Asset management method and device, electronic equipment and medium
An asset management and processor technology, applied in the field of data processing, can solve the problems of inability to quickly determine the server, unsaved switch and server connection relationship, connection relationship preservation and processing, etc., to achieve the effect of reducing risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] The first embodiment provides an asset management method, aiming at the problem of delaying the maintenance process of the switch because the asset management system does not save the connection relationship between the switch and the device in the related art.
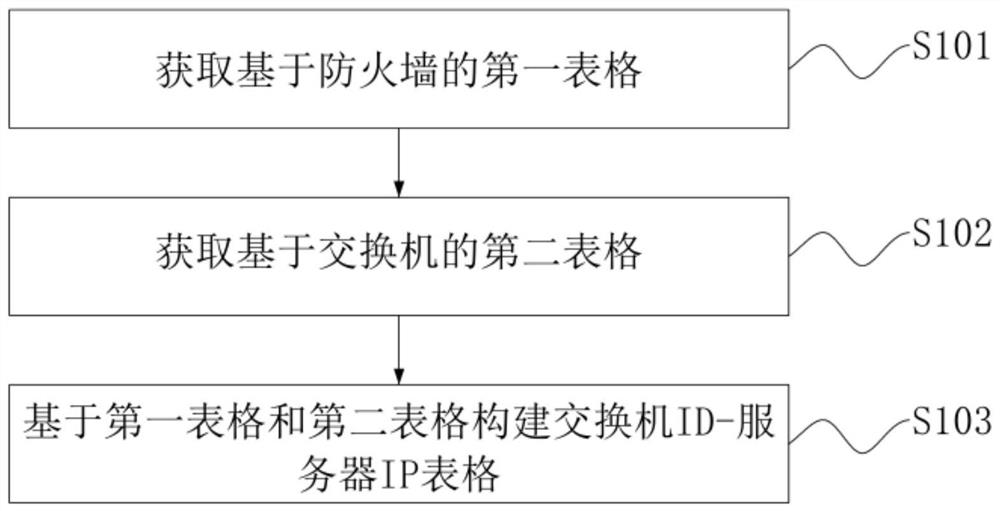
[0047] figure 1 is the flow chart of the asset management method shown in the first embodiment of the present application, refer to figure 1 As shown, the method includes steps S101 to S103.
[0048] Step S101 , acquiring a first table based on the firewall, where the first table includes more than one first entry, and the first entry is associated with a MAC address and a server IP.
[0049] Step S102: Obtain a switch-based second table, where the second table includes more than one second-first entry, and the second-first entry is associated with the MAC address and the switch ID. It can be understood that steps S101 and S102 do not limit the execution order.
[0050] Step S103, constructing a switch ID-se...
Embodiment 2
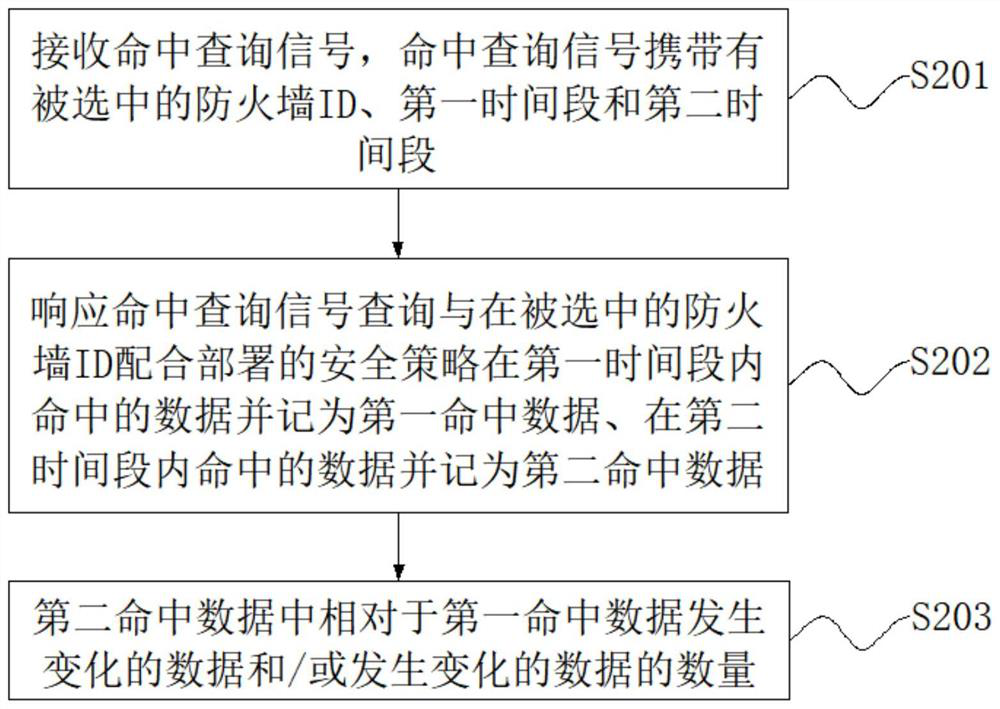
[0078] The second embodiment provides an asset management method, and the second embodiment is performed on the basis of the first embodiment. figure 2 This is a flowchart of the query steps shown in Embodiment 2 of the present application.
[0079] refer to figure 2 As shown, the query step may include steps S201 to S203.
