Entity identification method and device, equipment and storage medium
An entity recognition and entity technology, applied in the field of information security, can solve the problems of low accuracy of entity recognition results, long text, unbalanced distribution of data labels, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
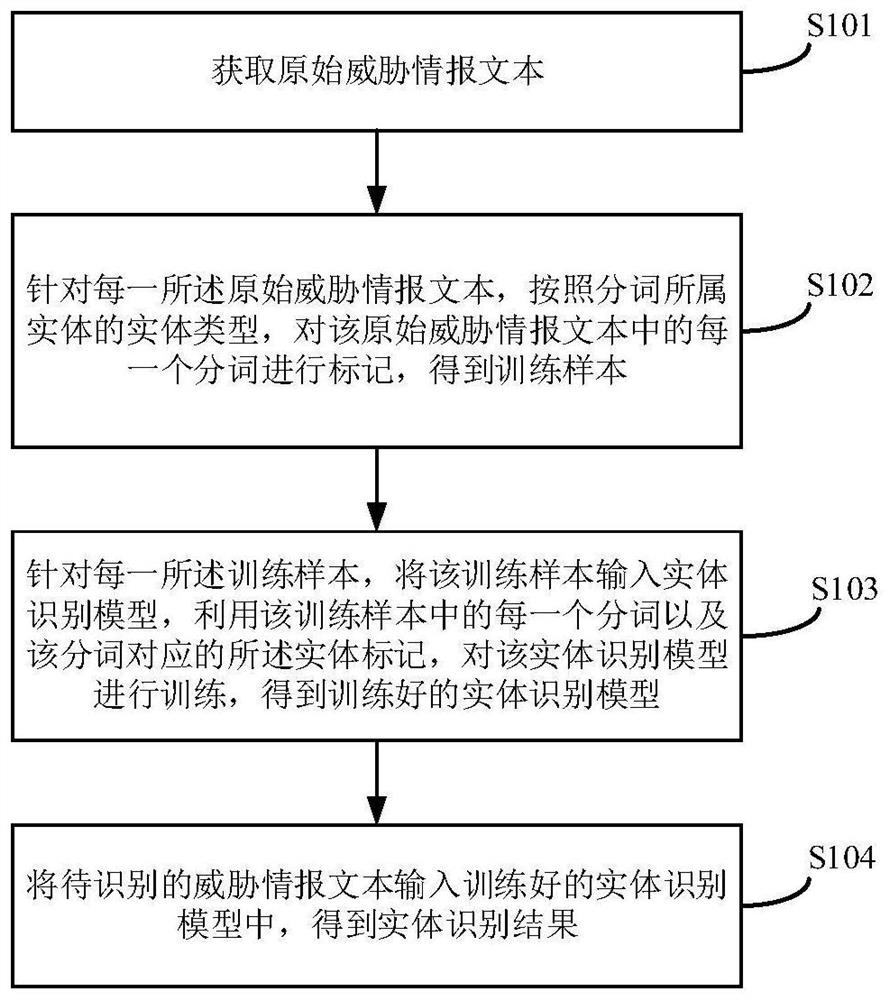
[0110] figure 1 It shows a schematic flowchart of an entity recognition method provided by the embodiment of the present application, wherein the method includes steps S101-S104; specifically:
[0111] S101. Obtain an original threat intelligence text.
[0112] Specifically, the existing entity recognition models are mainly used to identify common types of entities such as person names, place names, and time in ordinary text data. Considering that entities that need to be identified in the threat intelligence field need to involve a large number of specialized vocabulary, and in There is a lack of open source data sets in the threat intelligence field. Therefore, it is necessary to first construct a sample data set for training entity recognition models.
[0113] In this embodiment of the present application, as an optional embodiment, text data such as articles, blogs, and paper reports related to threat intelligence may be crawled from a secure website as the original threa...
