A kind of data export security detection method and detection system
A security detection and data export technology, applied in the field of data security, can solve problems such as data leakage, and achieve the effect of ensuring security, reducing the risk of leakage, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
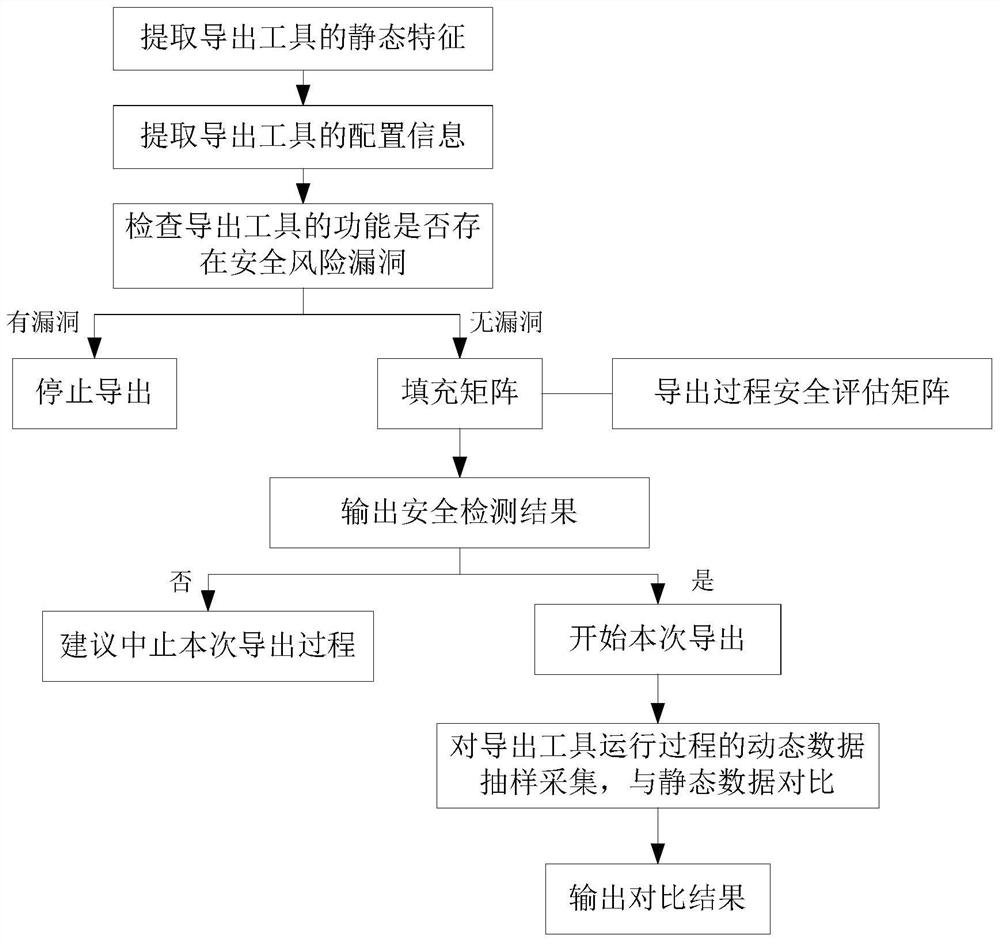
[0063] like figure 1 A data export security detection method is shown, including:
[0064] Extract the static features of the export tool;
[0065] Extract the configuration information of the export tool;
[0066] Check whether the function of the export tool has security risk vulnerabilities: if there is a vulnerability, stop exporting; if there is no vulnerability, go to the next step;
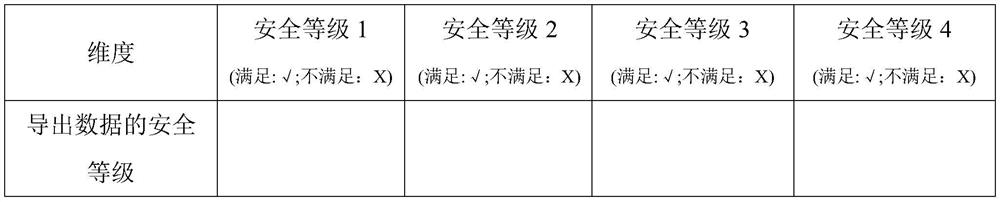
[0067] Populate the derived process safety assessment matrix, and output the safety inspection results based on the populated derived process safety assessment matrix:
[0068] If the output result is no, it is recommended to abort the export process;
[0069] If the output result is yes, the current export is started. During the export process, the dynamic data of the running process of the export tool is sampled and collected, and the sample collection result is compared with the static data of the export tool, and the comparison result is output; the static data includes the static fe...
