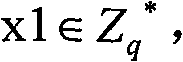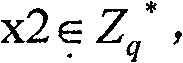Method and device for negotiating group cipher
A group and key technology, applied in the field of communication, can solve the problems of increasing delay, increasing system traffic, increasing algorithm complexity, etc., to achieve the effect of improving real-time performance and reducing traffic
Inactive Publication Date: 2010-11-10
HUAWEI TECH CO LTD +1
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The disadvantages of the above scheme are: the algorithm of key agreement is generated by recursive calling, which increases the complexity of the algorithm; the number of communication rounds of key agreement increases with the number of participants, the above scheme not only increases the delay, but also increases the complexity of the algorithm. It also increases the communication volume of the system
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
Embodiment 2
Embodiment 3
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a method for negotiating group keys and equipment thereof, which belongs to the communication field. In the method, each subscriber in the group generates the same group keys by information interaction with other subscribers based on bilinear pairings mapping of elliptical curve by the method of selecting negotiating group keys according to the parity of total number of subscribers in the group. The equipment can be three types, wherein, one equipment comprises an information interaction module, an intermediate value generating module and a group key generating module;another equipment comprises an information interaction module, an intermediate value generating module, a conversation key generating module, a new intermediate value generating module and a group key generating module; and the third equipment comprises an information interaction module, an intermediate value generating module, a conversation key decoding module and an intermediate value encrypting module. The method and the equipment have small number of communication rounds during the process of key negotiation, thereby improving the immediacy of communication. Furthermore, the rounds number of key negotiation is independent of the number of members, so that the communication volume of the key negotiation is reduced.
Description
Method and device for negotiating a group key technical field The invention relates to the communication field, in particular to a method and device for negotiating a group key. Background technique AdHoc network is a network with multi-hop, self-organization and dynamic topology changes. Nodes move frequently, power reserve is limited, and the trust relationship between nodes and wireless transmission links are relatively fragile. These characteristics make the AdHoc network group The design of the key agreement protocol is very different from the traditional scheme. In an AdHoc network, in order to ensure communication security, it is usually necessary to encrypt messages before transmission. Since the symmetric cryptosystem has advantages in efficiency, the use of group shared keys can greatly reduce the complexity of message processing. At the same time, the AdHoc network is also a dynamic peer-to-peer group, which lacks a fixed trusted third-party support. Therefore,...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/00H04L29/06H04L12/28
CPCH04L9/0833H04L9/3073
Inventor 马春波李建华吴越刘亚
Owner HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com