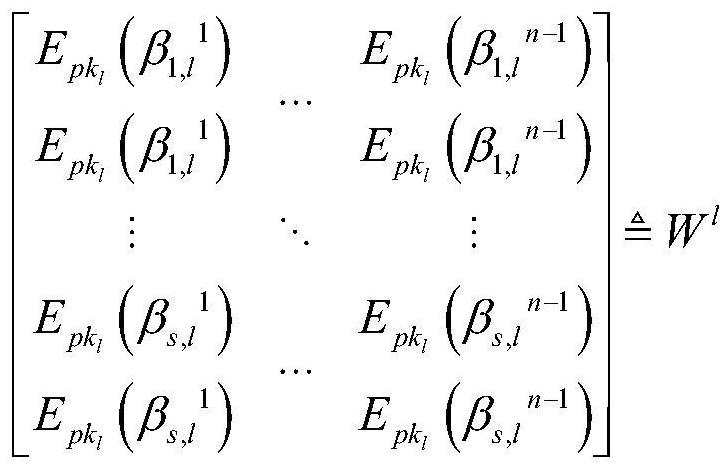Vertical partition data PPARM method based on multi-party set intersection solving
A technology of vertical partitioning and data, applied in the electronic field, can solve the problems of limitations, large amount of communication in the interaction stage, and insufficient privacy protection, and achieve the effect of weakening assumptions and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
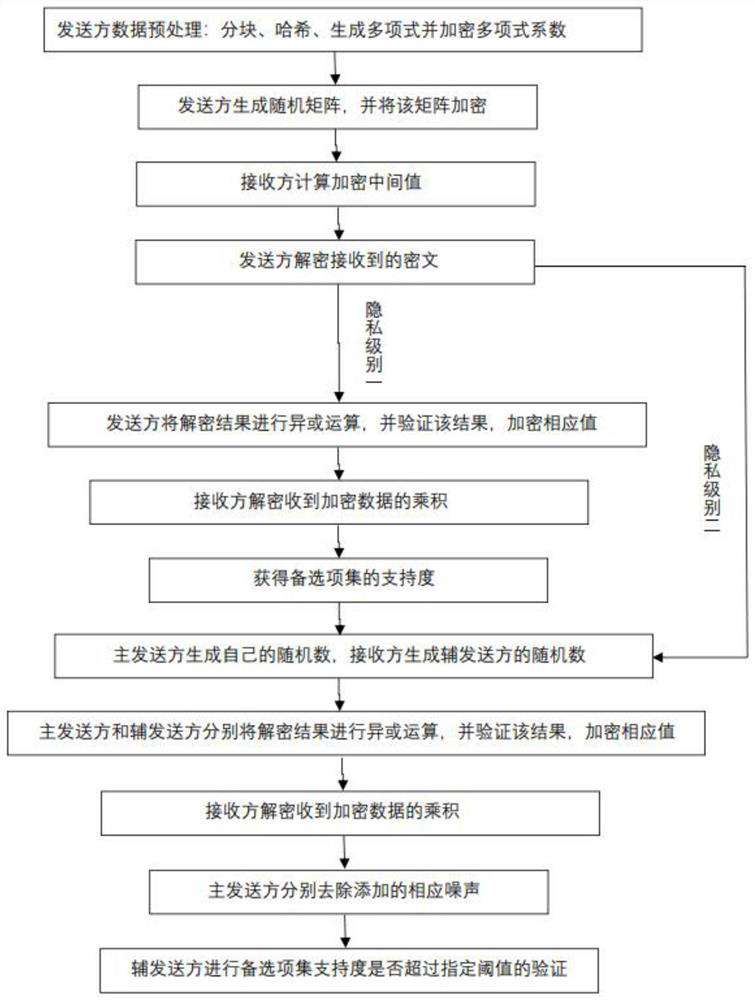
[0056] refer to figure 1 , a kind of vertical partition data PPARM method that the present invention proposes based on multi-party sets to intersect, comprises the following steps:
[0057] Step 1, Party A i Generate an encrypted public-private key pair (pk i ,sk i ) and the hash function H i (·), where i=1,2,...,n represents the participant number, n represents the total number of participants; among n participants, let the first n-1 be the sender A l , the nth one is receiver A n ;Sender A l contains the primary sender A q and secondary sender A n-1 , where q=1,2,...,n-2;
[0058] Step 2, data preprocessing:
[0059] (2.1) For sender A l Input s-dimensional vector data sender A l Use the idea of hash allocation bucket to process the vector data to get the processed data Among them, l=1,2,...,n-1 represents the number of the sender; specifically, it can be obtained as follows:
[0060] (2.1.1) According to the following formula, for each input sender A l Th...
Embodiment 2
[0120] The PPARM method for vertically partitioned data based on the intersection of multi-party sets provided in this embodiment is the same as in Embodiment 1, and its specific implementation steps can also be summarized as follows:
[0121] Step 1, each participant A l Preprocessing your own data is mainly divided into three stages:
[0122] (1) Block stage. According to the following formula, for each sender A l (l=1,2,...,n-1) The input s-dimensional vector is divided into blocks:
[0123]
[0124] in, is sender A l input, F=4r l blocks, where r l by A l Randomly selected, the size is about the average value of the actual items in each transaction set, and there are at most E elements in each block;
[0125] (2) Hash stage. sender A l Use your own hash function H l Hash each element in the divided block;
[0126] (3) Encryption stage. For any block X l (h) , A l produces a polynomial Q of degree E l (h) , then sender A l Use the public key pk of you...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com