Embodiment 2
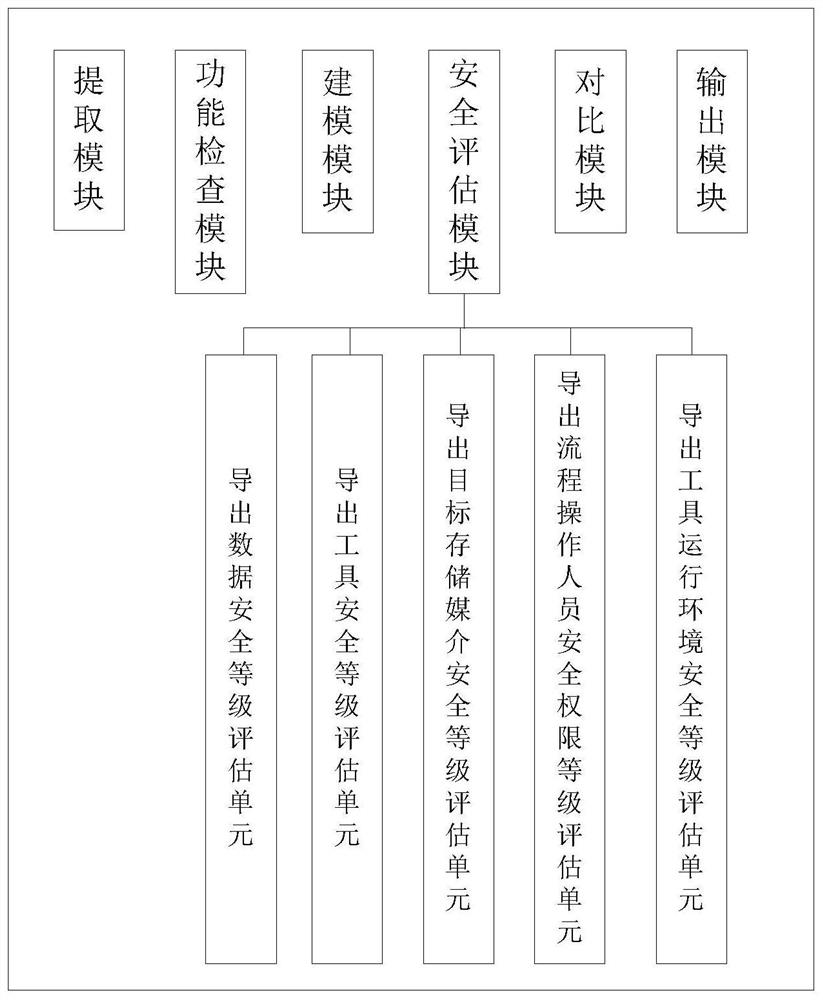
[0124] A data export security detection system, such as figure 2 shown, including:
[0125] The extraction module is used to extract the static features and configuration information of the export tool, and obtain the static data related to the export function;
[0126] The function check module is used to check whether the function of the export tool has security risk vulnerabilities;
[0127] Modeling module for establishing and exporting process safety assessment matrix;
[0128] The security assessment module is used to populate the export process security assessment matrix, and output the security detection result based on the populated export process security assessment matrix; if the output result is no, it is recommended to abort the export process; if the output result is yes, start this time Exporting, sampling and collecting the dynamic data of the running process of the exporting tool in the exporting process, and comparing the sampling and collecting result with ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com