Key processing system
A processing system and key management center technology, applied in the field of key processing systems, can solve problems such as poor key processing, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
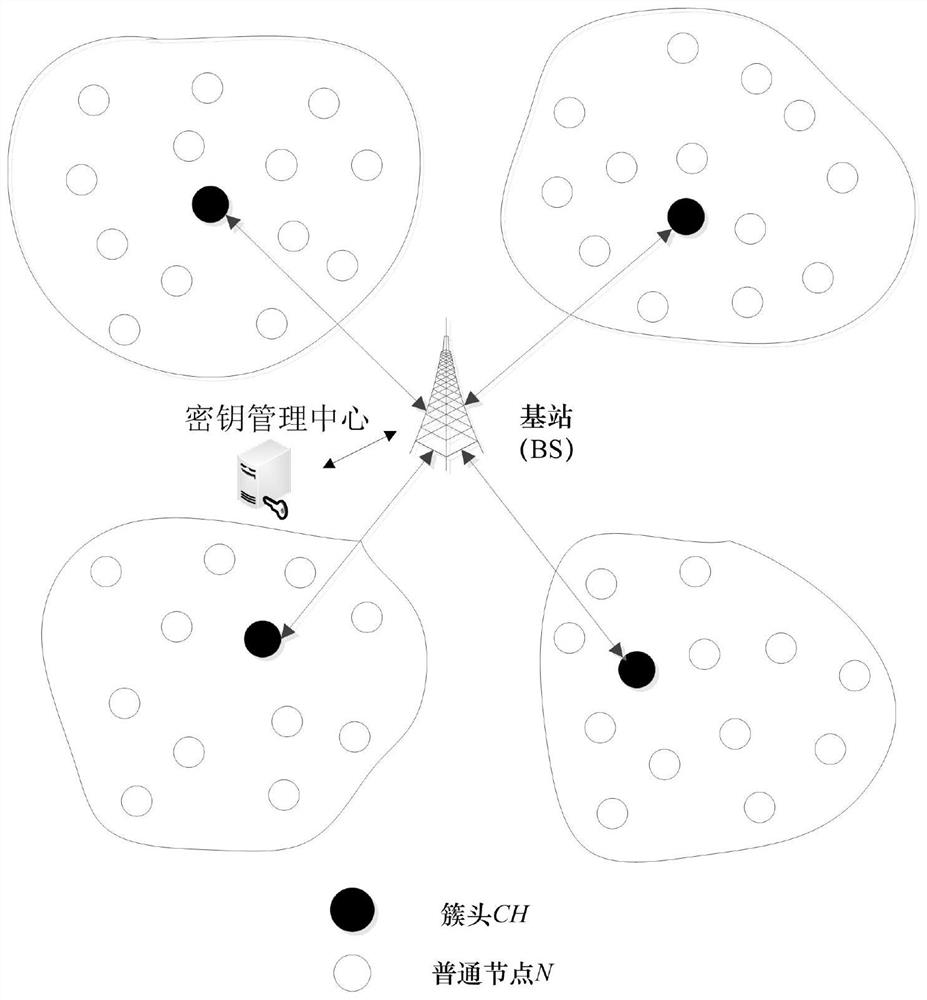
[0056] Such as figure 1 As shown, it is a schematic structural diagram of a key processing system model provided by one or more embodiments of this specification. The key processing system in this embodiment is a network of structural components based on hierarchical routing. The network model mainly It includes a key management center, a base station (BS), a cluster head node (CH) and an intra-cluster node (N) in the same cluster as the cluster head node. in:
[0057] The key processing system processes the key under the following assumptions:
[0058] After the cluster head node and the nodes in the cluster are captured, the identity information, key information and data of the captured nodes will be leaked. Each node has its own unique identification (ID). The base station is honest and reliable, and will not be captured. The base station has powerful computing power and huge storage space, and has a continuous power supply for it, so there is no need to worry about its ...
