Ciphertext covariance matrix calculation method based on row coding
A technology of covariance matrix and calculation method, which is applied in calculation, computer security devices, complex mathematical operations, etc., can solve problems such as utilization and data exposure, and achieve the effect of ensuring privacy security and providing security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
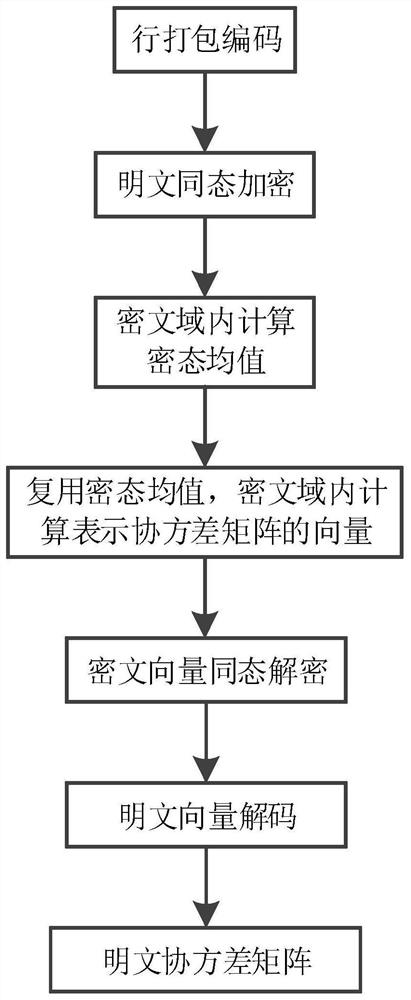
[0032] refer to figure 1 As shown, the invention discloses a method for calculating a ciphertext covariance matrix based on row coding.
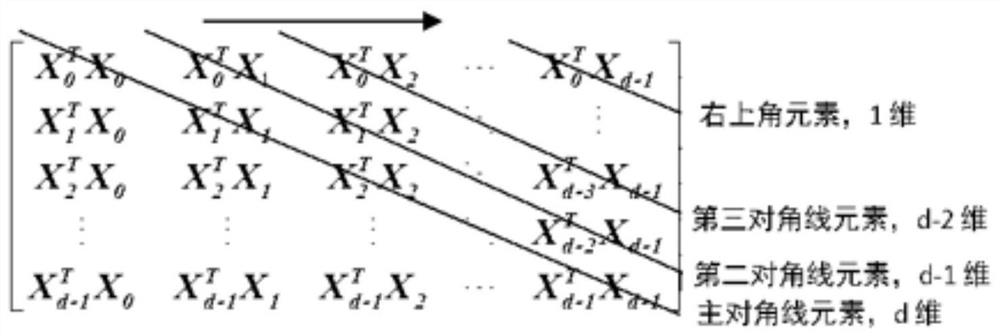
[0033] Let the data matrix X∈R n×d , containing n samples, each sample has d-dimensional features, x i,j Represents the j-th feature in the i-th sample.
[0034] in,
[0035] Covariance is generally used to describe the similarity between two random variables. To calculate the covariance matrix, each column of the data matrix X is regarded as a variable, and the covariance matrix is used to describe the similar relationship between the variables in each column and other variables. In addition, (∑ X ) ij with (∑ x ) ji The meaning of the expression is the same, and the values are also equal.
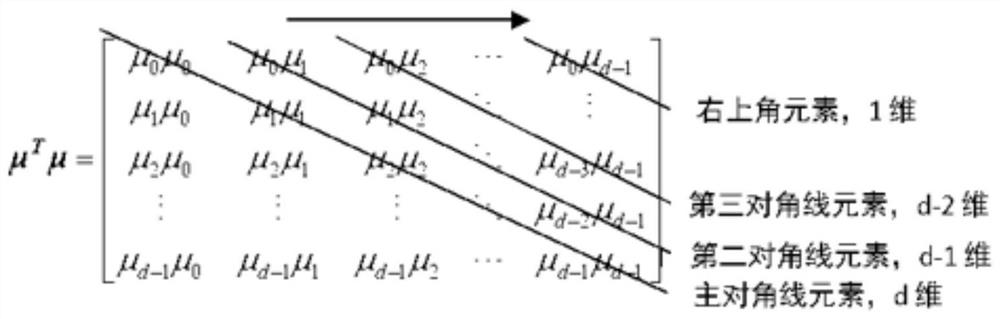
[0036] That is, the covariance matrix ∑ X is a symmetric matrix, and its calculation process is as follows:
[0037] Among them, μ represents the mean vector of the data matrix X, so that μ=[μ 0 ,μ 1 ,…,μ d-1 ], X=[X 0 ,X 1 ,...,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com