Mobile application APK file embedded privacy policy extraction method
A technology of mobile application and extraction method, applied in special data processing applications, text database clustering/classification, unstructured text data retrieval, etc. slow speed etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to facilitate the understanding and implementation of the present invention by those of ordinary skill in the art, the present invention will be further described in detail and in-depth below with reference to the accompanying drawings.
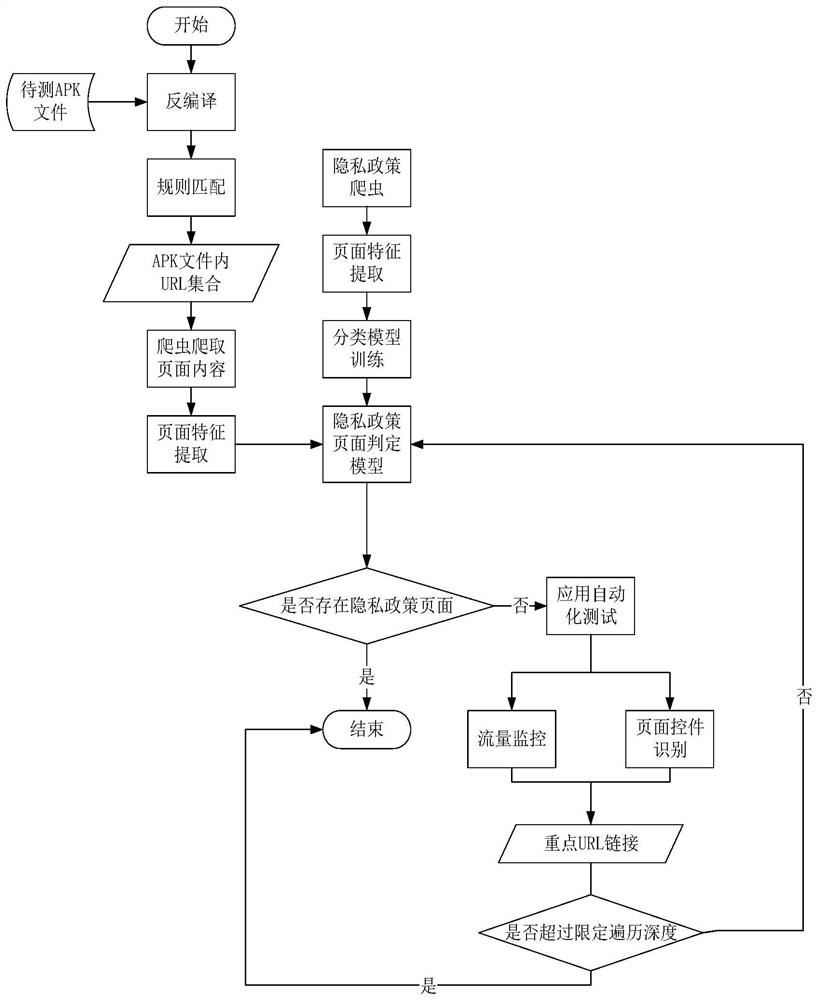
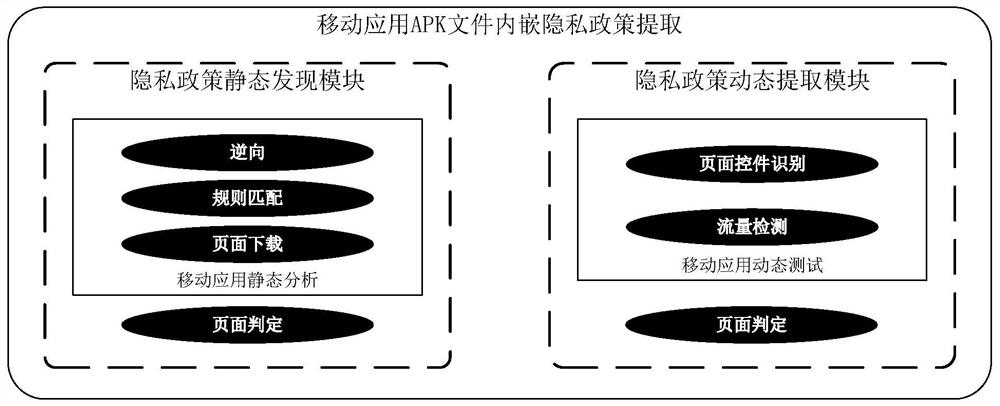
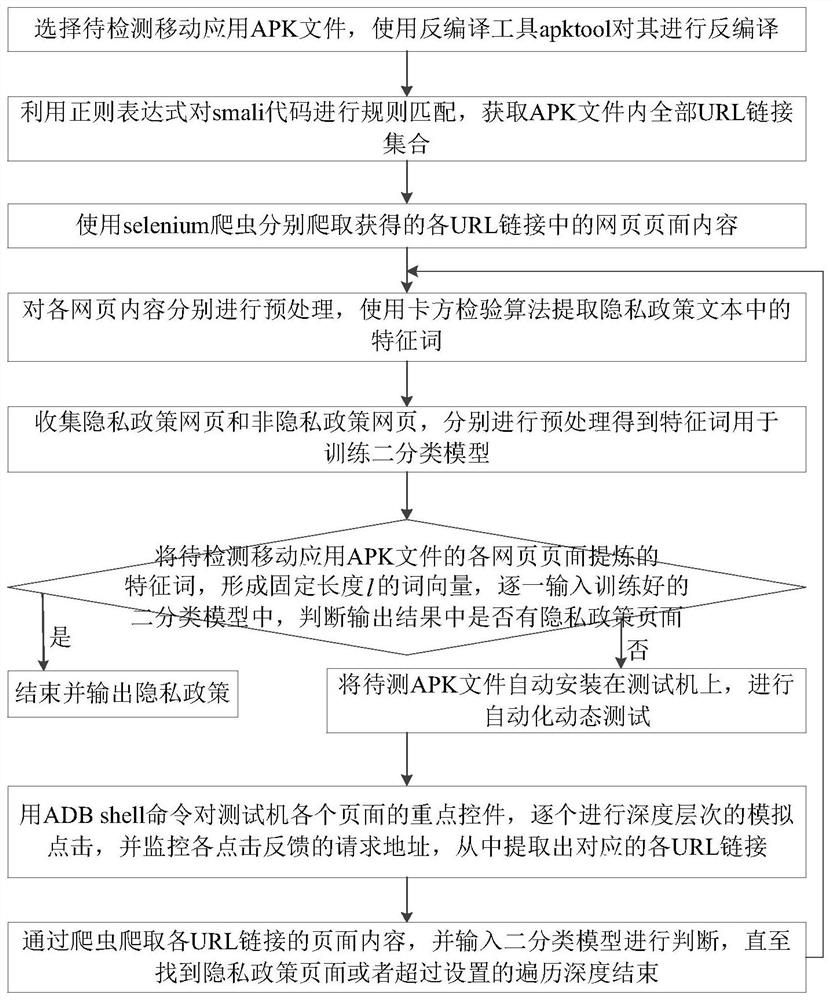
[0046] The present invention is based on the Android application program, utilizes dynamic and static detection of the privacy policy link embedded in the mobile application APK file, and automatically discovers and extracts the privacy policy link contained in the APK file; the overall workflow is as follows: figure 1 As shown: First, statically analyze the APK file of the mobile application to be tested, and obtain all the URL link sets contained in the APK file through decompilation and rule matching; The privacy policy crawler extracts the features of each page and inputs the classification model, and trains the privacy policy page judgment model; judges the extracted features of the obtained pages through the privacy polic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com