Method for preventing honeypot from being controlled to become jump server based on virtual switching
A technology of virtual switching and switching, applied in the field of network security, can solve problems such as violation and intrusion, and achieve the effect of avoiding false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the embodiments.
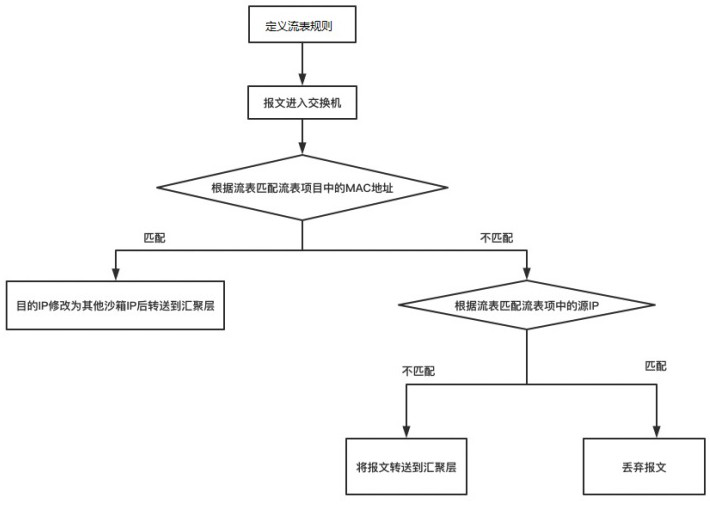
[0021] The invention discloses a virtual exchange-based method for preventing a honeypot from being charged as a springboard machine, comprising the following steps:
[0022] Step 1: The SDN controller interacts with the Openvswitch through the OpenFlow protocol, and defines flow entry rules according to flow entry and exit rules.
[0023] In this step, the SDN controller interacts with the OpenvSwitch switch based on the OpenFlow protocol, and defines its flow entry rules according to the flow entry and exit rules. The entry and exit rules of the flow in this solution are to prohibit the honeypot from initiating external requests, that is, the data packets sent by the honeypot to the outside world Both are discarded, but the honeypot is allowed to send packets to the honeypot management system, while ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com