Embodiment 2
[0241] Figure 4 A schematic structural diagram of an entity recognition device provided by an embodiment of the present application is shown, and the device includes:
[0242]A data collection module 401, configured to obtain an original threat intelligence text;
[0243] The word segmentation marking module 402 is configured to, for each of the original threat intelligence texts, mark each word segmentation in the original threat intelligence text according to the entity type of the entity to which the segmentation belongs to obtain a training sample, wherein the entity type is at least Including: threat intelligence type and non-threat intelligence type, each word segmentation in the training sample corresponds to an entity tag;
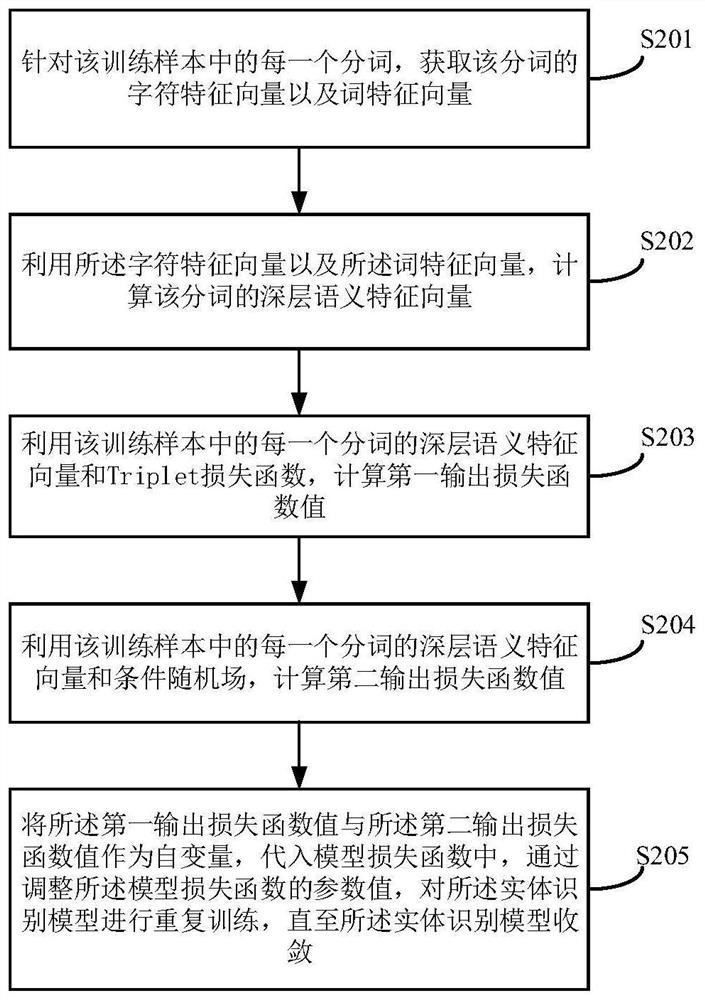
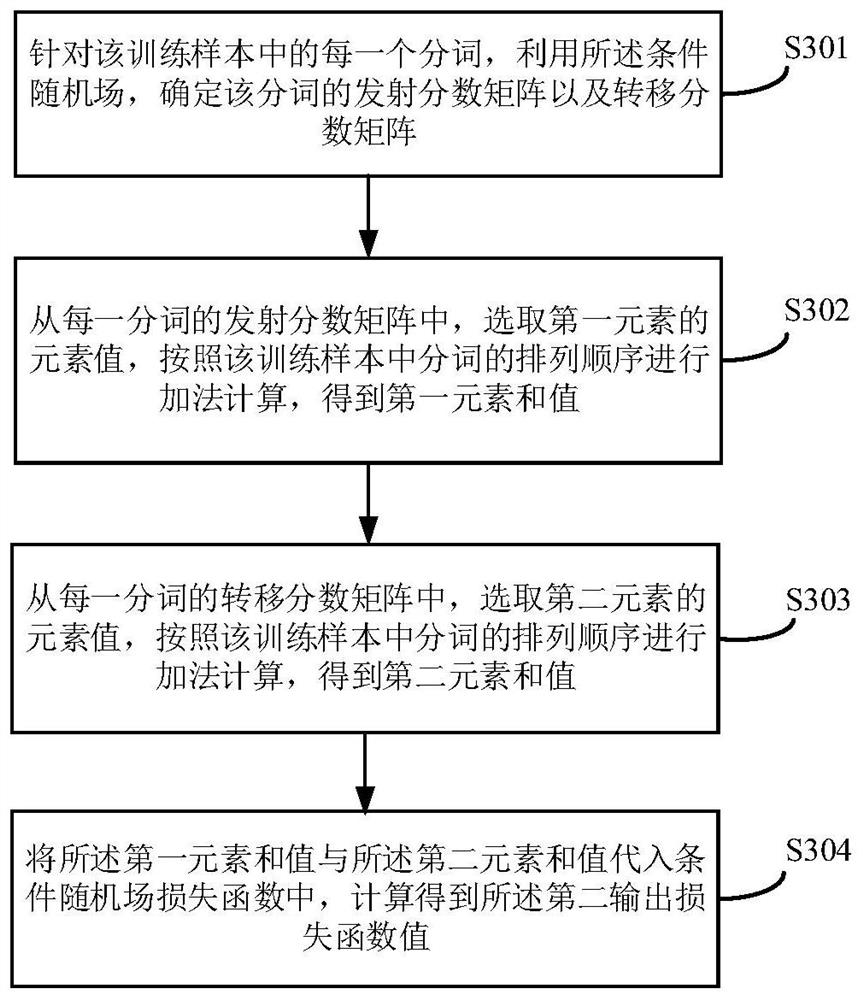
[0244] The model training module 403 is used to input the training sample into the entity recognition model for each training sample, and train the entity recognition model by using each participle in the training sample and the entity tag corres...
Embodiment 3
[0287] Such as Figure 5 As shown, the embodiment of the present application provides a computer device 500 for executing the entity recognition method in the present application, the device includes a memory 501, a processor 502 and a A running computer program, wherein, when the processor 502 executes the computer program, the steps of the above-mentioned entity recognition method are realized.
[0288] Specifically, the above-mentioned memory 501 and processor 502 may be general-purpose memory and processor, which are not specifically limited here. When the processor 502 runs the computer program stored in the memory 501, it can execute the above-mentioned entity recognition method.
[0289] Corresponding to the entity recognition method in this application, the embodiment of this application also provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is run by a processor, the above-mentioned entity recognition is pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com