Honeynet architecture implementation method for cloud plug-in type vulnerability response
An implementation method, a plug-in technology, applied in the direction of electrical components, instruments, platform integrity maintenance, etc., can solve the problems of honeypot information isolation, multiple component responses, and untimely threat intelligence sharing, and achieve the effect of protecting response time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
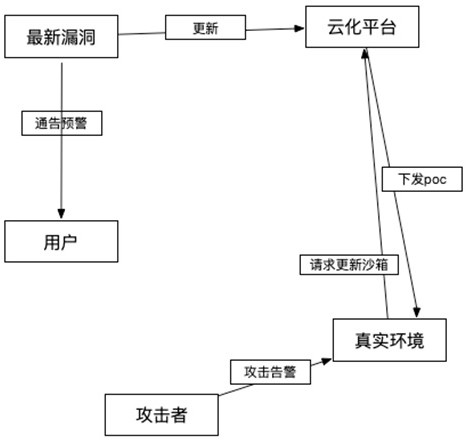
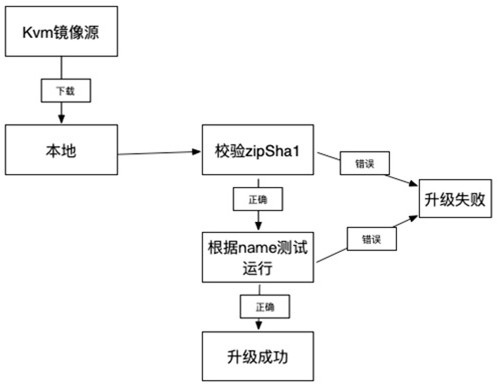
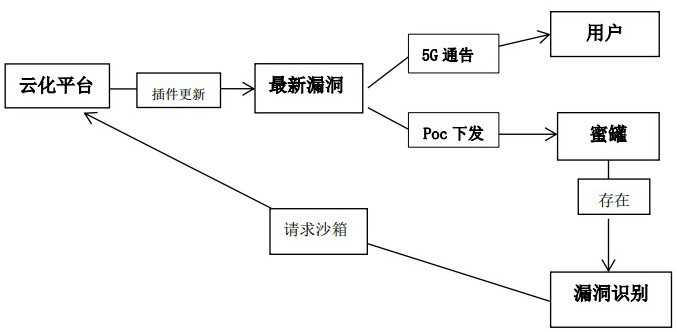
[0025] Such as Figure 1-3 As shown, the present invention provides a method for implementing a cloud-based plug-in vulnerability response honeynet architecture, including:
[0026] Build a cloud-based sandbox management platform to place the simulation sandbox on the cloud. The simulation sandbox simulates the latest vulnerable components through kvm, and quickly updates the simulation sandbox through the identification of vulnerable components in the network to achieve the latest 0day or nday's rapid detection and response;
[0027] A honeypot system is installed on the client side, and the system integrates a vulnerability detection engine. When a vulnerability of the component is detected, it requests the cloud sandbox management platform through the wireless networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com