Trusted review system for protecting service privacy and computer storage medium
A technology for reviewing systems and business information, applied in the field of blockchain, it can solve problems such as review fraud and privacy leakage, and achieve the effect of avoiding fraud and privacy leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
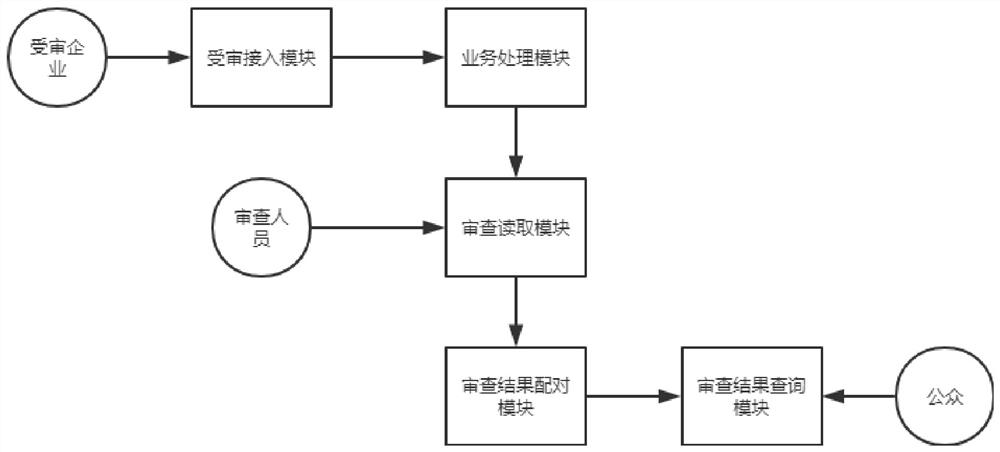
[0032] combined with Figure 1-5 , this embodiment provides a credible review system that protects business privacy, see figure 1 , including an audited access module, an audited reading module, an audited result query module, a business processing module, and an audited result pairing module. The module separates the input business from enterprise to business, and sends the separated pure business information to the review queue, and the review reading module obtains the pure business information from the review queue for credibility review, and the review result The matching module matches the credibility results of the pure business with the affiliated enterprises and records them in the blockchain, and the review result query module queries the credibility results of the corresponding enterprises through the blockchain;
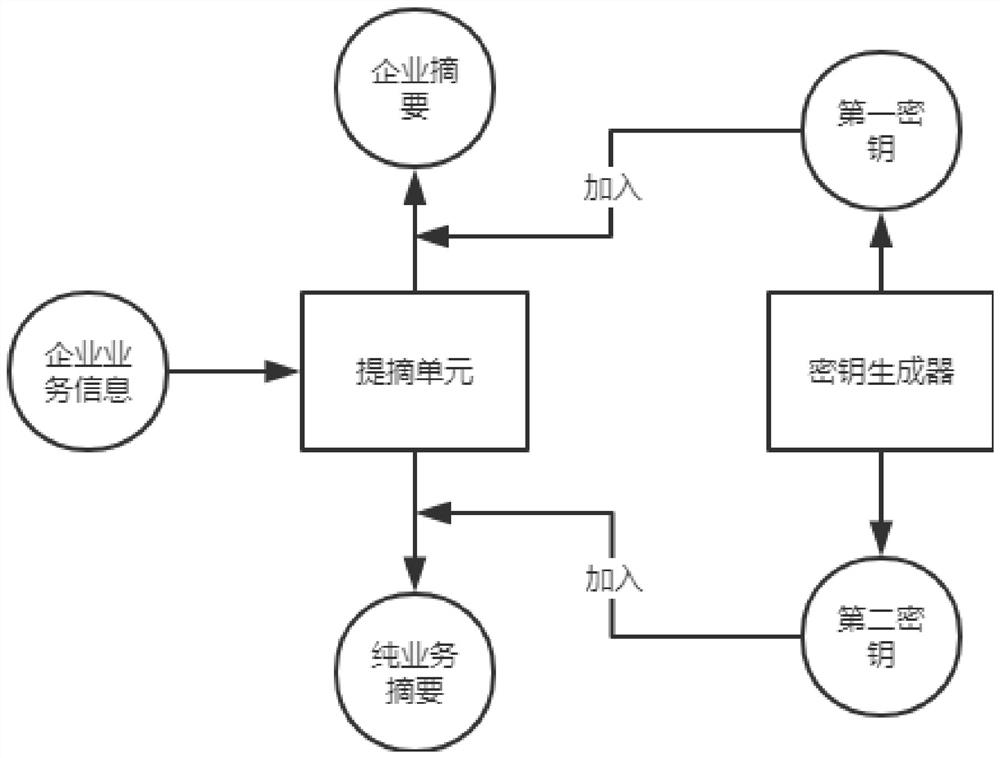
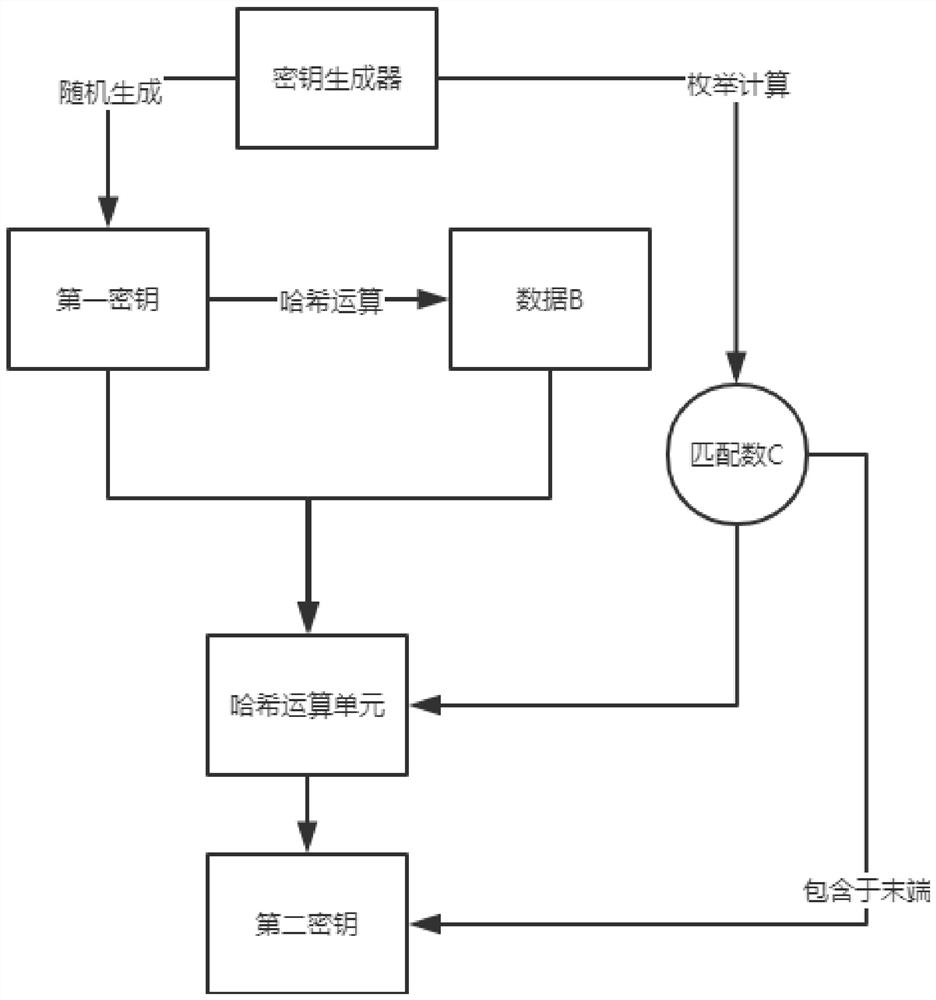
[0033] continue to see figure 2 , the business processing module includes an extraction unit and a key generator, the extraction unit extracts an ente...
Embodiment 2
[0048] Continuing with the accompanying drawings, this embodiment provides a credible review system that protects business privacy, see figure 1 , including an audited access module, an audited reading module, an audited result query module, a business processing module, and an audited result pairing module. The module separates the input business from enterprise to business, and sends the separated pure business information to the review queue, and the review reading module obtains the pure business information from the review queue for credibility review, and the review result The matching module matches the credibility results of the pure business with the affiliated enterprises and records them in the blockchain, and the review result query module queries the credibility results of the corresponding enterprises through the blockchain;
[0049] continue to see figure 2 , the business processing module includes an extraction unit and a key generator, the extraction unit ex...
Embodiment 3
[0071] Continuing with the accompanying drawings, this embodiment provides a credible review system that protects business privacy, see figure 1 , including an audited access module, an audited reading module, an audited result query module, a business processing module, and an audited result pairing module. The module separates the input business from enterprise to business, and sends the separated pure business information to the review queue, and the review reading module obtains the pure business information from the review queue for credibility review, and the review result The matching module matches the credibility results of the pure business with the affiliated enterprises and records them in the blockchain, and the review result query module queries the credibility results of the corresponding enterprises through the blockchain;
[0072] continue to see figure 2 , the business processing module includes an extraction unit and a key generator, the extraction unit ex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com