[0080] Step S201: Receive a hit query signal, where the hit query signal carries the selected firewall ID, a first time period and a second time period. It should be noted here that the sender of the hit query signal is not limited here, and the first time period and the second time period may have an intersection or may be independent of each other.
[0081] Step S202, in response to the hit query signal, query the data hit in the first time period by the security policy deployed in conjunction with the selected firewall ID, and denote the first hit data, and the data hit in the second time period and denote the second hit. hit data. The security po...
Embodiment 3
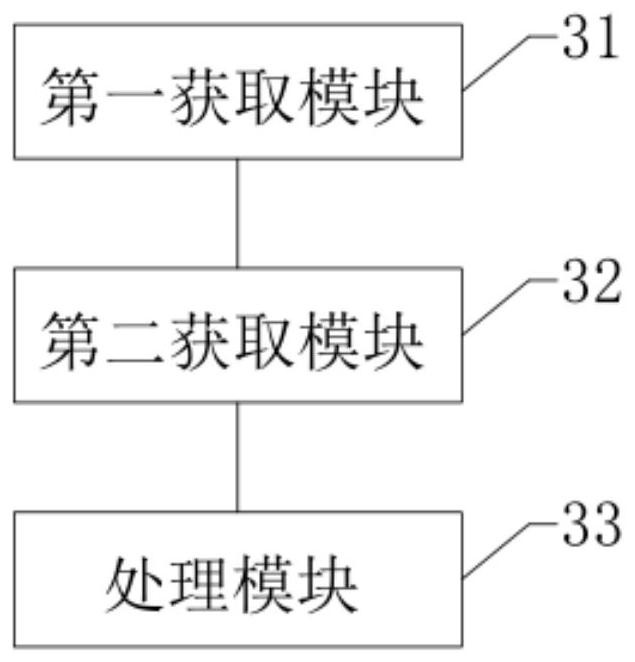
[0093] The third embodiment provides an asset management device, which is the virtual device structure of the foregoing embodiment. image 3 is the structural block diagram of the asset management device shown in the third embodiment of the present application, refer to image 3 As shown, the apparatus includes: a first acquisition module 31 , a second acquisition module 32 , and a processing module 33 .
[0094] The first obtaining module 31 is used to obtain the first table based on the firewall, the first table includes more than one first entry, and the first entry is associated with the MAC address and the server IP;
[0095] The second obtaining module 32 is configured to obtain a switch-based second table, the second table includes more than one second-first entry, and the second-first entry is associated with the MAC address and the switch;
[0096] The processing module 33 is configured to construct a switch ID-server IP table based on the first table and the second ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com