Intelligent terminal control system based on trusted security environment
A smart terminal and security environment technology, applied in the field of information security, can solve problems such as attacks, data confidentiality in the cloud, integrity and service availability threats, data storage, use, deletion and reuse, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The technical solution of the present invention will be described in detail below in combination with the embodiments and the accompanying drawings.
[0037] Taking the application of the present invention to a smartphone as an example, the details of the present invention will be described.
[0038] S1. Ensure the security of mobile terminals
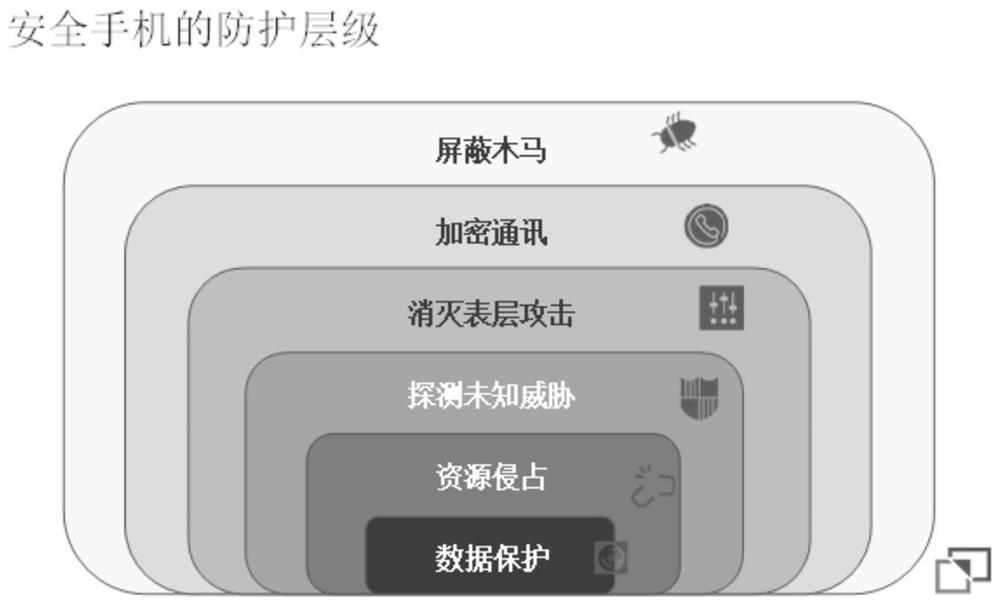
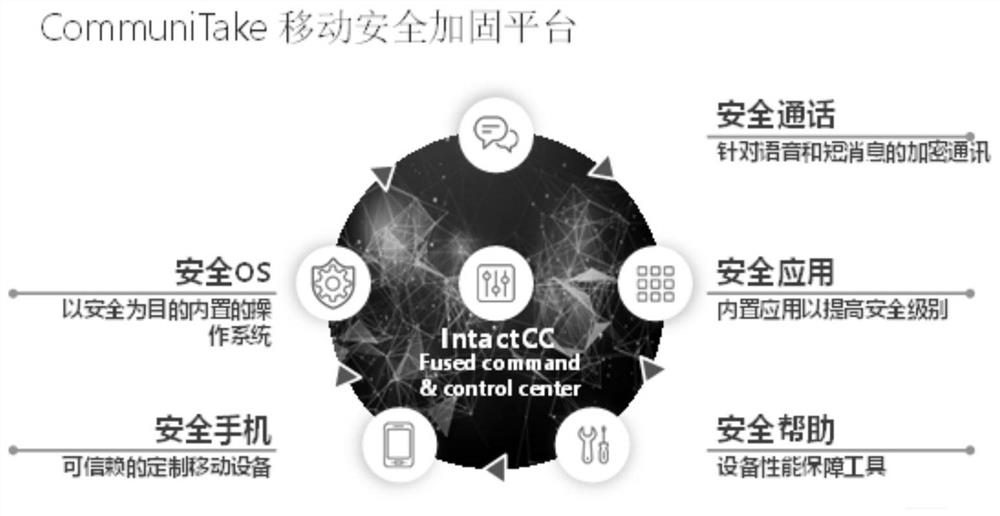
[0039] Such as figure 1 As shown, the protection levels of a secure mobile phone include shielding Trojan horses, encrypting communication, eliminating surface attacks, detecting unknown threats, resource intrusion, and data protection. In addition, the mobile phone-based security architecture includes such figure 2 Secure OS, Secure Phone, Secure Call, Secure App, and Secure Help shown. Therefore, the security environment developed by the present invention is a comprehensive protection scheme based on software design, which is defined as DOOV-OS. It ensures the security of mobile terminals through a series of protection me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com