Embodiment 2
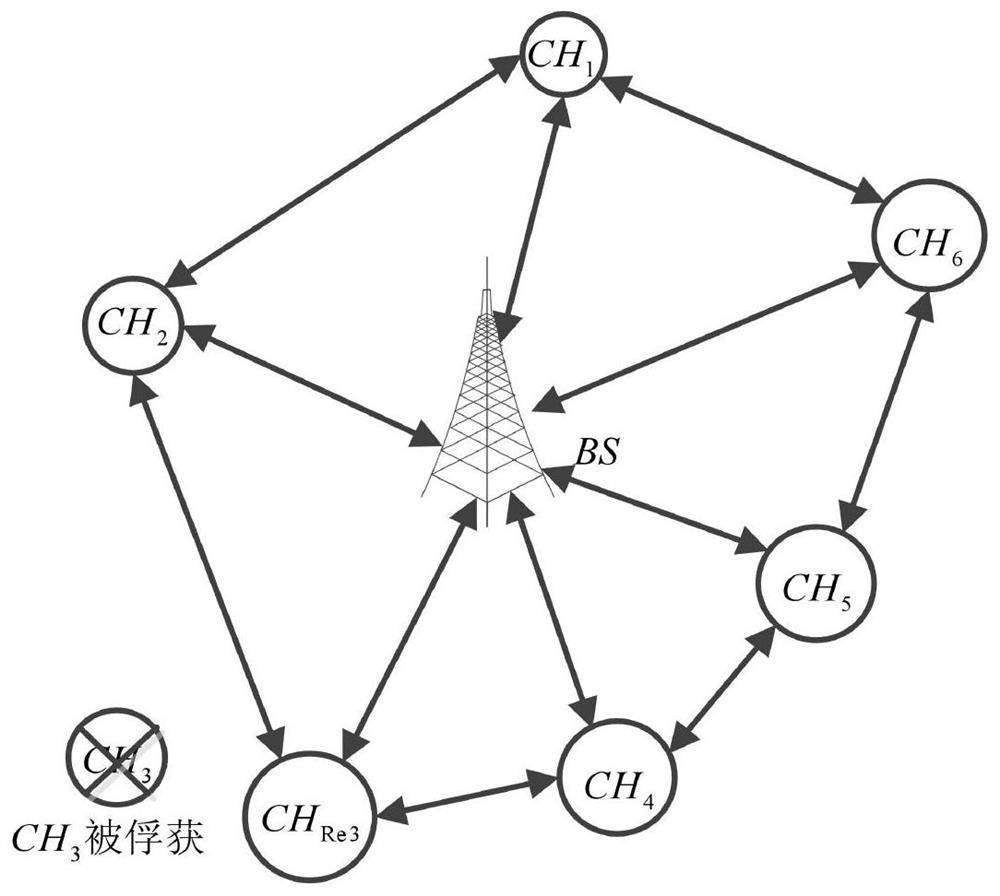
[0104] As an optimization or supplement to the key processing system provided in the foregoing embodiments, one or more embodiments of this specification further provide another key processing system. details as follows:
[0105] In this embodiment, a cluster head node is taken as an example for illustration, and the first communication key between all cluster head nodes and the base station is the same. The key processing system encrypts and decrypts the first communication key and the second communication key based on the public-private key pair of the base station or the cluster head node and the elliptic curve cryptosystem, and the cluster head node obtains the key after the decryption is completed. The first communication key and the second communication key, in this process, the cluster head node and the base station are completed in an interactive way, specifically for the following operations:
[0106] The cluster head node needs to send a configuration request for th...
Embodiment 3
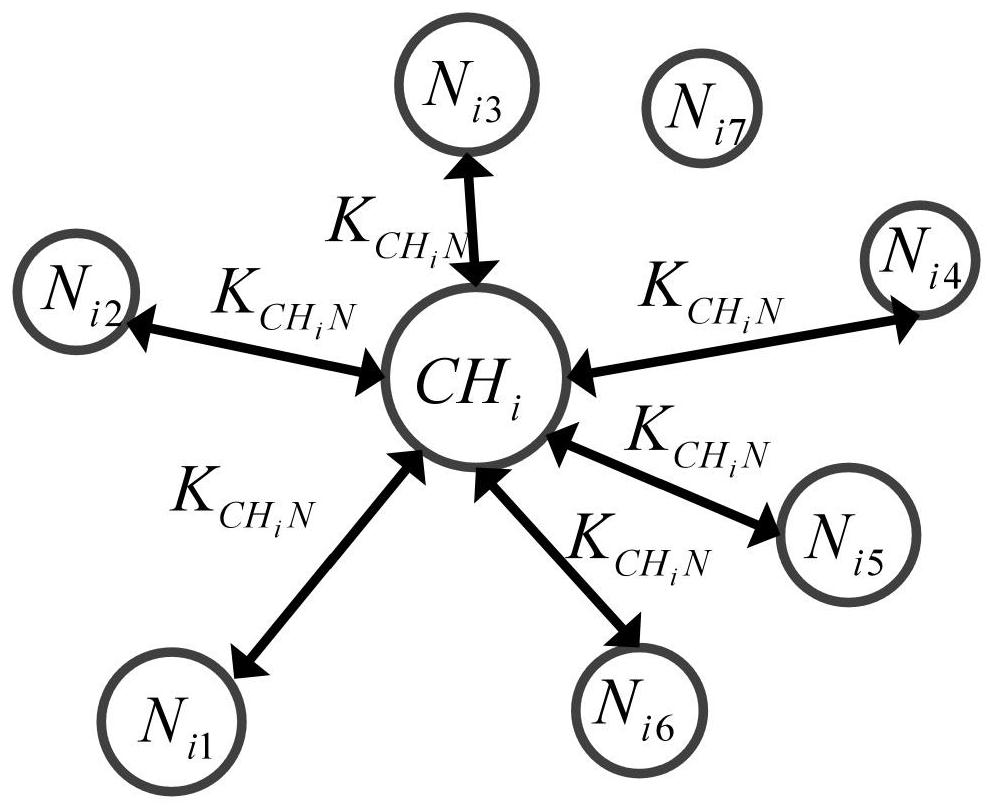
[0139] The cluster head node is further configured to send the second communication key to the nodes in the cluster, and the nodes in the cluster obtain the second communication key. In this process, the cluster head node and the corresponding intra-cluster nodes are carried out in an interactive manner, as follows:
[0140] The node in the cluster is used to select the cluster head node corresponding to it, and send the second configuration message corresponding to the configuration request of the second communication key to the cluster head node corresponding to it, the second configuration message includes the identification of the node in the cluster and, The third digital signature based on elliptic curve encryption is performed on the configuration request with the time stamp with the private key of the node in the cluster. The nodes in the cluster pack their identification and the third digital signature into a second configuration message and send it to the correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com