Acquired data protection method and system based on sandbox
A technology for collecting data and sandbox, which is applied in the field of data collection protection method and system based on sandbox to achieve the effect of protecting user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
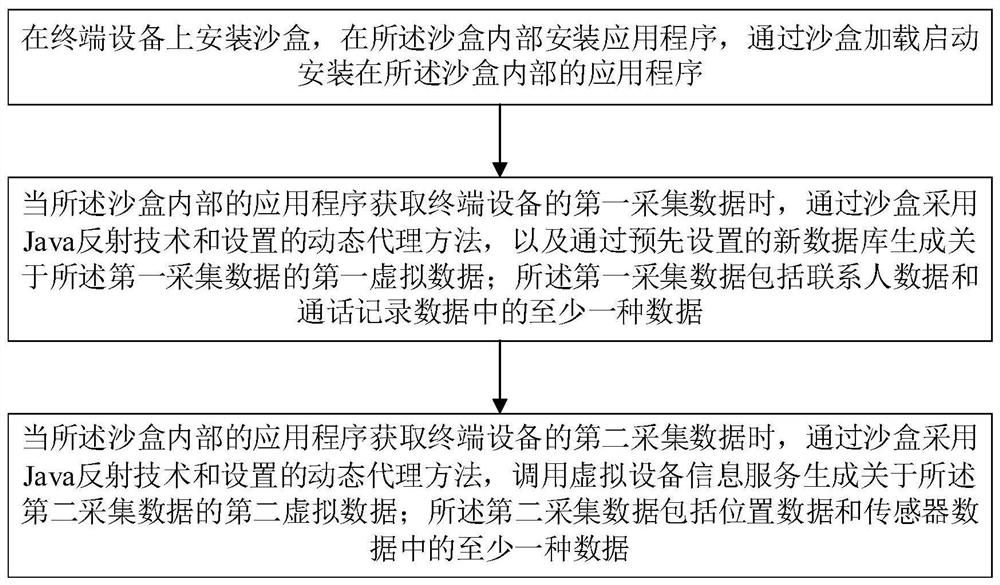
[0061]Based on the above embodiment, the difference from the above-described embodiment is, in the embodiment of the present invention, in step S102, further includes the following steps:
[0062]Through the sandbox, Java reflective technology and setting dynamic agent methods are used to generate new databases for the original storage database of the first acquisition data, including:
[0063]During the process of the application of the application inside the sandbox, the dynamic proxy object is obtained from the original storage database of the first acquisition data in the original storage database of the first acquisition data, and then through the dynamic proxy object The original storage database is transformed, and the transformed data is inserted into the original storage database to generate a new database; in the new database, use the fake data table to replace the original real data table, and re-create the true data table.
[0064]In actual applications, the contact data is used ...
Embodiment 3
[0066]Based on the above embodiments, different from the above-described embodiments in that the present invention, the dynamic proxy method of Java reflection technology and settings through the sandbox, as well as the new database, and generated by pre-set new databases The first virtual data of the first acquisition data includes:
[0067]Using the Java Reflection Technology and Dynamic Agent Method through the sandbox, you get the dynamic proxy object from the new database, by querying the fake data table in the new database, data corresponding to the first acquisition data, according to the data, according to the first The first virtual data of the data is collected.
[0068]It should be noted that since the embodiment of the present invention performs a database transformation when the contact is inserted, the contact phone number queried at this time is the pre-saved fake phone number that has been saved first, and it has completed the privacy of the contact data. Protection, becau...
Embodiment 4
[0070]On the basis of the above embodiment, the difference from the above-described embodiment is, in the embodiment, the present invention, the dynamic agent method of Java reflection technology and the setting dynamic proxy method, calling the virtual equipment information service to generate the first Second, the second virtual data of the data, including:
[0071]Java reflection techniques are used in the application inside the sandbox to enable the application to acquire the dynamic agent object to the set dynamic agent method when the second acquisition data of the terminal device is acquired.
[0072]By dynamic agent method, the virtual device information service set in the sandbox is used to generate the virtual device information service set in the sandbox, and the virtual information is returned to the dynamic agent method;
[0073]The application inside the sand box is obtained by obtaining the virtual information by the dynamic agent method, and the virtual information is convert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com