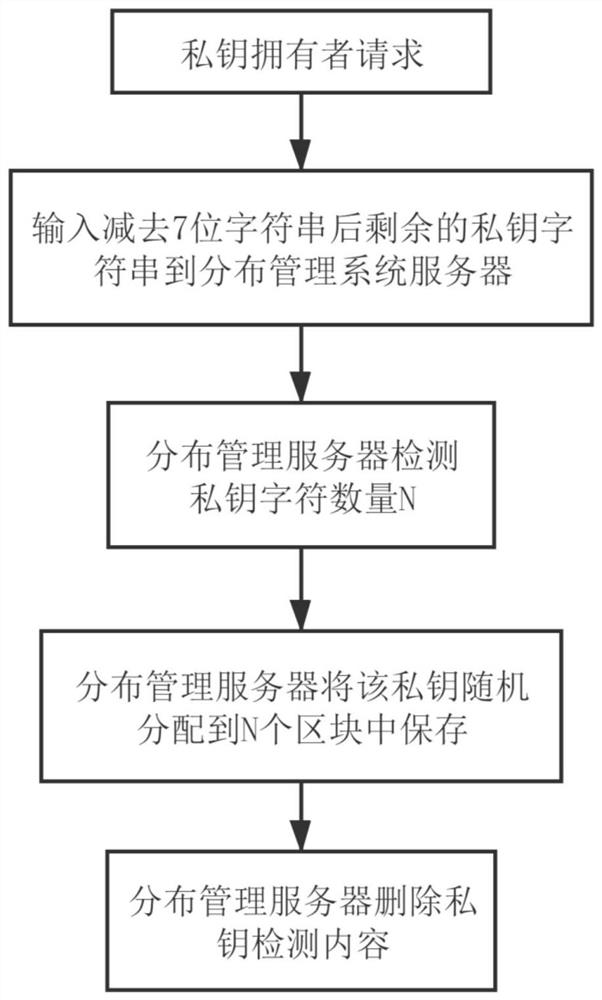
[0131] The technical scheme adopted by the present invention is to supplement the selection object of the private key, the selection object is extensive, and the ECDSA-secp256k1, SHA-256 and other algorithms are used to increase the confidentiality, and 1xin is combined on the basis of the algorithm to make the private key in the process of generating the address Credibility is further increased, and the trusted address involves the corresponding system, and the smart contract is configured for the trusted address, and a distributed management system is provided for the management of the private key of the trusted address. The present invention provides a technical solution to the above problems. The specific implementation is as follows:
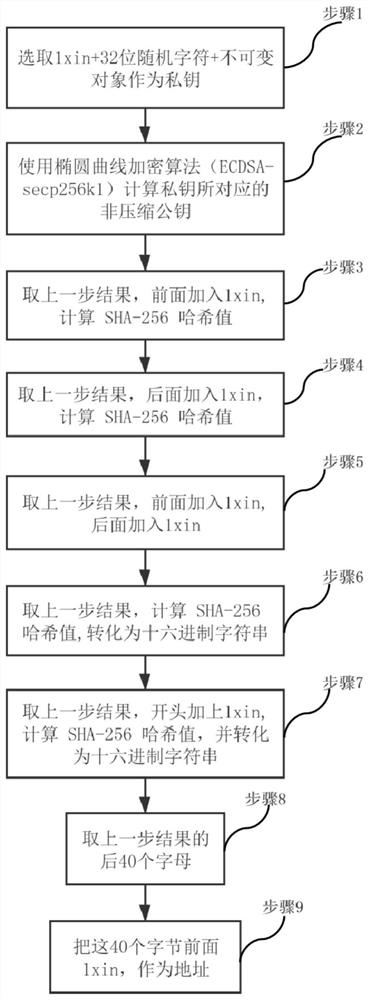
[0132] combined with figure 1 and Figure 5 A trusted address generation method is implemented, comprising the steps of:
[0133] Step 1. Select 1xin+32 random characters+immutable object as the private key;
[0134] Further immutable ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com