DDoS attack detection method oriented to high-speed network packet sampling data acquisition scene
A high-speed network and sampling data technology, applied in the field of network security, can solve problems such as reduced resource stability and complex calculations in memory space, achieving low time complexity, low space complexity, and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
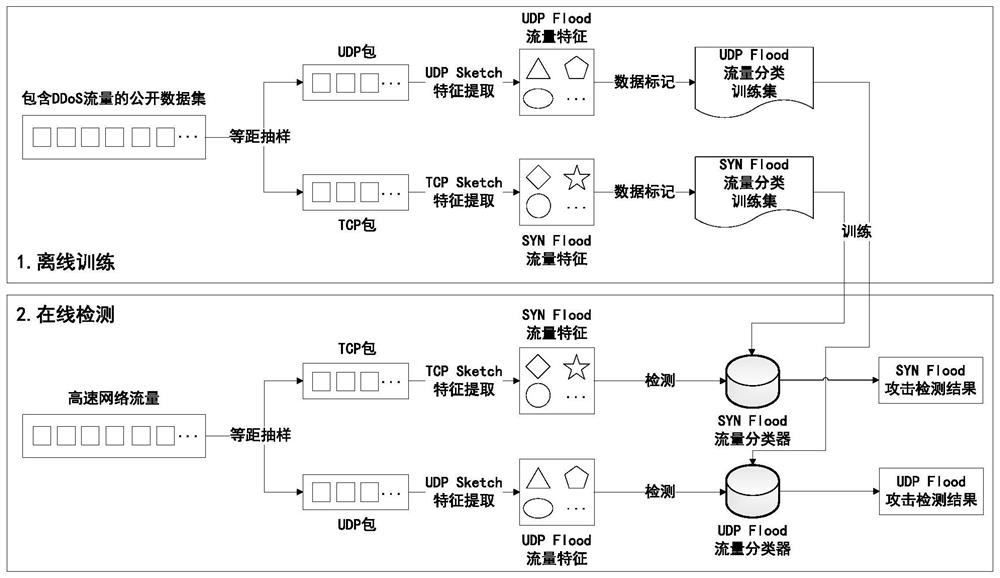
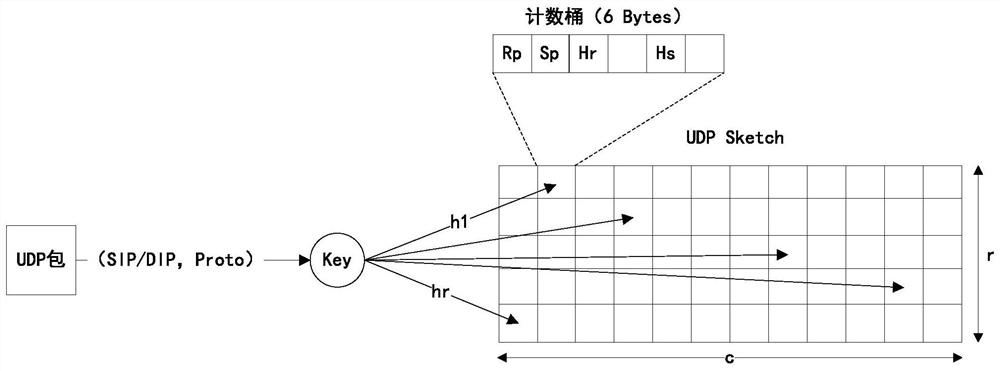
[0069] Specific embodiments: the DDoS detection method based on the improved Count-Min Sketch provided by the present invention can detect common DDoS attacks UDP Flood and SYN Flood in a high-speed network environment, and its process framework is as attached figure 1 As shown, the following will introduce the detection steps of UDP Flood and SYN Flood respectively.
[0070] The detection of UDP Flood includes the following steps:
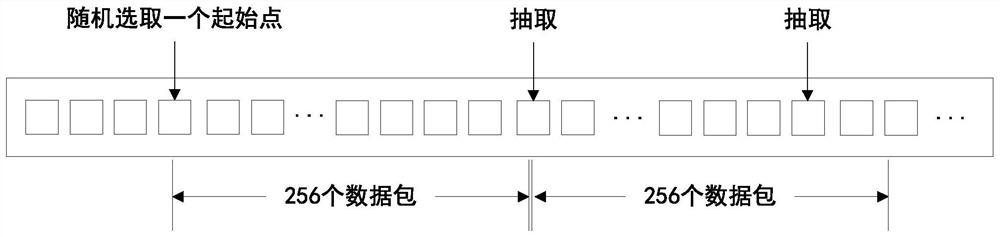
[0071] (1) Obtain a public traffic data set containing UDP Flood traffic, including traffic collected in two different time periods. The first part of the traffic collection time is earlier than the second part of the traffic. Both parts of the traffic contain common DDoS attack UDPFlood traffic and normal traffic;
[0072] In one embodiment of the present invention, the public data set CIC-DDoS2019 containing UDP Flood traffic collected by UIB University on January 12, 2018 and March 11, 2018 is obtained, and the data collected on January 12, 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com